A new Brazilian banking Trojan leverages on PowerShell
According to Kaspersky experts Brazilian crooks have made an important addition to their malware leveraging on the PowerShell.
Security experts from Kaspersky Lab have discovered a sophisticated banking trojan targeting Brazilian users. The threat, codenamed Trojan-Proxy.PowerShell.Agent.a, leverages on the Microsoft’s PowerShell utility. It is considered one of the most complex Brazilian malware samples discovered since now.
The malware was delivered via a phishing campaign, the malicious messages appear as sent from a mobile carrier. Threat actors used a malicious .PIF (Program Information File) attachment to compromise the victims. PIF files instruct MS-DOS applications how to run in Windows environments, they can include executables like BAT, COM or EXE that are automatically executed once the host file is running.
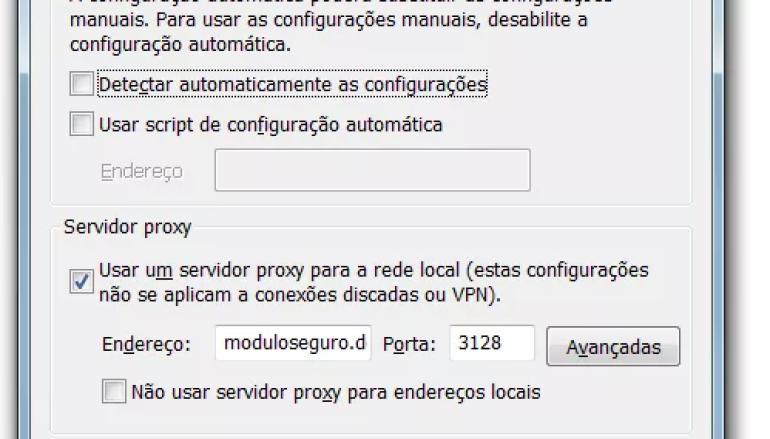
The Trojan-Proxy.PowerShell.Agent.a observed by Kaspersky is able to modify proxy settings in Internet Explorer to hijack users to phishing pages for Brazilian banks.
“After the file is executed it changes the proxy configuration in Internet Explorer to a malicious proxy server that redirects connections to phishing pages for Brazilian banks. It’s the same technique used by malicious PACs that we described in 2013, but this time, no PACs are used; the changes in the system are made using a PowerShell script.” wrote Fabio Assolini.
The malware also works on Firefox and Chrome, it attempts to bypass PowerShell execution policies launching the “powershell.exe” process and the command line “-ExecutionPolicy Bypass -File %TEMP%\599D.tmp\599E.ps1”.
The malware modifies the file prefs.js, changing proxy settings in this way users trying to access bank websites listed in the script they will be redirected to a phishing page hosted on the malicious proxy server.
“The proxy domains used in the attack are listed below. All of them use dynamic DNS services and their goal is to redirect all traffic to a server located in the Netherlands (89.34.99.45), where there are several phishing pages for Brazilian banks:”
gbplugin.[REMOVED].com.br
moduloseguro.[REMOVED].com.br
x0x0.[REMOVED].com.br
X1x1.[REMOVED].com.br
The Brazilian underground is very prolific for banking malware development due to a large inclination of Brazilians in the use of online banking services.
According to Kaspersky Lab, Brazil was the country with the highest number of banking trojan infections in Q1 2016.
Below the mitigation strategy suggested by Kaspersky experts:
“To protect a network against malware that uses PowerShell, it is important to modify its execution, using administrative templates that only allow signed scripts. We are sure this is the first of many that Brazil’s bad guys will code.”
Source | securityaffairs