Archive
Student Data Exposed at Stanford University
The private data of students at Stanford University was exposed after someone changed a numeric ID in a URL that had been distributed to students who requested access to review their own files, according to The Stanford Daily. In total,
The Muncy Malware is on the Rise
Over the last few days, a phishing campaign from DHL and entitled “DHL Shipment Notification” has been targeted users worldwide distribution the Muncy malware. Muncy is the name dubbed by SI-LAB that analyzed this threat. Now, the malware is targeting
As the value of Bitcoin and other cryptocurrencies continues to fluctuate while governments consider marketplace regulations, J.P. Morgan announced that is launching the first US bank-backed cryptocurrency, JPM Coin. “The JPM Coin is based on blockchain-based technology enabling the instantaneous
Five Billion Records Exposed in 2018
Last year was the second highest on record in terms of data breaches and leaks, with over 6500 reported, according to Risk Based Security. The security vendor revealed that 6515 incidents were reported globally in 2018, second only in the
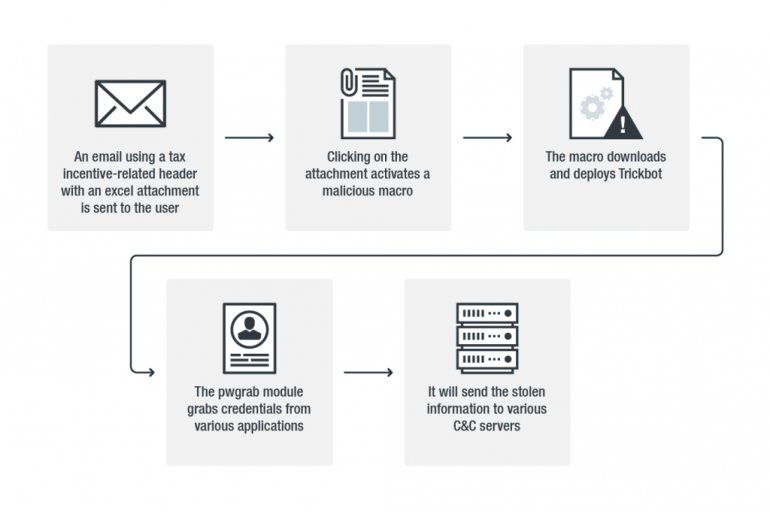
The Trickbot banking trojan continues to evolve, Trend Micro detected a new variant that includes a new module used for Remote App Credential-Grabbing. The infamous Trickbot banking trojan is back, experts at Trend Micro detected a new strain of the
Security researchers have spotted a mass data leak from an unsecured database which exposed the personal details of over 2.5 million surveilled Chinese residents. SenseNets Technology uses AI-powered technology in facial recognition cameras to record the movements of millions of
Australian Prime Minister Scott Morrison has blamed a “sophisticated state actor” for the recent attempt to hack the parliament’s computer network. On February 8 news broke of the malicious activity which resulted in password resets for government workers. Speaking today,
Last week, Aleksa Sarai, a senior software engineer at SUSE Linux GmbH, disclosed a serious vulnerability tracked CVE-2019-5736 affecting runc, the default container runtime for Docker, containerd, Podman, and CRI-O. The vulnerability was discovered by the security researchers Adam Iwaniuk
