Archive
Everything is going automatic – and those looking to perpetrate data breaches with malware are no different – emphasizing the need for individuals and organizations to be better prepared to keep the cyber door closed to potential threats. With the
Scammers are spreading JavaScript malware disguised as a Facebook comment tag notification. A user will receive a notification in their app and/or in their email about a friend tagging them in a comment and, upon clicking the link, malware is
Symantec has discovered an app on Google Play that steals photos and videos from the popular social media app Viber. Beaver Gang Counter masquerades as a score keeping app for a popular card game but secretly searches for media files
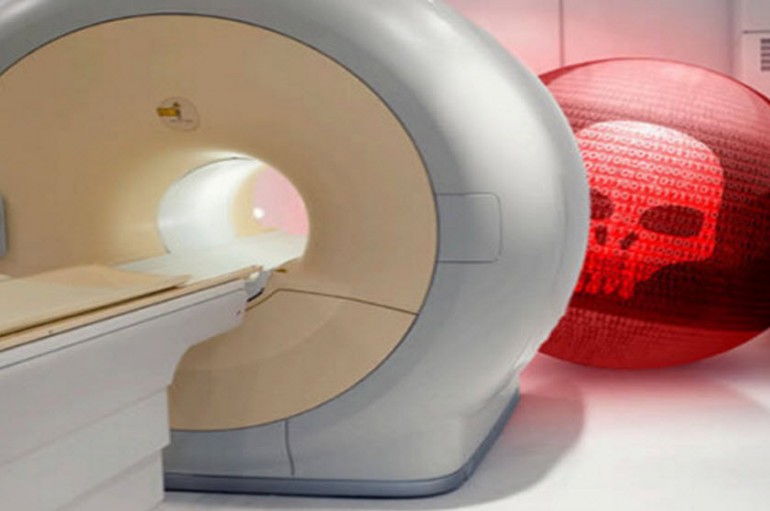
Attackers are packaging the newest and most sophisticated attack tools in long out-of-date malware wrappers, targeting medical devices running legacy operating systems, to breach hospital networks for advanced persistent attacks. Last year, TrapX Security revealed how attackers were infecting medical
New research revealed that as many as 500 restaurants in the U.S. may have been punked by PunkeyPOS, a point-of-sale (POS) malware. PunkeyPOS has been around for a while, at least according to Trustwave’s alert from 2015. It did its
Fansmitter: malware that exfiltrates data from airgapped computers by varying the sound of their fans
In a new paper, researchers from Ben-Gurion University demonstrate a fiendishly clever procedure for getting data off of airgapped computers that have had their speakers removed to prevent acoustic data-transmission: instead of playing sound through the target computer’s speakers, they
A massive network of hacked CCTV cameras is being used to bring down computers around the world, we’re told. The unusual 25,000-strong botnet was apparently spotted by US security outfit Sucuri when it investigated an online assault against an ordinary
Hospital equipment running old operating systems providing safe harbor for data theft, TrapX says. Medical devices running outdated operating systems like Windows XP and Windows 7 are giving attackers safe harbors within hospital networks for carrying out data theft in
Google scans billions of “potentially harmful apps” on the Play store, but a malware app has slipped through, and is automatically rooting phones it infects. The since-scuppered malware masqueraded as a spirit level application dubbed Level Dropper. When installed it
Hackers are stealing credit card information in Europe with malware that can spoof the user interfaces of Uber, WhatsApp and Google Play. The malware, which has struck Android users in Denmark, Italy and Germany, has been spreading through a phishing
One of the biggest tech debates in Washington is whether the government should have a “back door” or special key to unlock password-protected smartphones. Leading the opposition is Apple, which earlier this year opposed a court order by the FBI
Google encryption flaw could allow video piracy
A Google vulnerability could allow bad actors to hijack video content from protected videos, according to online newspaper Jewish Business News. A flaw within the encryption technology of Widevine EME/CDM is said to hold the potential to allow attackers to
NTT uses reflected lasers for encryption
Random number sequences used in cryptographic systems are usually generated from mathematical formulae but by understanding the algorithms behind the formulae hackers can crack the encryption. Using irregular physical phenomena to generate random numbers can achieve a higher level of
Intel does not support encryption backdoors
Intel does not support the US government’s position that encrypted devices need to have backdoors so that they can be accessed by law enforcement. In an official statement that laid out its position on encryption in the wake of the
Quick, decode that. Stumped? That’s because it’s encrypted. Well, sorta. The message, if you were curious, reads: “Encryption Matters,” and it’s part of a project by Mozilla — alongside TODO, an Italian creative agency — to teach Web users how
The United States Internal Revenue Service (IRS) has announced the abolition of its PIN tool due to the platform being hacked. Under the now abolished electronic filing PIN tool (e-File PIN) people dealing with the IRS were able to use