Archive
A hacker who claims to have obtained more than ten million health records is selling the data to the highest bidder on the dark web. The seller, who goes by the name “thedarkoverlord” began listing the data over the weekend,
Hackers Wanted (Must Be Willing to Work at Bank)
It’s hard finding a good hacker these days — a hacker to work for banks, that is. Even though cybersecurity jobs can offer six-figure salaries, generous signing bonuses and other perks, banks are struggling to find people to hire. Part
Hackers have reportedly stolen $10m from a bank in Ukraine by exploiting the Swift messaging system, according to reports emerging from the region citing an independent IT monitoring organisation called the Information Systems Audit and Control Association (ISACA). English-language newspaper,
A NASCAR team has admitted to paying hackers after several of its computers were infected with something called “ransomware,”The Register reports. Ransomware affects a computer by locking a user out of their files, and hackers then demand a ransom payment
Managed Service Provides Powerful End-To-End Security for Data “In Flight” Over Public or Private Networks Dallas – June 27, 2016 – Masergy Communications Inc. today announced WAN Encryption, a managed service that protects data end-to-end while in transit for software-defined WAN connectivity between applications
Apple last week released the first beta of iOS 10 after explaining the main features of the upcoming iPhone, iPad and iPod touch update during its WWDC 2016 opening keynote. As expected, developers and researchers started poking around and some of
It if were up to Russian policymakers, Internet controls will become even more strict in the country moving forward. Labeled as an anti-terrorism campaign, there are plans to increase online surveillance measures. If this were to happen, ISPs would need
Is your messaging app using encryption? And, actually, do you even care about that? Even though people have more choices than ever when using mobile messaging apps billed as secure and private, and surveillance and encryption have been steadily in
Google encryption flaw could allow video piracy
A Google vulnerability could allow bad actors to hijack video content from protected videos, according to online newspaper Jewish Business News. A flaw within the encryption technology of Widevine EME/CDM is said to hold the potential to allow attackers to
A new ransomware program making the rounds uses a simple, yet effective technique to make user files inaccessible: locking them in password-protected ZIP archives. The new threat is called Bart and shares some similarities—in the ransom note in particular—with Locky,
David Trail, 26, of Edinburgh, Scotland, will have to pay £17,000 ($22,700) as compensation and will serve 200 hours of unpaid work for selling drugs on the Dark Web and hacking his former employer. Trail was the administrator of the
According to Burrell though, the budget of the division needs to be put into context. The resources of the Operational Technology Division are divided, with the tools being developed for investigations related to national security being different from those for
A Filipino man has been charged in New Jersey with running a large and sophisticated scheme to hack into the bank and credit card accounts of celebrity customers. According to an indictment made public on Friday, Peter Locsin, 35, conspired
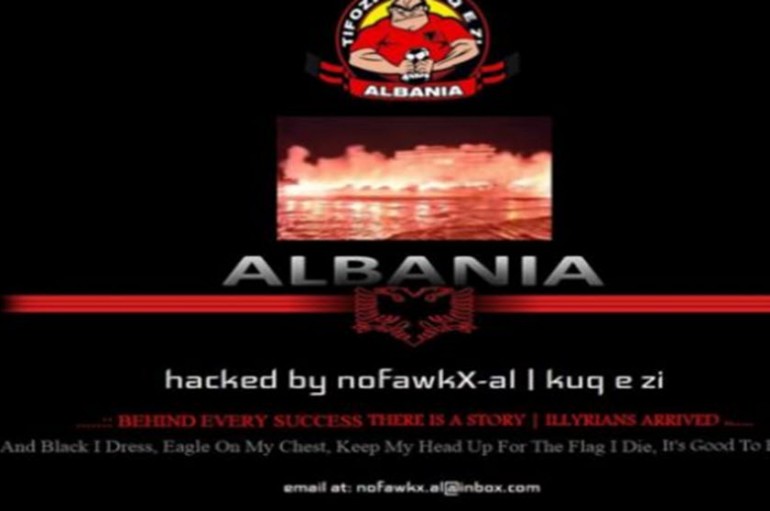
South Yorkshire Police’s website has been hacked by a group purporting to be from Albania. Following Sunday’s hack, the front page of the site showed an Albanian banner and a carousel of images including football fans at Euro 2016. It
Hackers steal $10m from Ukraine bank
Hackers have stolen $10 million from an unnamed Ukrainian bank, according to an independent IT monitoring organisation. The Kyiv branch of ISACA, the Information Systems Audit and Control Association, reported this week that the theft had occurred via the SWIFT
A hacker group has briefly overtaken the Quora account of Google CEO Sundar Pichai, which also enabled them to post on his Twitter. “We are just testing your security,” the hackers tweeted from Pichai’s account, pointing to a post on