Archive
A new phishing tactic which targets Verizon customers to steal user credentials, passwords and personal details has been detected. According to research by Armorblox, the email resembles a secure message from Verizon Support and is titled “Your attention is urgently
Configuration errors are the number one threat to cloud security, according to a new poll of IT and security professionals by Check Point. The security vendor interviewed 653 industry professionals to compile its 2020 Cloud Security Report. Three-quarters (75%) claimed
Product complexity and a lack of in-house skills mean many organizations are failing to fully realize the benefits of their cloud access security broker (CASB) solutions, according to the Cloud Security Alliance (CSA). The industry body polled over 200 IT
Open Source Supply Chain Attacks Surge 430%
Security experts are warning of a 430% year-on-year increase in attacks targeting open source components directly in order to covertly infect key software supply chains. There were 929 attacks recorded between July 2019 and May 2020, according to Sonatype’s annual
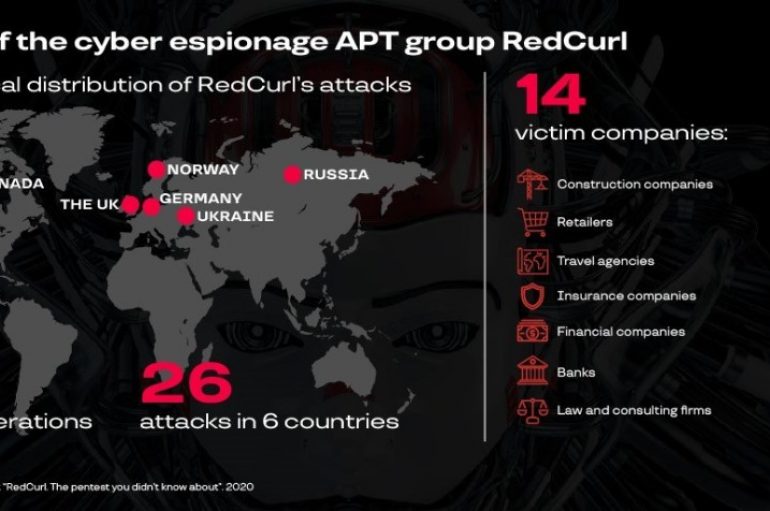
Threat Intel firm Group-IB has released an analytical report on the previously unknown APT group RedCurl, which focuses on corporate espionage Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has released an analytical report on the previously
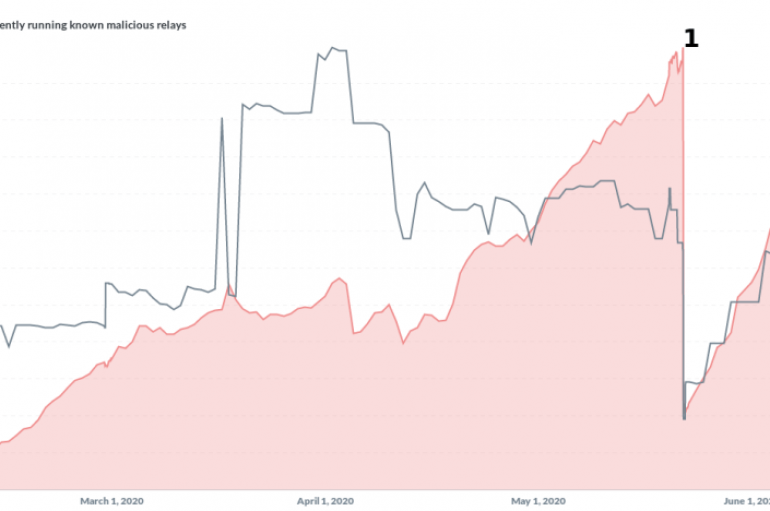
A security researcher has discovered that a threat actor controlled roughly 23% of the Tor network’s exit nodes. A security researcher named Nusenu revealed that in May a malicious controlled roughly 23% of the entire Tor network’s exit nodes. Experts
FireEye Announces Bug Bounty Program
California cybersecurity company FireEye today announced that it is opening up its bug bounty program to the public. FireEye previously set up a private bug bounty program in partnership with Bugcrowd. As of today, the company is extending the program
Pace Center for Girls’ Donor Data Breached
A non-profit social services agency in Florida has been hit by a data breach after a security incident affected one of its outside vendors. Pace Center for Girls has issued a warning to its supporters after the organization discovered some
Experts found new variants of Agent Tesla Trojan that include modules to steal credentials from popular web browsers, VPN software, as well as FTP and email clients. Researchers from SentinelOne discovered new variants of the popular Agent Tesla Trojan that
Only 2% of organizations have run incident response scenarios related to the pandemic response. According to research by Immersive Labs of 402 organizations, nearly 40% are not fully confident in their teams training to handle a data breach if one
Citrix released an update covering multiple vulnerabilities in Citrix Endpoint Management (CEM) also referred to as XenMobile. Chaining the vulnerabilities allows an unauthenticated remote attacker to gain control over the Citrix Endpoint Management (CEM) server. The vulnerabilities can be tracked
Around a third (33%) of UK universities have been targeted with ransomware, freedom of information (FOI) requests submitted by the agency TopLine Comms have revealed. Of the 134 universities the requests were sent to, 105 responded. Of these, 35 (33%)
The SANS Institute has revealed that hundreds of emails from an internal account were forwarded to an unknown third party, compromising 28,000 records of personally identifiable information (PII). The global cybersecurity training and certifications organization said in a statement that
Human Error Threatens Cloud Security
Virtually all security professionals believe that human error could put the security of cloud data at risk, according to new research published today. A survey commissioned by Tripwire and carried out last month by Dimensional Research found that 93% of
It was another big Patch Tuesday this month with over 100 CVEs fixed by Microsoft, including two being actively exploited in the wild. Of the 120 vulnerabilities addressed this month, 17 were rated critical. Experts agreed that system administrators should
Rights groups are celebrating after the Court of Appeal ruled that the use of facial recognition (AFR) technology by South Wales Police is unlawful, although the force may not stop future pilots. The case was brought by Liberty and activist