Archive
Proofpoint analyzed two strains of malware tracked as ServHelper and FlawedGrace distributed through phishing campaigns by the TA505 crime gang. Security researchers at Proofpoint researchers discovered two strains of malware tracked as ServHelper and FlawedGrace distributed through phishing campaigns by
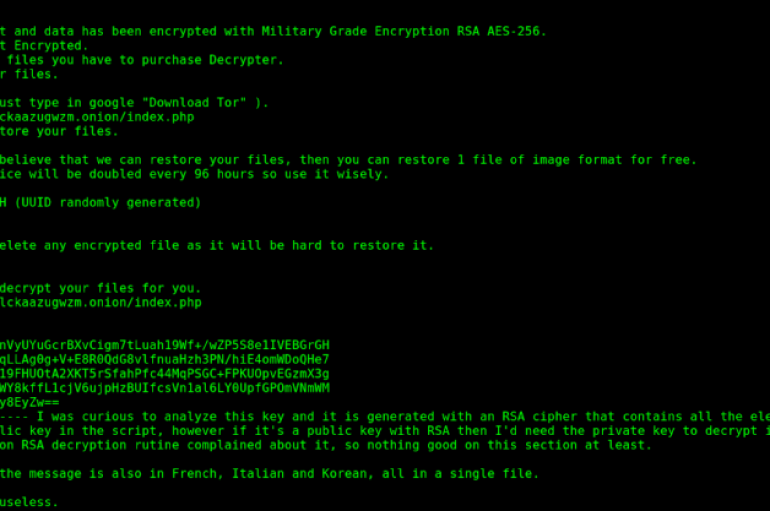
Victims of the PyLocky Ransomware can use a tool released by security researcher Mike Bautista at Cisco Talos group to decrypt their files for free. I have good and bad news for the victims of the PyLocky Ransomware. The good
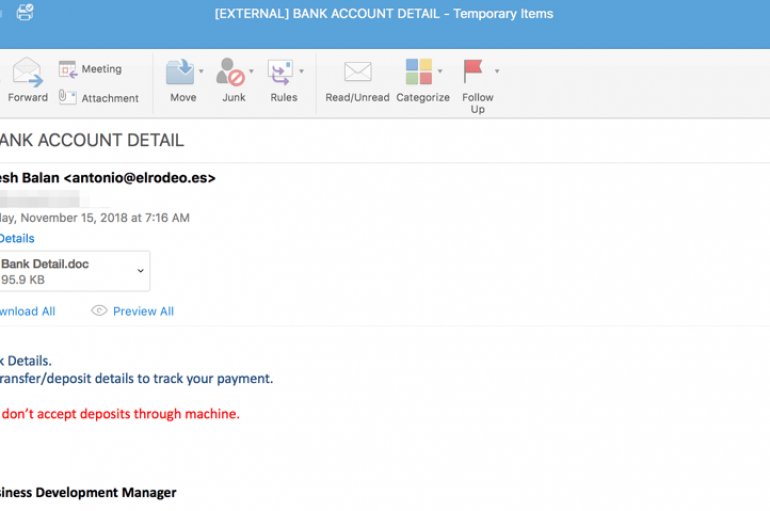
The ‘AVE_MARIA’ Malware
Ave Maria Malware – Phishing attempts spreading in the last days of the past year against an Italian organization operating in the Oil&Gas sector The Cybaze-Yoroi ZLab researchers analyzed phishing attempts spreading in the last days of the past year
Side-Channel Attack Targets Windows, Linux
A research team of experts from Graz University of Technology, Boston University, NetApp, CrowdStrike, and Intel has published findings on page cache attacks. Unlike Spectre and Meltdown, this attack is a first-of-its-type, hardware-agnostic, side-channel attack that can remotely target operating
Third-Party Breach Exposed 31K Patient Records
The healthcare sector continues to be the target of cyberattacks, with Managed Health Services (MHS) of Indiana Health Plan announcing recently that a third-party data breach potentially exposed up to 31,000 patients’ personal data in one of two security incidents
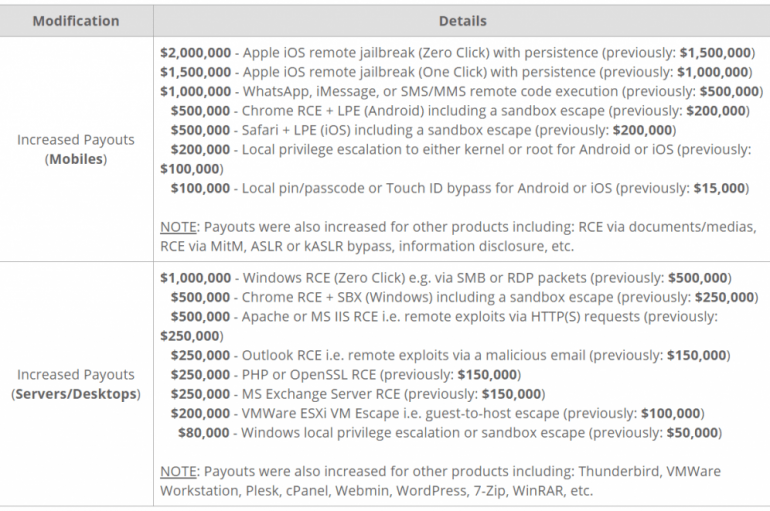
The zero-day broker Zerodium offers $2 million for remote iOS jailbreaks and $1 million for chat app exploits. Zerodium announced it is going to pay up to $2 million for remote iOS jailbreaks that don’t need any user interaction, Previous
Microsoft Kicks Off 2019 With Medium Patch Load
Microsoft started the new year yesterday by issuing fixes for a near half century of vulnerabilities, although only seven were rated critical. Many of these were remote code execution (RCE) bugs, with experts agreeing that CVE-2019-0547 should be top of
Phone Carriers Selling Customer Location Data
Bounty hunters are able to leverage a somewhat dubious skeptical service available through major telecom companies, including T-Mobile, AT&T, and Sprint, according to Motherboard. A researcher reportedly paid $300 to a bounty hunter who was then able to geolocate a
