Archive
An unknown hacker or a group of hackers just claimed to have hacked into “Equation Group” — a cyber-attack group allegedly associated with the United States intelligence organization NSA — and dumped a bunch of its hacking tools (malware, private
Some days you can’t win for losing. In 2012, Linux implemented a new TCP/IP networking standard, RFC 5961, Improving TCP’s Robustness to Blind In-Window Attacks, to improve security. In the process, they opened up a heretofore unknown security hole. Ironically,
most four out of every 10 businesses have been hit by ransomware over the past year, and instances of such malware in exploit kits have increased by 259 percent over just the past five months, according to a new study.
A hacker who has previously offered to sell user data from MySpace and LinkedIn on the Dark Web is reportedly now shopping around the credentials of 200 million Yahoo users. The cyber thief, who goes by the name “Peace,” is
People tend to hate computer passwords, that often nonsensical jumble of letters, numbers and special keystrokes said to be essential for digital security. The secret codes seem impossible to remember. It’s why every login page has a “Forgot password?” life
Vodafone, Airtel networks witnessed cyberattacks
In a recent incident, internet service providers such as Tata Communications, Airtel and Vodafone in Mumbai, Maharashtra and other regions were hit by cyberattacks in July. “A case has been reported of Distributed Denial of Service (DDoS) attack on July
SANS Security Leadership Summit 2016
Attacks on Mobile Devices and Apps on the Rise
Enterprises continue to fall short when it comes to protecting corporate data on mobile apps and devices, according to the Mobile Security and Risk Review, by MobileIron at the 2016 U.S. Black Hat conference in Las Vegas. Mobile threats are
Hope you weren’t too used to browsing Facebook without seeing any ads. The company on Tuesday will begin preventing ad blocking software from blocking ads on the desktop version of the Facebook.com website. The move, which Facebook couched in moral
Startup Spotlight: NewSky Security looks to disrupt hackers before nefarious plots are hatched
Hardly a day goes by without a high-profile security breach or nasty computer hack. Scott Wu and Song Li — the co-founders of Redmond-based NewSky Security — want to stop those hackers in their tracks. The longtime security professionals —
SYDNEY (Reuters) – German tech entrepreneur and alleged internet pirate Kim Dotcom will seek a review of a Federal Court decision which rejected his bid to keep hold of millions of dollars in assets held in Hong Kong and New
A Nostalgic Virus Is Infecting Windows Machines
Anyone who visited FossHub on Tuesday to download either Start Menu replacement Classic Shell or the audio editor Audacity is at risk of having downloaded a Trojan that feels like something out of the early ’90s. The malicious code was
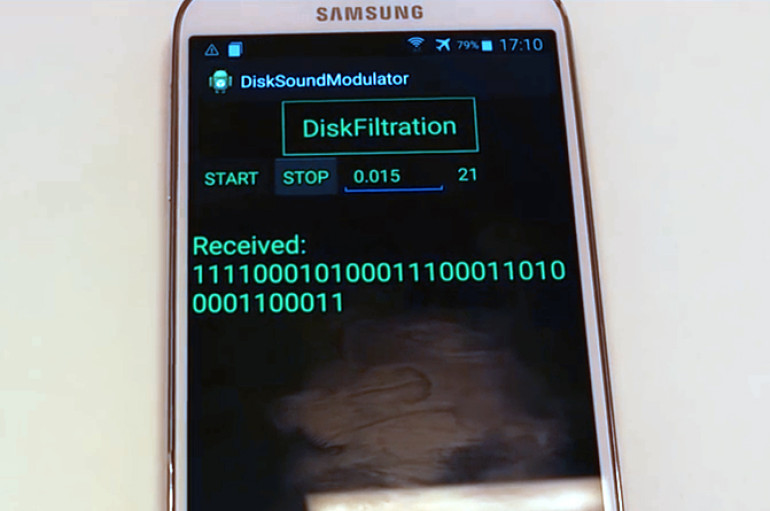
Do you think your data is safe because your computer isn’t connected to the internet or a network? Wrong. As security researchers recently demonstrated, the sounds of your computer’s hard drive can be used to transmit data from an air-gapped
Nearly 40 percent of businesses have experienced a ransomware attack in the last year, according to a new study. Of these victims, more than a third lost revenue and 20 percent had to stop business completely. The report, “State of
This past March Bloomberg offered a compelling look inside the world of election hacking in which campaigns and their supporters hack into their opponents and steal or destroy data, saturate the online space with fake messaging and otherwise attempt to