Archive
Schneider Electric: TRITON/TRISIS Attack Used 0-Day Flaw in its Safety Controller System, and a RAT
S4x18 CONFERENCE – Miami – Industrial control systems giant Schneider Electric discovered a zero-day privilege-escalation vulnerability in its Triconex Tricon safety-controller firmware which helped allow sophisticated hackers to wrest control of the emergency shutdown system in a targeted attack on
Cryptocurrency miners have begun using two older and already patched vulnerabilities to compromise servers to mine the Monero digital currency. Trend Micro researcher Hubert Lin reported a significant increase in the use of Apache Struts (CVE-2017-5638) and DotNetNuke (CVE-2017-9822) starting
Several universities and more than 20 companies have been hit with malware whose creators are using several layers of subterfuge to camouflage their phishing attack by taking advantage of a few trusted brand names. The new scam was uncovered by
Nexus Zeta behind botnet that weaponises router exploit to enlist further vulnerable IoT devices. The author of Satori botnet may also be behind two new Mirai variants called Masuta and PureMasuta. According to a blog post by researchers at NewSky
Despite facing mostly external attacks, nearly half (45%) of businesses believe their greatest security risk comes from their own employees, according to the 2018 Netwrix Cloud Security Report. The blame falls more heavily on IT staff (39%) and businesses users
Attackers have made off with up to US$400,000 (£290,000) in cryptocurrency after an ingenious attack on Stellar Lumen (XLM) wallet, BlackWallet. In the latest cryptocurrency security incident, hackers managed to compromise the server hosting popular web-based wallet BlackWallet and change
The company trying to be the Google of hacked user credentials says it just obtained another huge leak, this time affecting Twitter users. LeakedSource recently reported it obtained a database of more than 32 million Twitter login credentials from a
Researchers have found a loophole in Intel processors that allow an attacker to bypass logins and place backdoors on laptops, allowing adversaries remote access to laptops. Researchers at F-Secure, that first identified the attack strategy, say the loophole can be
‘MaMi’ Mac Malware Hijacks DNS Settings
The malware, dubbed OSX/MaMi by Wardle based on a core class named “SBMaMiSettings,” is currently only detected – at least based on its signature – by ESET and Ikarus products as OSX/DNSChanger.A and Trojan.OSX.DNSChanger. However, other vendors will likely create
The Anatomy of a Data Breach
Join Fran Malloy, IBM Security Technical Sales Management and former CISO of a Fortune 500 company, as he shares an authentic and candid firsthand experience of surviving a highly public breach. Understand what you have to consider and even how
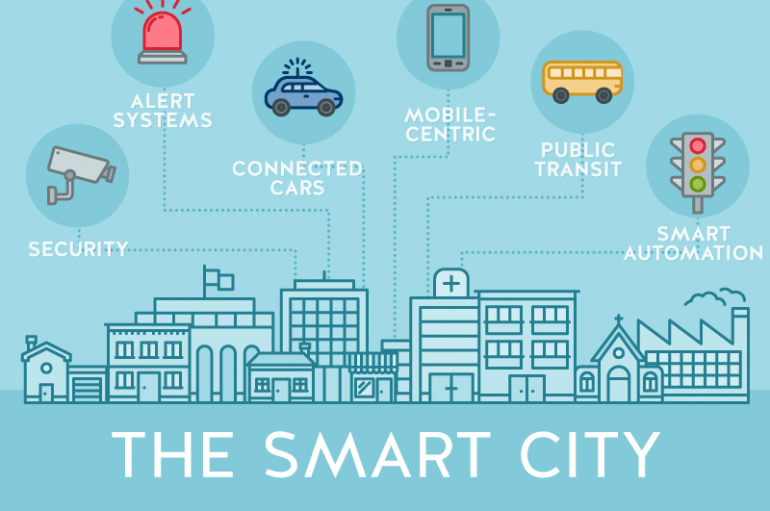
Smart City Security and Cyber Attacks
Technology adoption is bringing about massive change in major cities around the world from smart traffic lights to knowing exactly what time transportation will arrive and paying for public services with the touch of a credit card or personal device.