Award-winning cooking tools company OXO revealed that it has suffered data breaches over the last two years that may have compromised customer and credit card information. In a breach disclosure letter filed with the State of California, OXO said that
A Python network tool, Scapy, is vulnerable to denial-of-service (DoS) attacks, according research published by Imperva. The company also released its 2018 State of Web Application Vulnerabilities, which found that injections represented 19% of the total vulnerabilities in 2018, while
IcePick-3PC Malware Strain Steals Device IPs
IcePick-3PC has impacted a range of businesses, from publishers to e-commerce, across a variety of industries, including retail and healthcare, according to researchers from The Media Trust‘s digital security and operations (DSO) team. The malware strain was first identified in
Network and endpoint security company, Sophos, announced today that it has acquired Avid Secure, a cloud infrastructure security company that uses artificial intelligence to deliver cloud security analytics, according to a press release. No further details about the acquisition have
The cryptocurrency exchange Coinbase suspended the trading of Ethereum Classic (ETC) after double-spend attacks worth $1.1 Million The cryptocurrency exchange Coinbase has suspended the trading of Ethereum Classic (ETC) after double-spend attacks that consist in spending digital coins twice. Ethereum
Disgruntled Man Behind German Cyber-Attack
Citing annoyance at government officials as his motive, a 20-year-old man has confessed to be the hacker responsible for releasing private information on hundreds of politicians in Germany, according to Reuters. The news comes one day after investigators at the
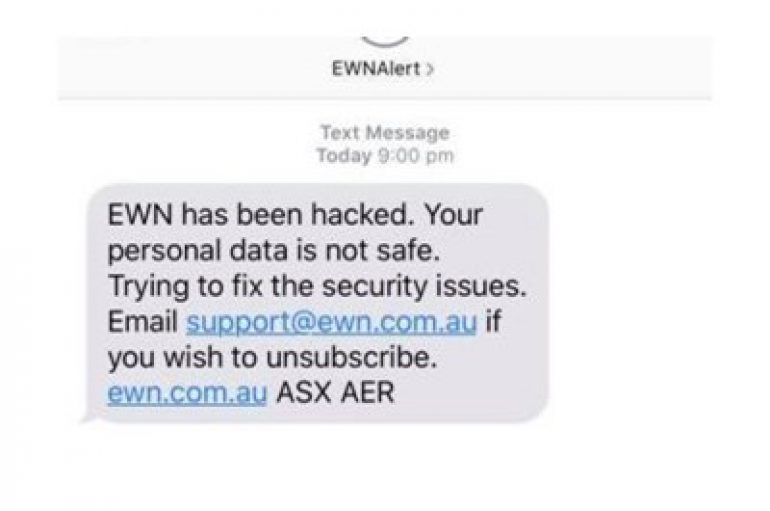
Detection Limited Hacker Access to EWN Database
Swift detection of a malicious insider that used stolen credentials to gain unauthorized access to Australia’s Early Warning Network (EWN) allowed EWN staff to shut down systems and limit the number of messages the hacker was able to disperse, according
Security researchers have warned users of P2P sites of a new malvertising campaign featuring a twin threat: info-stealing malware and ransomware. By registering rogue advertising domains, the attackers are able to direct torrent site visitors to two different exploit kits: