Posts From CCME
Sonos appears to have bowed to customer pressure and will now offer security updates for legacy kit and ensure it can co-exist with newer systems. The smart speaker firm issued a statement earlier this week warning that from May, “some
The Information Security Industry is on high alert because of constant cyber threats and trends than ever before in 2020. Artificial intelligence, cryptocurrency, machine learning, sophisticated cyber-attacks, phishing, malware, viruses, bots, have all caused governments, corporations, and individuals to be
Non-removable Android Malware Infects System Process to Remove Pre-Installed Apps & Gain The Root Access
Researchers observed a new variant of Android.Xiny malware with an improved self-defense mechanism. The malware targets only the older versions of the Android devices and gains the complete root access of the vulnerable Android device. It infects Android device version
National Institute of Standard and Technology (NIST) released a Privacy framework for 2020 to improving privacy through enterprise risk management. NIST Privacy Framework is a voluntary tool developed in collaboration with stakeholders intended to help organizations identify and manage privacy
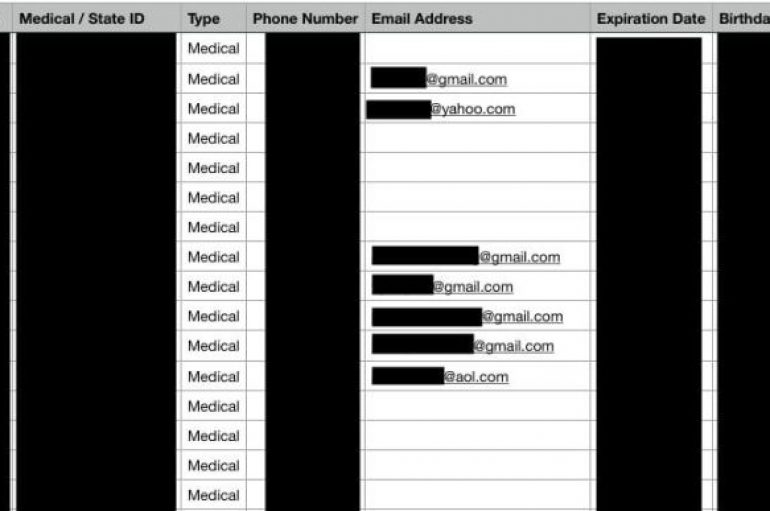
Experts found online an unsecured database owned by THSuite and used by point-of-sale systems in medical and recreational marijuana dispensaries. Data leak continues to be a frequent issue suffered by companies, news of the day is the discovery of an unsecured
US Cybersecurity Agency Issues Emotet Warning
America’s Cybersecurity and Infrastructure Security Agency (CISA) issued a warning yesterday after observing an increase in the number of targeted cyber-attacks that utilize Emotet. Emotet functions as a modular botnet that can steal data, send malicious emails, and act as
Albany County in the state of New York has been struck by two separate cyber-attacks in three weeks. A five-figure ransom in Bitcoin was paid by Albany County Airport Authority (ACAA) earlier this month after their servers became infected with
An annual report into the virulence of phishing scams has found that more than half of organizations dealt with at least one successful phishing attack in 2019. The 2020 “State of the Phish” report, by cybersecurity and compliance firm Proofpoint,
Thousands of WordPress sites have been infected with malicious JavaScript in an attempt to promote scam websites, according to Sucuri. The number of infections spiked last week, with hackers exploiting vulnerabilities in various plugins, including Simple Fields and the CP
Tens of thousands of cannabis users in the US have had their personal information leaked by a misconfigured cloud bucket, according to researchers. Over 85,000 files including more than 30,000 records with sensitive personally identifiable information (PII) were exposed when
Researchers from Microsoft discovered a new version of PowerShell Based Malware sLoad 2.0 that using Background Intelligent Transfer Service (BITS) for malicious activities to attack Windows systems. Microsoft called this new version as “Starslord” based on strings in the malware
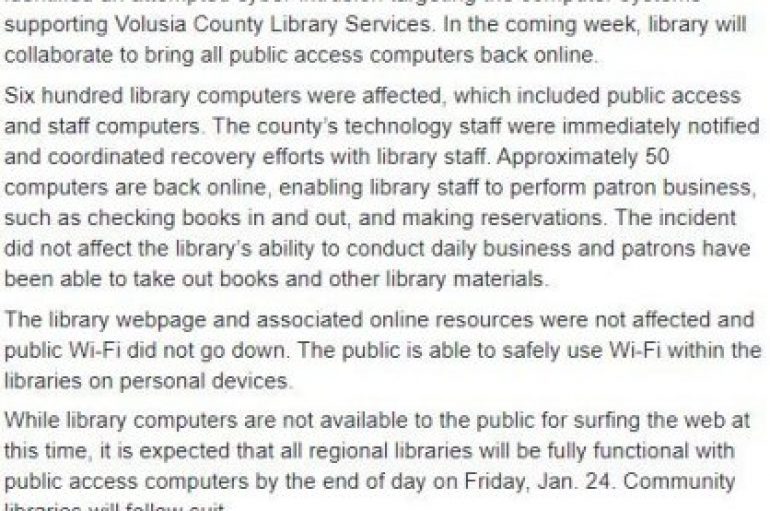
System supporting libraries in Volusia County were hit by a cyber attack, the incident took down 600 computers at Volusia County Public Library (VCPL) branches. 600 staff and public access computers were taken down at Volusia County Public Library (VCPL)
Fake Smart Factory Captures Real Cyber-Threats
A fake industrial prototyping company created by cybersecurity researchers has become the target of real-life cyber-attackers. Researchers at Trend Micro established the faux firm and maintained it for a six-month period in 2019 to learn about the threats facing companies
The UK government is planning to police social media by issuing sites with a new code of conduct. Social media firms will be required by law to protect children from viewing any content deemed to be “detrimental to their physical
Apple dropped plans to offer end-to-end encrypted cloud back-ups to its global customer base after the FBI complained, a new report has claimed. Citing six sources “familiar with the matter,” Reuters claimed that Apple changed its mind over the plans
Lack of penetration testing, A recent study found that 33% of businesses have lost customers because of a breach. Not only will this kind of security incident further add to the costs of the potential damages, but it can also