A New Variant of Asruex Trojan Exploits Very Old Office, Adobe Flaws
Experts at Trend Micro discovered a new variant of the Asruex Trojan that exploits old Microsoft Office and Adobe vulnerabilities to infect systems.
Malware researchers at Trend Micro discovered a new variant of the Asruex Trojan that exploits old Microsoft Office and Adobe vulnerabilities to infect Windows and Mac systems.
Asruex first appeared in the threat landscape 2015, researchers linked it to the spyware used by the DarkHotel APT group.
“However, when we encountered Asruex in a PDF file, we found that a variant of the malware can also act as an infector particularly through the use of old vulnerabilities CVE-2012-0158 and CVE-2010-2883, which inject code in Word and PDF files respectively.” reads the report published by Trend Micro.
CVE-2012-0158 is a critical remote code execution (RCE) vulnerability that affected Microsoft Office.
CVE-2010-2883 is a stack buffer overflow flaw that could be exploited by attackers to execute arbitrary code or trigger a denial of service condition.
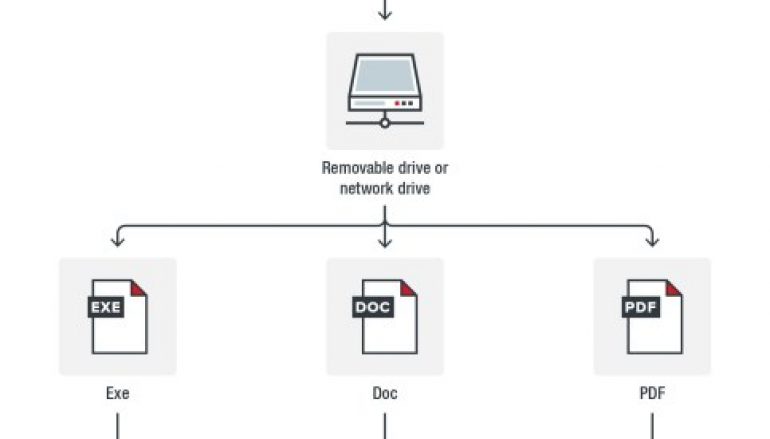
The attack chain leverages a shortcut file that has a PowerShell download script, and spreads through removable drives and network drives.

The use of exploits for well-known vulnerabilities that have been already patched suggests that attackers aims at infect specific targets who have been using older versions of Adobe Reader (versions 9.x up to before 9.4) and Acrobat (versions 8.x up to before 8.2.5) on Windows and Mac OS X.
Because of this unique infection capability, security researchers might not consider checking files for an Asruex infection and continue to watch out for its backdoor abilities exclusively. Awareness of this new infection method could help users defend against the malware variant.
Trend Micro researchers discovered the new Asruex variant in malicious .PDF files that was spread via phishing messages.
Researchers reported that attackers also used weaponized Word files to deliver the Asruex Trojan, in other cases the malicious code is delivered as a standard executable.
“This Asruex variant compresses and encrypts the original executable file or host file and appends it as its .EBSS section. This allows the malware to drop the infector, while also executing the host file like normal.” continues the report.
Once executed on a machine, Asruex will check the following information to determine if it is running in a sandbox environment:
- Computer names and user names
- Exported functions by loaded modules
- File names
- Running processes
- Module version of running process
- Certain strings in disk names
If the systems passes the checks, the backdoor is installed on the system.
“This case is notable for its use of vulnerabilities that have been discovered (and patched) over five years ago, when we’ve been seeing this malware variant in the wild for only a year,” Trend Micro concludes. “This hints that the cybercriminals behind it had devised the variant knowing that users have not yet patched or updated to newer versions of the Adobe Acrobat and Adobe Reader software.”
This post A New Variant of Asruex Trojan Exploits Very Old Office, Adobe Flaws originally appeared on Security Affairs.





