Archive
What is a VPN? Why Would I Need One
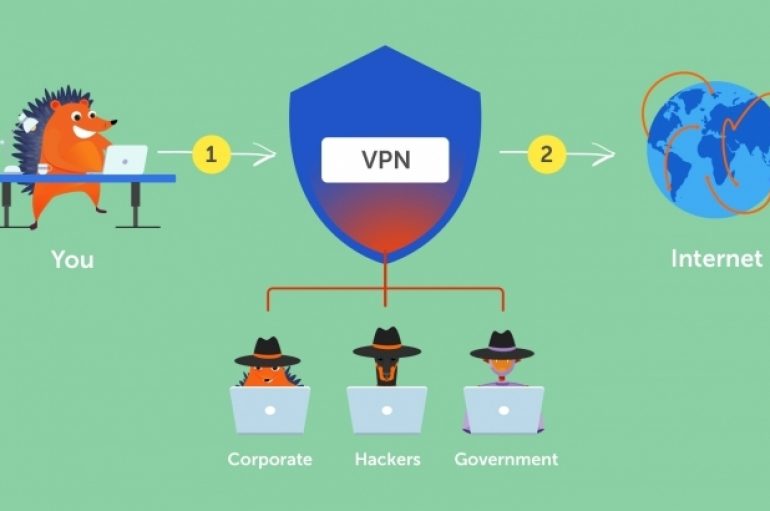
VPN means virtual private network. A VPN connection is an encrypted data connection, and this encryption takes place between the user’s device and the VPN server. All sent and incoming data are redirected via a VPN server to make your
Day after day the number of Coronavirus-themed attacks increases, fraudsters have launched a phishing campaign to deliver keyloggers on users’ PC Experts from IBM X-Force have uncovered a new Coronavirus-themed phishing campaign aimed at delivering keyloggers on users’ PC Threat
A new variant of the infamous Mirai malware, tracked as Mukashi, targets Zyxel network-attached storage (NAS) devices exploiting recently patched CVE-2020-9054 issue. Security experts have discovered a new variant of the infamous Mirai malware, tracked as Mukashi, was employed in attacks against
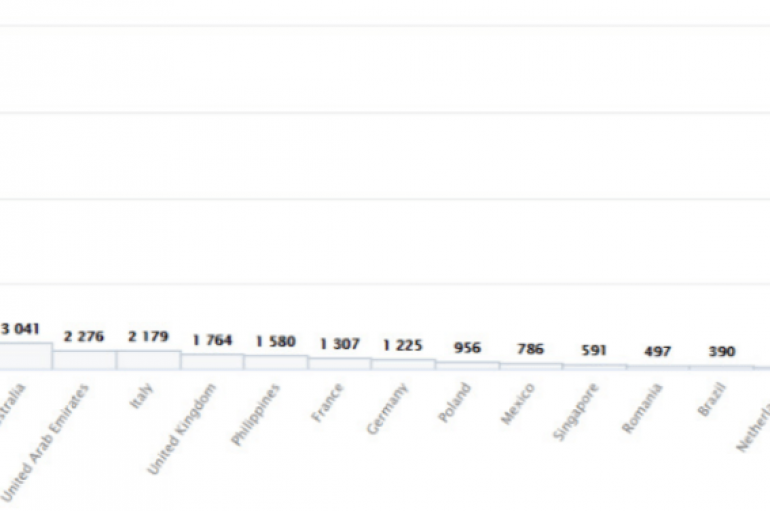
UK printing company Doxzoo exposed hundreds of gigabytes of information, including documents related to the US and British military. Security experts at vpnMentor discovered 343GB worth of files belonging to the printing company Doxzoo that were exposed on an AWS
Norwegian Cruise Line Suffers Data Breach
A major cruise operator has suffered a data breach as the travel industry battles the storm created by the COVID-19 outbreak. Information from a database belonging to Norwegian Cruise Line was discovered on the dark web by an intelligence team
APT28 Attacks Webmail and Microsoft Exchange Servers to Launch Sophisticated Spear Phishing Attacks
Pawn Storm having a group also known as APT28, Strontium, and Fancy Bear active since at least 2004, the group has targeted many organizations globally. The threat actors behind the hacking group use sophisticated social engineering lures, data-stealing malware, several
Experts warn of scanning activity conducted by Russia-linked APT28 cyberespionage group, hackers are searching for vulnerable mail servers. According to security researchers from Trend Micro, the Russia-linked APT28 cyberespionage group has been scanning vulnerable email servers for more than a
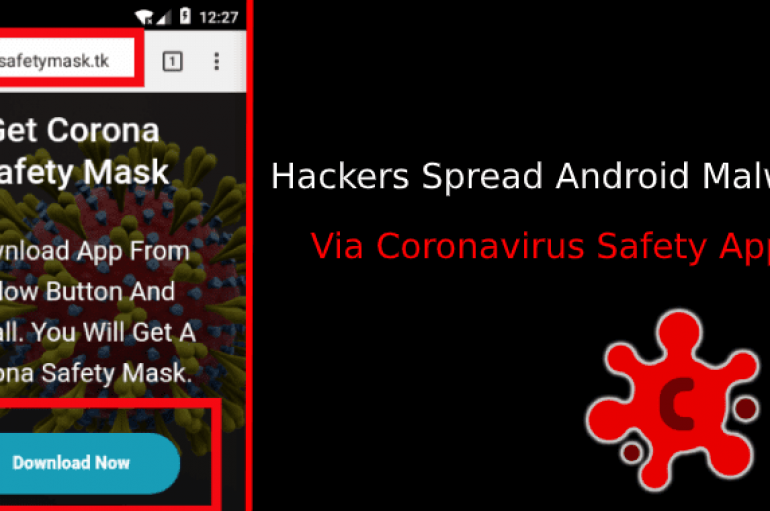
Researchers discovered a new Coronavirus safety Android App that infects Android users via malware, as a result, it hefty usage charges for victims. Attackers taking advantage of the Coronavirus fear to continuously exploit online users by infecting their mobile with
