Archive
Phishing, Humans Root of Most Healthcare Attacks
Across healthcare organizations in the US, malicious actors are successfully leveraging phishing attacks to initially gain access to networks, according to findings from the 2019 HIMSS Cybersecurity Survey published by the Healthcare Information and Management Systems Society (HIMSS). The study,
Information Warfare a Top Cyber-Threat in 2019
Predicting threats that are yet to come is always tricky, but a new report published by Booz Allen, 2019 Cyberthreat Outlook, identifies eight key threats to watch as the year advances. In addition to combing through thousands of intelligence reports
Experts from Safety Detective discovered thousands of refrigeration systems made by Resource Data Management (RDM) exposed to remote attacks. Thousands of instances of a temperature control system made by Resource Data Management (RDM) are exposed to remote attacks because they
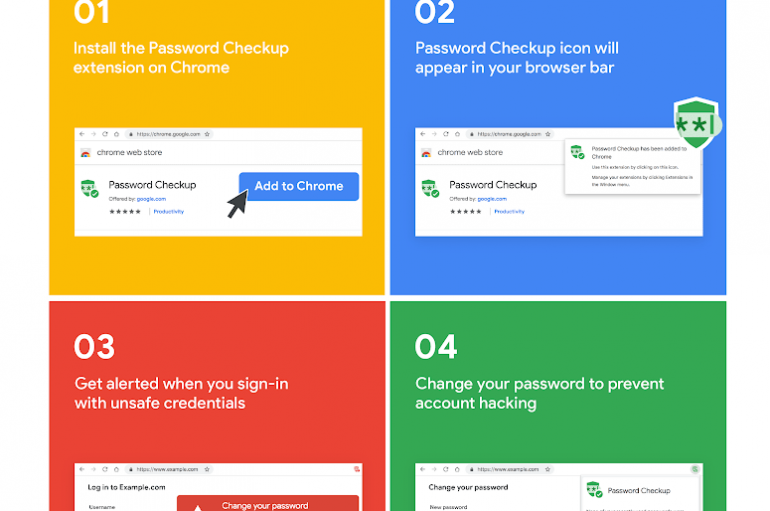
Google has released a new extension for Chrome dubbed Password Checkup that will alert users if their username/password combinations were leaked online as part of a dump after a data breach. Last week Google released Password Checkup a Chrome extension
Mumsnet Privacy Snafu Exposes User Info
Mumsnet has suffered a serious data leak affecting potentially thousands of users after a software glitch during an IT system migration to the cloud. Justine Roberts, founder and CEO of the popular parenting forum, explained in a blog post late
Converged IT and OT to Advance Security Maturity
The convergence of IT, operational technology (OT) and industrial internet of things (IIoT) has raised concerns about cybersecurity, safety and data privacy for many organizations, according to a new Ponemon Institute study. Released today in partnership with TUV Rheinland OpenSky,
Senators Urge Security Audit of Foreign VPNs
Two US senators have called for an urgent investigation into whether foreign-owned Virtual Private Networks (VPNs) represent a risk to national security. Ron Wyden and Marco Rubio signed a joint letter to the director of the Department of Homeland Security‘s
OkCupid Users Victims of Credential Stuffing
Love is in the air this week, but cyber-criminals are reportedly targeting user accounts on dating sites like OkCupid ahead of Valentine’s Day. Multiple news outlets have reported that OkCupid users say their accounts have been hacked, which the company
