
This Hacker’s Account of How He Infiltrated Hacking Team Says a Lot About Digital Security
You may remember that last year, a hacker exposed the inner workings of Hacking Team, a company that makes spyware for governments. Now that the dust has settled down, someone claiming to be the hacker has posted all the details on how he did it.
The hack itself was executed using a common weakness: first, an embedded device within the network was found with a known zero-day weakness. From there, the hacker was able to get into an unencrypted backup and find the passwords for a Domain Admin server, which basically gave him the keys to the kingdom.
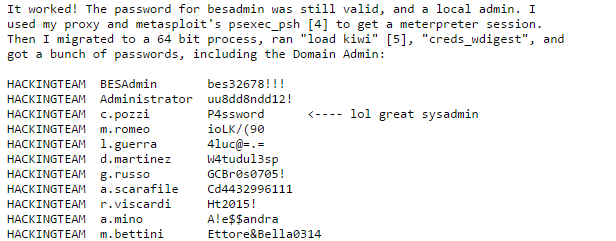
There wasn’t one gaping security flaw: rather, it was a vulnerability in one tiny device (probably something like a router or network switch), which allowed the hacker to escalate his attack, through a series of small errors like unencrypted backups. But using those small vulnerability, the hacker got everything—emails, documents, and even the source code for Hacking Team’s software.
The post is actually worth reading—it’s reasonably intelligible, and gives a lot of insight into how hacking works outside of the movies.
Source | Gizmodo