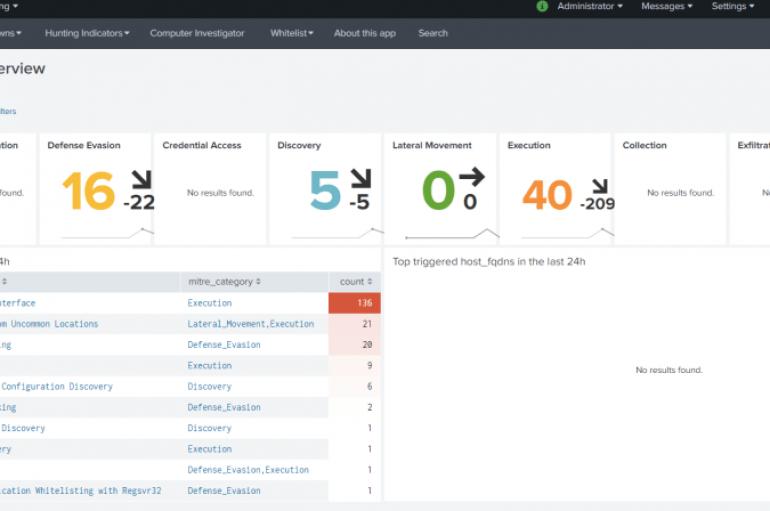
Most of us know MITRE and the ATT&CK(TM) framework that they have come up with. What a splendid job they have done for the cyber security community by bringing most of the key attack vectors under an organized framework that
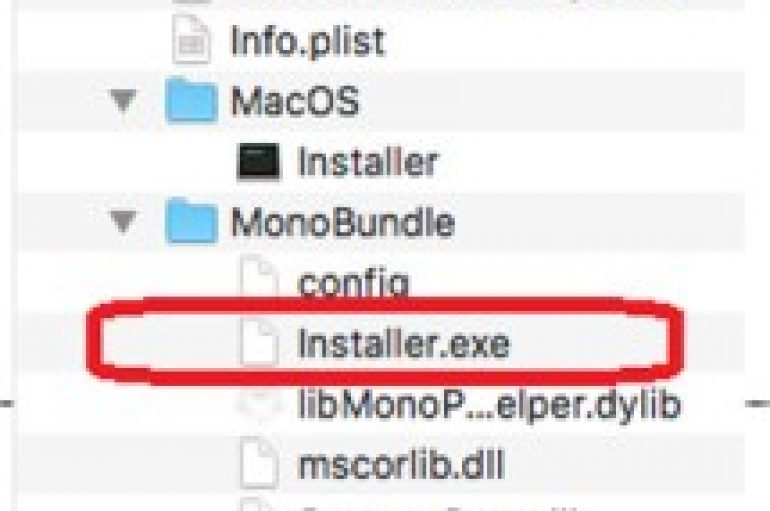
Security experts at Carbon Black have recently discovered a new strain of the Shlayer malware that targets macOS versions. Security experts at Carbon Black have recently spotted a new strain of the Shlayer malware that targets MacOS versions from 10.10.5
UK and US CISOs are facing burnout as they struggle to cope with escalating cyber-threats, insufficient budgets and a lack of engagement from the board, according to Nominet. The DNS security provider commissioned Osterman Research to poll over 400 security
GandCrab Ransomware Slingers Target MSPs
A software company has been forced to remind customers to patch a two-year-old flaw in a third-party plug-in, after reports it is being exploited to infect scores of companies with GandCrab ransomware via their managed security provider (MSP). The issue
Google Play App Suspensions Jump 66%
Google has claimed it’s getting better at spotting bad apps on its Play Store marketplace, with the number of rejected submissions and suspensions both growing into the double digits last year. The Android platform has often been criticized by security
Experts at Trend Micro have detected a new strain of MacOS malware that hides inside a Windows executable to avoid detection. Security experts at Trend Micro have spotted a new strain of MacOS malware disguises itself as a Windows executable
A new batch of 127 million records appears in the dark web, this time the huge trove of data appears to be originated from eight companies. A hacker that goes online with the moniker ‘gnosticplayers‘ is offering for sale the
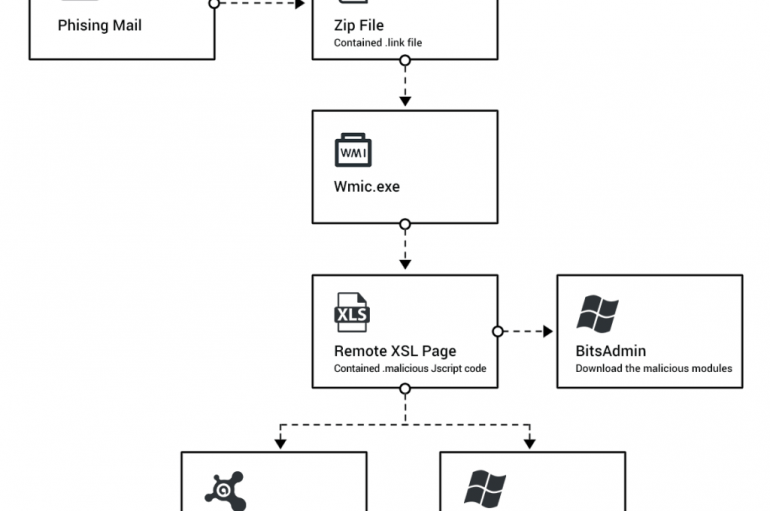
A new Astaroth Trojan campaign was spotted by the Cybereason’s Nocturnus team, hackers are targeting Brazil and European countries. Researchers at Cybereason’s Nocturnus team have uncovered a new Astaroth Trojan campaign that is currently exploiting the Avast antivirus and security