Archive
Pakistan passes controversial cyber-crime law
ISLAMABAD (Reuters) – Pakistan has adopted a much-criticised cyber security law that grants sweeping powers to regulators to block private information they deem illegal. The National Assembly approved the Prevention of Electronic Crimes Bill 2015 late on Thursday after the
The website of the organization that oversees competitive swimming in Australian has come under cyber attack, allegedly in connection with an Australian swimmer calling a Chinese competitor at the Rio de Janeiro Olympics a “drug cheat,” according to a report.
Google released two new security features that attempt to make Gmail safer for users. The updates, announced Wednesday, will benefit Gmail users on the web or Android. If users receive a message that can’t be authenticated, the search giant will
As well as a great opportunity to spy on some of the most talented security researchers, hacking conferences are naturally a hotbed for those looking to get up to a bit of mischief. Newly published data suggests a load of
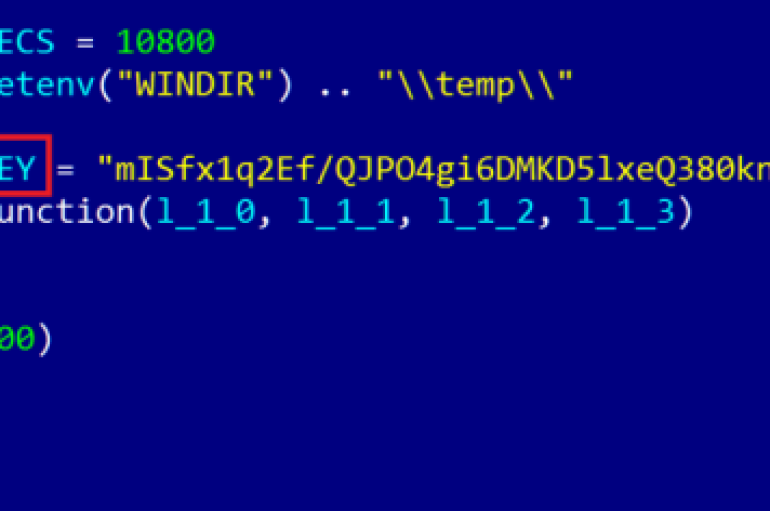
MICROSOFT MISTAKENLY LEAKS SECURE BOOT KEY
Two researchers operating under aliases (my123 and slipstream) this week posted a report—accompanied by a relentless chiptune—that reveals how Microsoft inadvertently published a Secure Boot policy that acts as a backdoor that allows for the UEFI firmware feature to be
Fiat Chrysler Automobiles may not be the only automaker with hacking vulnerabilities to worry about as a new report suggests that over 100 million Volkswagens are susceptible to remote hacking. A lengthy report compiled by four security experts from the
Security experts have discovered a malware platform that’s so advanced in its design and execution that it could probably have been developed only with the active support of a nation state. The malware—known alternatively as “ProjectSauron” by researchers from Kaspersky
In action five years, highly selective threat actor has only been known to compromise seven organizations. Symantec has discovered a previously unknown cyberespionage group so selective in its targets that it is only known to have compromised seven organizations and
Two men jailed in Houston and accused of using pirated computer software to steal more than 100 vehicles may have exploited an electronic vulnerability to advance auto theft into high-tech crime. Michael Arce, 24, and Jesse Zelaya, 22, focused on
We think of our monitors as passive entities. The computer sends them data, and they somehow—magically?—turn it into pixels which make words and pictures. But what if that wasn’t the case? What if hackers could hijack our monitors and turn
36th GITEX Technology Week
Those of you with a Yahoo account may want to reset your password, as the hacker behind the recent MySpace and LinkedIn data dumps is claiming that he has the details of 200 million Yahoo accounts. He’s ready to sell
Another year, another Black Hat, another Jeep steered into a ditch next to a cornfield. Last July, you might recall how automotive cybersecurity researchers Charlie Miller and Chris Valasek remotely hijacked the digital systems of a Jeep Cherokee from 10
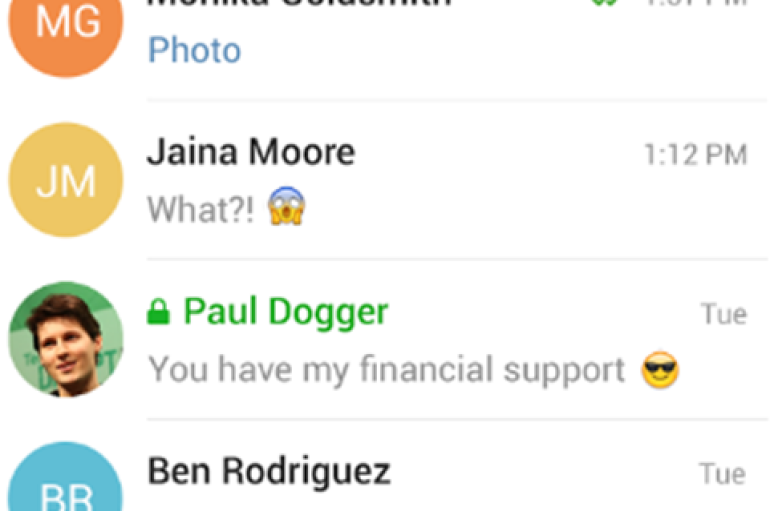
Hackers accessed Telegram accounts in Iran
Iranian hackers have compromised more than a dozen accounts on the Telegram instant messaging service and identified the phone numbers of 15 million Iranian users, researchers have found. The attacks, which took place this year, jeopardised the communications of activists,
LastPass Patches Password Manager Vulnerability
Password managers are a wise way to manage large volumes of login credentials in a safe way. The applications generate strong passwords for new web services and securely store them. But if a password manager has software vulnerabilities, it could
LAS VEGAS – Credit card companies for the most part have moved away from “swipe and signature” credit cards to chip and pin cards by this point; the technology known as EMV (Europay, MasterCard, and Visa) which is supposed to