Archive
Three hackers have found eight holes in Uber that could allow fake drivers to be created and user email addresses reveal, and found more than 1000 of valid coupon codes including one giving drivers $100 extra in fare rides. The
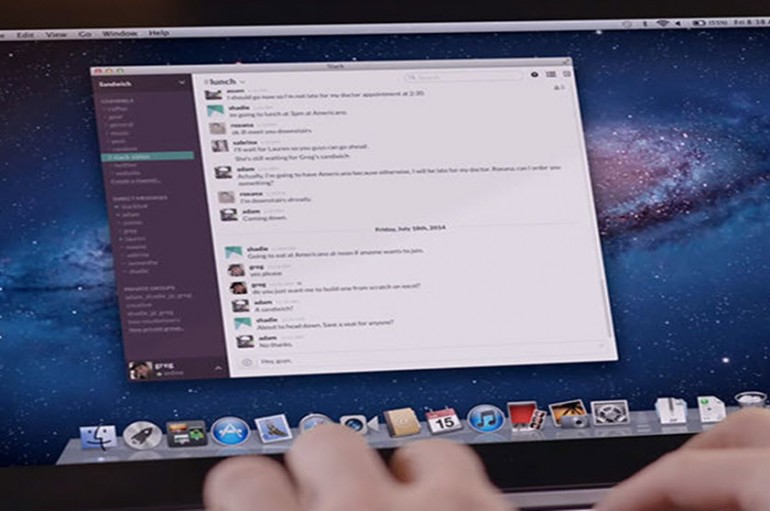
It’s a harsh lesson to learn, but internal chat messages like Slack are really not your friend. In fact, they can be your worst enemy. Teachers at the Blackstone Valley Prep High School in Rhode Island learned that lesson in
Every now and then, Blizzard Entertainment’s Battle.net gets disturbed with a server hack and the danger of leaking some of its users information, and it looks like it happened again. Blizzard announced that their servers suffered from a security breach
An unpatched remote code execution hole has been publicly disclosed in the popular Swagger API framework, putting users at risk. The client and server hole (CVE-2016-5641) exists in code generators within the REST programming tool, also know as the OpenAPI
An orchestrated hacking campaign is targeting members of Air India’s frequent-flyer program, so far pilfering $23,745 worth of travel miles. The Flying Returns program has more than 195,000 customer accounts. The Delhi Police said that the attack appears to have
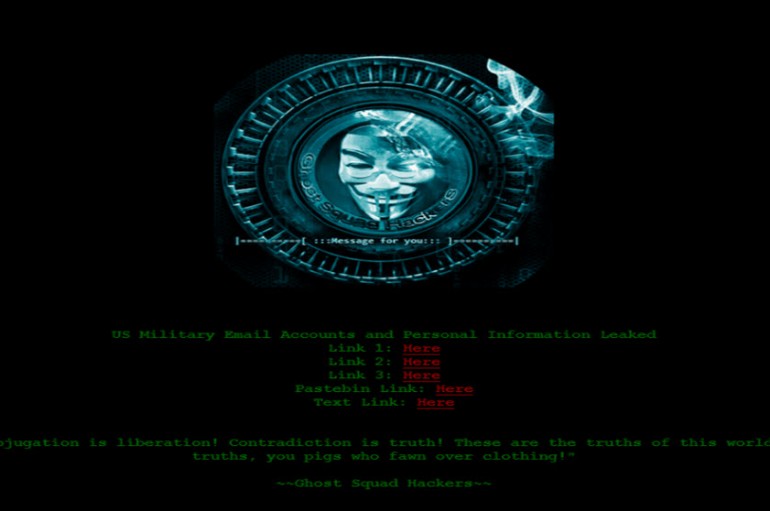
Ghost Squad Hackers dumped the data of US military personnel, according to a Facebook post published today. The data is on a website on the Dark Web but was added to PasteBin after a few hours as well. Group leaks
Anonymous hackers back Brexit vote in scathing tweet blasting ‘European elites who put wealth over people’
Anonymous hackers have thrown their weight behind Brexit in a scathing tweet blasting European elites who put wealth over people. As millions of Brits cast their votes in yesterday’s historic EU referendum , the secretive global hacking network took to
Google researchers tackle AI and robotics safety, prevent future toasters from killing us in our sleep
Humans have been afraid of the dangers posed by AI and hypothetical robots or androids since the terms first entered common parlance. Much early science fiction, including stories by Isaac Asimov and more than a few plots of classic Star
The Department of Defense’s recent “Hack the Pentagon” bounty program was such a hit that the Department of Health and Human Services is starting to take a look at it. HHS officials mentioned the DoD’s recently completed pilot program—which paid
A client comes to you because FBI agents seized his iPhone pursuant to a search warrant, which seeks particular records that are stored within it. The client has kept his iPhone locked at all times because it contains sensitive data
The Supreme Court next Wednesday will hear a petition seeking a ban on WhatsApp on the ground that the messaging platform’s end-to-end encryption gives terrorists a means of communication that is impossible to intercept. Filed by Sudhir Yadav, a Haryana-based
Smartphone security is a hot topic that’s made news headlines recently, and has raised new concerns: how do you keep what’s on your phone secure and private? Experts tell us that a whole new industry of apps and software are popping
A working group of House lawmakers studying the thorny problem of encryption this week appeared to lean away from a law requiring companies to provide law enforcement with any form of guaranteed access to locked communications. “Members of the encryption
Did Apple just give everyone the keys to the kingdom? Sort-of, but it didn’t just drop them on the porch accidentally—it put them on a hook right next to the door. At least, that’s one way to think about Apple’s
Major data losses can cripple a business. According to the Disaster Recovery Preparedness Council, 73 percent of companies worldwide are failing in terms of disaster readiness. Reported losses from a disaster ranged from a few thousand dollars to millions of
Study: You Can ‘Catch’ the Online Fraud Germ
Online fraud is as much a part of the internet experience as “likes” and “retweets.” Whether it be Nigerian princes looking for social security numbers or social media hackers asking your friends’ for money, there is no end to the