Archive
Millions of users of Mozilla’s Firefox web browser may be at risk, thanks to a ruling handed out by a federal judge on Monday. US District Court Judge Robert J. Bryan rejected Mozilla’s request to force the government to reveal
Four months after Google fixed the issue, a security researcher has come forward to explain how a vulnerability in Android’s Qualcomm Secure Execution Environment (QSEE) can be leveraged to compromise devices. Fixed in Google’s January Nexus Security Bulletin, the bug
Check Point today published its latest Threat Index, highlighting the most prevalent malware families being used to attack organisations’ networks and mobile devices globally in April 2016. Check Point identified 2,000 unique malware families during April, which was more than
Furtim Malware: As Stealthy as Its Name Implies
Breaking Malware recently published an analysis of a new malware called Furtim. Its name is derived from the Latin term for stealthy — and that’s exactly how it acts. Furtim attacks Windows machines. It won’t install itself if it identifies
Furtim malware can run AND it can hide
Avoiding detection is generally a top priority for any malicious code developer, but the creators of the newly discovered “Furtim” truly appear to have gone the extra mile to ensure that their malware flies under the radar. Infiltration prevention firm
An old piece of ATM malware is back, and reportedly more dangerous and harder to detect than ever. According to security researchers from Kaspersky Labs, an updated piece of malware dubbed Skimer has infected numerous Windows-based ATMs across all corners
Japan’s local mobile network NTT DoCoMo launched five new smartphones on Tuesday that will allow the government to secretly track its citizens, reported the Japan Times. In other words, the newly launched smartphones will allow the track a user’s location
Two researchers from the University of Texas have published a paper that details a new algorithm for combining two sources of entropy to obtain a higher-quality random number that can be used to bolster encryption operations with less computational resource
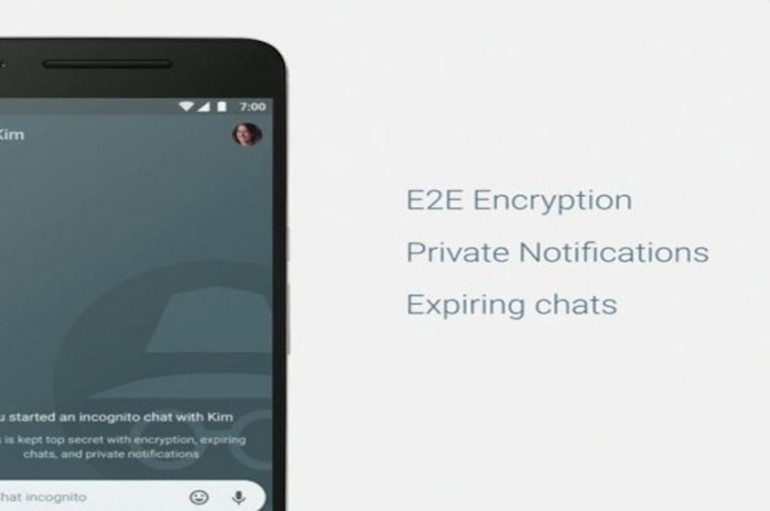
After Google’s decision not to provide end-to-end encryption by default in its new chat app, Allo, raised questions about the balance of security and effective artificial intelligence, one of the company’s top security engineers said he’d push for end-to-end encryption to
Over the past few weeks the developers of the malicious ransomware TeslaCrypt, which would encrypt files or entire computers and hold them hostage, signaled that they were closing down operations. As time went on the project’s website slowly dismantled and
Dubai Police stay ahead in combating cyber crime
Dubai: Dubai Police have come a long way in combating cyber-crime since the first case they handled in the early 90s. Major General Khamis Mattar Al Mazeina, Dubai Police Chief, spoke about a number of cyber crime cases – some
Malware-infected apps sneak into Google Play, leave Android devices wide open for attacks
The legend of vikings who siege settlements to loot their goods and set them ablaze is alive and well in the latest Android malware scenario. Apparently, not only do they still exist, but they also strike dangerously close to home.
If this malware finds any of over 400 security products installed, it won’t bother infecting…
A new strain of malware checks to see if 400 different security products are installed on a victim’s computer prior to completing installation. Yotam Gottesman, a senior security researcher at enSilo, observes that the developers of the malware, which has
Mozilla has to take another approach if it wants to discover and fix the vulnerability feds exploited to infiltrate a child porn website. Washington US District Judge Robert Bryan has thrown out the organization’s requestfor the security flaw’s details. If
Researchers have devised a method of generating random numbers that could shake up computer encryption. University of Texas computer science professor David Zuckerman and PhD student Eshan Chattopadhyay have found that a “high-quality” random number could be generated by combining
During its Google I/O 2016 conference, the technology giant announced a new application calledAllo that uses machine learning and ‘smart replies’ to streamline communications. However, it’s a mode called Incognito that is likely to become a key feature for privacy-conscious