Source Code for IoT botnet responsible for World’s largest DDoS Attack released Online
With rapidly growing Internet of Thing (IoT) devices, they have become a much more attractive target for cybercriminals.
Just recently we saw a record-breaking Distributed Denial of Service (DDoS) attacks against the France-based hosting provider OVH that reached over one Terabit per second (1 Tbps), which was carried out via a botnet of infected IoT devices.
Now, such attacks are expected to grow more rapidly as someone has just released the source code for IoT botnet, which was ‘apparently’ used to carry out world’s largest DDoS attacks.
Internet of Things-Botnet ‘Mirai’ Released Online
Dubbed Mirai, the malware is a DDoS Trojan that targets BusyBox systems, a collection of Unix utilities specifically designed for embedded devices like routers.
The malware is programmed to hijack connected IoT devices that are using the default usernames and passwords set by the factory before devices are first shipped to customers.
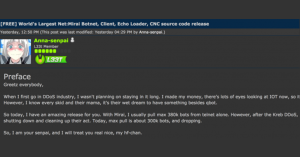
Spotted by Brian Krebs, the “Mirai” source code was released on Hackforums, a widely used hacker chat forum, on Friday.
However, there is no concrete evidence that this is the same botnet malware that was used to conduct record-breaking DDoS attacks on Krebs’ or OVH hosting website.
Reportedly, the attack code has built-in scanners that look for vulnerable smart devices in homes and enroll them into a network of Botnet, that hackers and cyber criminals can then use in a DDoS attack to temporarily shut down any website.
The hacker, nicknamed “Anna-senpai,” who released the Mirai source code said they have “made their money…so it’s time to GTFO.”
“So today, I have an amazing release for you,” Anna-senpai wrote. “With Mirai, I usually pull max 380k bots from telnet alone. However, after the Kreb [sic] DDoS, ISPs been slowly shutting down and cleaning up their act. Today, max pull is about 300k bots, and dropping.”
Even after the above explanation, I am still wondering why the malware’s author chose to dump the code online over making big money.
Beware: Don’t Download It Or Use at your own risk!
I apologize, if you are looking for the download link. We came across hundreds of such malware and their source codes, but ethically we don’t prefer to promote them through our articles because that could indirectly advantage more blackhat hackers to cause further damages.
It is not at all surprising to believe so, as we have seen several cases in past years, when hackers have taken advantage of trending or hot events (or incidents), in this case record-breaking DDoS attack, to post and distribute their backdoored malware strategically.
Now that the malware is publicly released, anyone can download and use it to infect a large number of devices worldwide to create their own IoT botnet.
And if the code contains any backdoor, it would not only compromise the user who downloads it from the hacking forum but also hijacks those who are part of that user’s botnet network.
So, we advise beginner and our enthusiast readers not to rush to download Mirai IoT Botnet files.
Since manufacturers of IoT devices majorly focus on performance and usability and ignore security measures and encryption mechanisms, they are routinely being hacked and used as weapons in cyber attacks.
Just recently we reported about vulnerable D-Link routers that are programmed in such a way that they contain several backdoors, which allow attackers to remotely hijack and control them, as well as network, leaving all connected devices vulnerable to cyber attacks.
So, if you own one or more IoT devices, the first thing you need to do in order to protect yourself against cyber attacks is change those default credentials.
Source | thehackernews