Windows GodMode Abused by Malware
Security researchers at McAfee Labs have come across a new malware family that is abusing a secret Easter Egg in Microsoft Windows called “GodMode.”
GodMode consists of a piece of code that Microsoft left inside Windows since Vista that allows users to create a folder, give it a specific name, and automatically transforming it into a container that lists all the shortcuts to all the Control Panel settings.
Nobody knows how GodMode panels came to be, but most likely they were used by Microsoft’s staff for debugging purposes.
Users can add GodMode panels anywhere, and to create one, just make a new folder and give it the following name (You can replace GodMode with any word you wish).
GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
McAfee researchers recently revealed that they’ve seen malware that uses this trick, with a slight modification.
GodMode abused by Dynamer to open backdoor connections
The malware called Dynamer was infecting computers and in order to gain persistence it was adding a new entry to the local Windows Registry that automatically started its malicious process with every startup.
This registry key contained a slightly modified GodMode path which automatically opened and redirected users to the “RemoteApp and Desktop Connections” control panel item.
Taking into account that Microsoft categorizes Dynamer as a backdoor trojan, it appears that this is how the malware was opening connections from an infected computer to its master server. The Dynamer registry key was as follows.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
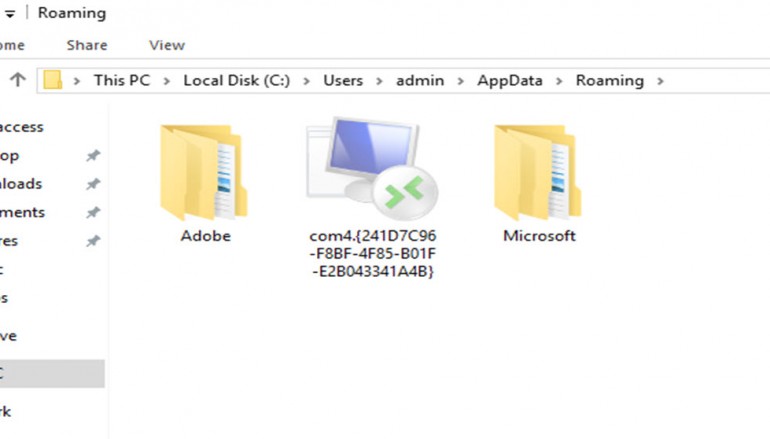
lsm = C:\Users\admin\AppData\Roaming\com4.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}\lsm.exe
As you can see, the GodMode path was slightly different in order to link directly to the “RemoteApp and Desktop Connections” control panel item.
The malware was almost unremovable. Almost.
Additionally, the GodMode string was also replaced with com4. While the GodMode string was never obligatory to create a GodMode panel and users have often replaced it with anything they wanted, using com4 has some repercussions.
“The malware author has attempted to give this directory eternal life, by prepending the name ‘com4’,” Craig Schmugar from McAfee Labs explained. “Such device names are forbidden by normal Windows Explorer and cmd.exe commands and Windows treats the folder as a device, thus preventing users from otherwise easily deleting the folder with Explorer or typical console commands.”
Nevertheless, the McAfee team found a way to delete such malicious items from someone’s computer. In this case, users could run the following command to delete the malware. In case you find Dynamer in other places than your AppData folder, just make sure to alter the CLI command with the proper file path.
rd “\\.\%appdata%\com4.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}” /S /Q
Source | SoftPedia