Archive
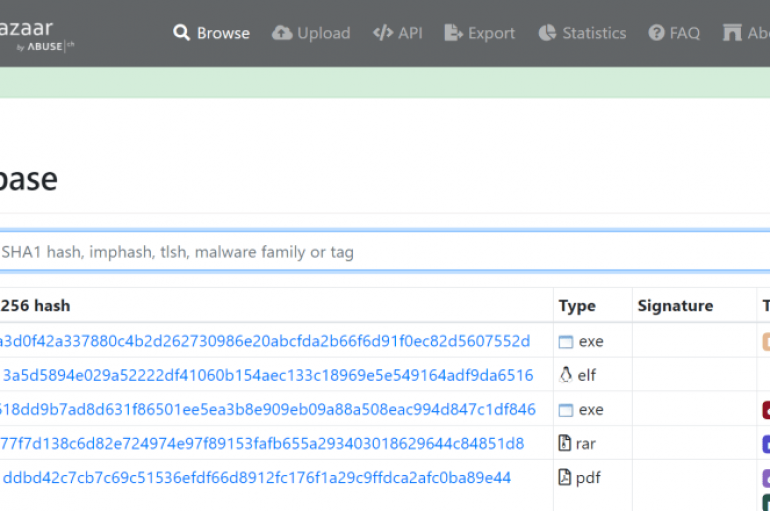
Abuse.ch launched the MalwareBazaar service, a malware repository to allow experts to share known malware samples and related info. Abuse.ch launched a malware repository, called MalwareBazaar, to allow experts to share known malware samples and related analysis. MalwareBazaar is available
A third of UK businesses do not currently have the tech infrastructure to handle long-term remote working, according to new data commissioned by Leonne International and conducted by independent survey company Censuswide. The concerning research comes at a time when
Microsoft issued a security warning for two unpatched critical windows 0-day vulnerabilities and the attackers currently exploiting in wide by executing arbitrary code remotely. 2 Vulnerabilities are uncovered in the Adobe Type Manager Library that affects all versions of Windows,
The National Gallery was subjected to nearly two million email cyber-attacks last year, official data received by Absolute Software has revealed. Obtained via a Freedom of Information request, the figures displayed the lengths cyber-criminals went to try and steal the
The US Department of Justice on Saturday filed its first court action against a website operator accused of committing fraud to profit from the global COVID-19 pandemic. A temporary restraining order was filed in a federal court in Austin against
Virginia Forms Coronavirus Fraud Taskforce
Law enforcement agencies in Virginia have created a new task force to deal specifically with the rising deluge of scams based around the COVID-19 outbreak. The Virginia Coronavirus Task Force is a joint federal and state initiative led by assistant
Numerous LinkedIn users are claiming to work for established companies, with the companies often left powerless to act upon this problem. According to a LinkedIn post by Andy Cuff, CEO and founder, Computer Network Defence Ltd, he has been alerted
MalwareHunterTeam experts have identified a new Coronavirus phishing campaign that aims at delivering the Netwalker Ransomware. The number of coronavirus-themed cyberattacks continues to increase, MalwareHunterTeam researchers uncovered a new campaign that is delivering the Netwalker Ransomware, aka Mailto. The researchers have analyzed
Google Security Update Fixed Multiple High Severity Vulnerabilities in Chrome – Update Now
Google released Chrome 80.0.3987.149, a stable channel update for Windows, Mac, and Linux with the fixes for several high severity vulnerabilities. Google Addressed 13 “high” severity bugs that were reported by various external security researchers. Due to the COVID-19 outbreak,
Hackers are offering for sale on the dark web data belonging to 538 million Weibo users, including 172 million phone numbers. Data of 538 million Weibo users are available for sale on the dark web the news was reported by
Online extortionists are now threatening email victims with COVID-19 infection if they don’t pay thousands of dollars, marking yet another evolution in their scam tactics. Sophos reported the sextortion scam, which follows a similar pattern to others of this type.
Military Secrets Exposed by UK Printing Company
Security researchers have warned that as many as 100,000 customers of a UK-based printing company including military organizations may have had sensitive personal and business documents exposed in another cloud leak. Researchers at vpnMentor found the misconfigured Amazon Web Services
A hacking group has released details of a Russian intelligence project to build a Mirai-like IoT botnet. Digital Revolution is well known for hacking organizations that do business with the Federal Security Service (FSB). Last week it published technical documents
Cybercriminals launching a new variant of Mirai Malware by taking advantage of the recently patched remote code execution vulnerability (CVE-2020-9054) in Zyxel network-attached storage (NAS) devices. The vulnerability marked as “critical” with 9.8 CVE rate, and the bug lets Mukashi
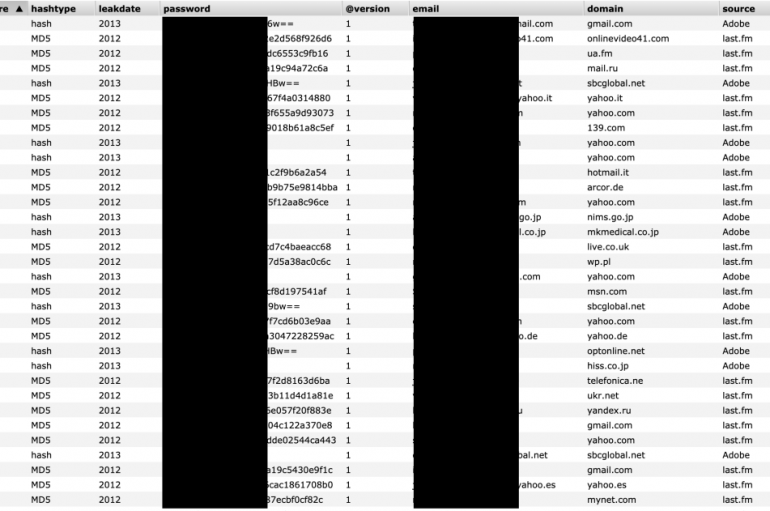
Security Firm Accidentally Exposed An Unprotected Database with 5 Billion Previously Leaked Records
Expert discovered an Elasticsearch instance belonging to a security firm containing over 5 billion records of data leaked in previous incidents. The expert Bob Diachenko has discovered an unsecured Elasticsearch install belonging to a UK security firm that contained 5
Do you do most of your transactions using your credit card? Or, are you active on social media? Then, you are a potential identity theft victim. Because most online scams succeed when the perpetrator disguises as a credible person. In