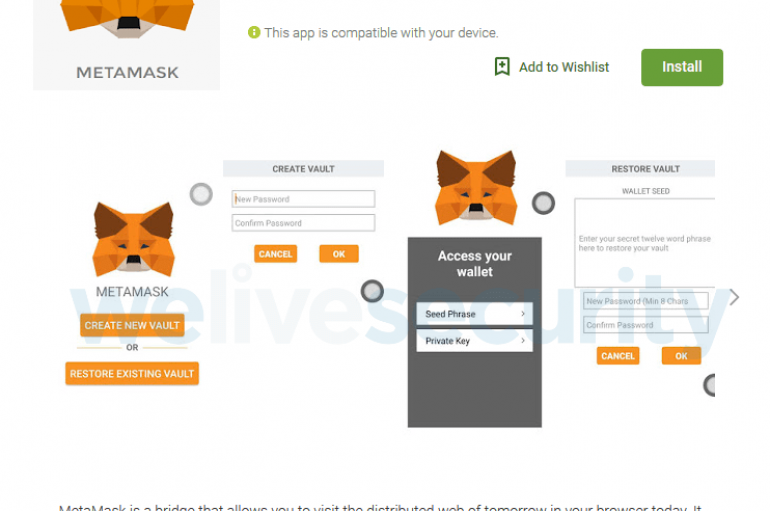
Security researcher Lukas Stefanko from ESET discovered the first Android cryptocurrency clipboard hijacker impersonating MetaMask on the official Google Play store. The rogue MetaMask app is a Clipboard Hikacker that monitors a device’s clipboard for Bitcoin and Ethereum addresses and
Driverless Cars Fail to Focus on Cybersecurity
Driverless vehicles and connected cars are creating a buzz in the marketplace, but as the industry races to produce the connected car of the future, it is letting cybersecurity fall to the wayside, according to new research from Synopsys. In
Android users could be remotely hacked simply by viewing a legitimate-looking PNG image, Google has warned in its latest security update. The Android Security Bulletin for February lists 42 vulnerabilities in the Google mobile operating system, 11 of which are
Ransomware accounted for one tenth of 1% of all malicious email content in Q4, according to a new threat report from Proofpoint. It’s Q4 threat report found that banking trojans accounted for 56% of all malicious payloads in email in
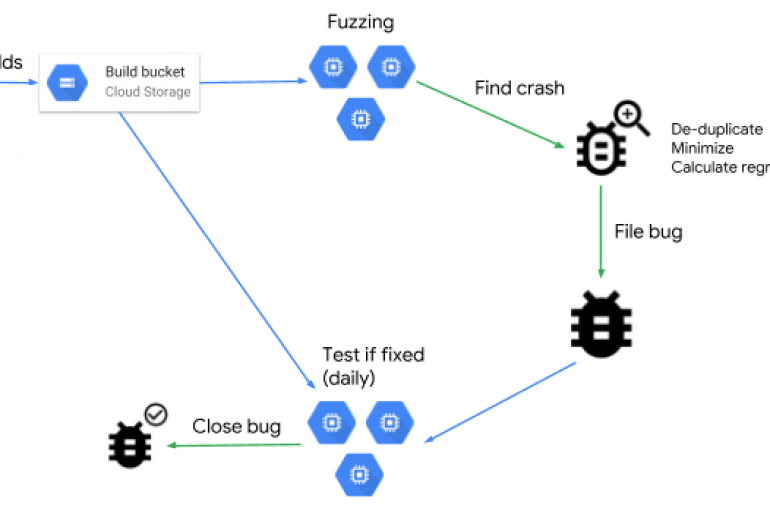
Google has open sourced ClusterFuzz, its fuzzing infrastructure it has developed to find memory corruption vulnerabilities in Chrome. Google has open sourced its fuzzing infrastructure ClusterFuzz that the tech giant developed to find memory corruption bugs in the Chrome browser.
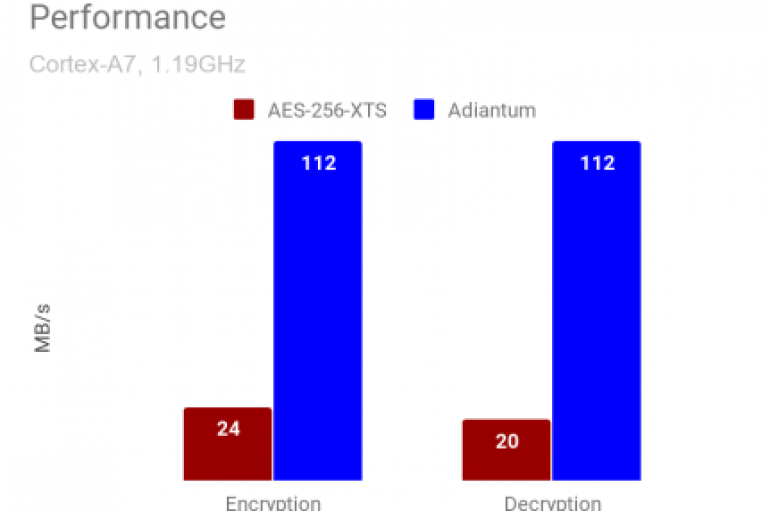
Google announced Adiantum, a new encryption method devised to protect Android devices without cryptographic acceleration. Google announced Adiantum, a new encryption method devised to protect Android devices without cryptographic acceleration. “Adiantum is an innovation in cryptography designed to make storage
Security of Industrial system is a top priority, experts found multiple serious flaws in a gateway made by Kunbus that could allow to completely control a device Nicolas Merle from industrial cybersecurity firm Applied Risk discovered several flaws in a
Cayosin Botnet: a deeper look at this threat supported by the psychological profile of the “youngsters-wannabe-hackers” Rolex boasters Money, botnet as service business and coding on the dark side of the life: “At this point of my life… if it