The infamous Russian threat group known as APT28 or Pawn Storm has spent the past year scanning for vulnerable email, Microsoft SQL Server and Directory Services servers, in what appears to be something of a change in tactics. The APT
Over Five Billion Breached Records Leaked
A London-based cybersecurity vendor appears to have leaked a massive database of previously breached user information dating back seven years. Researcher Bob Diachenko found the unsecured Elasticsearch instance on March 15. It contained two collections, one with 15 million records
Twitter Will Try to Ban #COVID-19 Misinformation
Twitter has released details of the steps it’s taking to combat misinformation on COVID-19, but admitted that its increasing reliance on automated systems may lead to more mistakes. The social network said it was broadening its definition of harm to
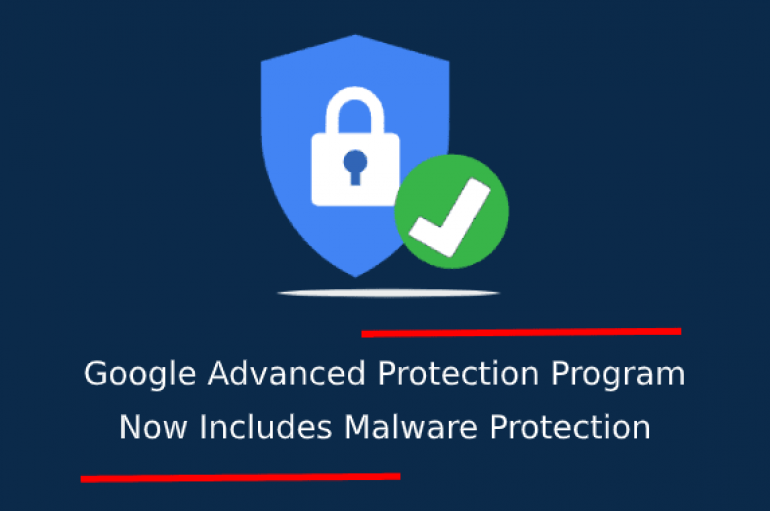
Google launched its Advanced Protection Program in the year 2017, the program aimed to protect users against phishing, blocking malicious apps, and to protect users from attackers. The program provides a high level of protection for high-risk users such as
A new variant of the TrickBot malware is targeting telecommunications organizations in the United States and Hong Kong. Security experts from Bitdefender recently discovered a new TrickBot variant that is targeting telecommunications organizations in the United States and Hong Kong.
A new organization has been established in the United States to share information regarding cyber-threats with political campaigns. The US CyberDome PC-ISAO is the first-ever political campaign information sharing and analysis organization to be created in America. It was formed
WhatsApp is partnering with the World Health Organization to fight back against the spread of fake news regarding the COVID-19 outbreak. The popular messaging platform, which has been used to spread disinformation in the past, has established a new Coronavirus
A growing number of world governments are using surveillance techniques to gauge whether their citizens are heeding instructions to stay indoors and isolate amid the COVID-19 outbreak. Technologies designed to track and analyze terrorists, tourists, and public travel patterns are