Archive
Critical systems used by utility providers — industrial control systems (ICS) and SCADA— were never designed with security in mind. Attackers have picked up on this critical gap, and according to Threatpost, a new strain of ICS malware has now
New Android tricks for modern malware licks
Symantec engineer Dinesh Venkatesan says malware writers have one up on Google with the pillaging of a keystone trick that permits attacks on Android Marshmallow. The method was extracted from white hat proof-of-concept works published initially to show how malware
Microsoft’s search engine Bing will display more detailed warnings when users encounter potential phishing and malware sites. The company has announced it’s refining how it communicates potential threats in Bing results and to website operators using the Bing webmaster dashboard.
Facebook users this summer may have to make a choice: do they want extra privacy – or better artificial intelligence? In the coming months, according to three people close to the project, the social media company plans to release an
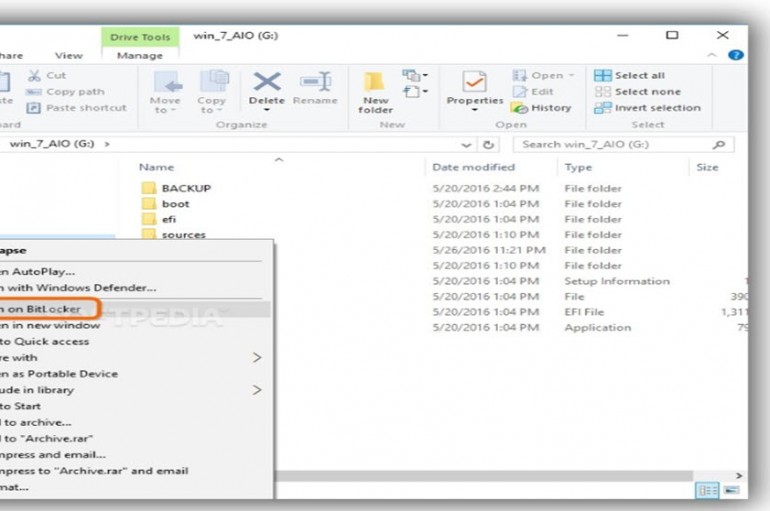
One of the many security methods available for protecting sensitive files and folders is through USB drive encryption. This way, you can take the secure devices with you and access the secret contents on any computer, as long as you
Proposed anti-encryption legislation known as “Burr-Feinstein,” filed in the wake of Apple’s legal showdown with the FBI, had such broad business ramifications that apparently common sense prevailed. According to a Reuters report, sources in Congress say the bill had trouble
At an event held during Apple’s fight with the FBI over whether it should help unlock a dead terrorist’s iPhone, CEO Tim Cook promised “We will not shrink” from the responsibility of protecting customer data —including from government overreach. Yet
The latest news only confirms the theory that Israeli firms are creating a position in the spying and surveillance industry with their ground-breaking and wide-ranging products. The latest news only confirms the theory that Israel is going places as far
The online hacktivist group, Anonymous reportedly shut down the London Stock Exchange (LSE) website last week for more than two hours as part of a protest against world’s banks and financial institutions. According to the Mail on Sunday, the attack
HACKING LAWS ARE generally intended to punish, well, hacking—not the digital equivalent of destroying the office printer on the day you quit. But when IT administrator Michael Thomas deleted a collection of files before leaving his job at the auto
Mitsubishi Outlander PHEV at risk of hacking
The Mitsubishi Outlander PHEV – UK’s best selling plug-in electric car – has become the latest car susceptible to hacking, after weaknesses in the car’s on-board Wi-Fi security allowed researchers to turn off security alarms. Security expert Ken Munro and his
The messages first appeared May 31, the Tuesday after Memorial Day. “DONALD TRUMP IS A SHAPE SHIFTING LIZARD!!” read one. “BERNIE FOR PRESIDENT,” appeared another. “WORK IS CANCELED — GO BACK HOME,” instructed a third. They were perplexing for East
There are several lessons to be learned from a data breach in which hackers gained access to Mark Zuckerberg’s social media accounts, but chief among them is probably this: Quit using the same password for multiple websites. It may be
A seemingly endless stream of high-profile data breaches have given cyber security a new impetus, bringing it very much to the forefront of conversations amongst business leaders and consumers alike. With the general cyber security industry at the height of
Top 5 VoIP Security Tips for Businesses
VoIP, short for Voice over Internet Protocol, allows businesses to make free, or very low-cost, telephone calls over the Internet. This works anywhere in the world, regardless of the equipment that the other person is using. While VoIP is a
Why Managed DNS Means Secure DNS
Home security systems are designed to keep intruders out. But even with the most advanced systems in place, vulnerabilities still exist. Something as simple as an old cellar door may provide a clear and undetected path for trespassers. The same