Latest News
Microsoft Patches Serious Crypto Flaw Found by NSA
Microsoft has kicked off the new decade with fixes for half a century of vulnerabilities, including one discovered by the
App Leaks Thousands of Baby Photos and Videos Online
An app designed to record and share milestones in a child’s development has leaked thousands of images and videos of
Play Store Still Peppered with Fleeceware Apps
Four months after fleeceware’s initial exposure, Android users who purchase “subscriptions” to apps from the Google Play Store are still
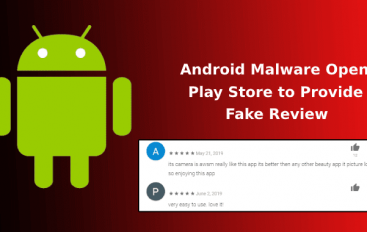
Hackers Install Malware on Android Devices That Open Google Play Store to Provide 5* Ratings & Fake Reviews for Malicious Apps
Researchers discovered a new type of strange malware that targeting android device, and use the victim’s mobiles to provide fake
CISA Releases Test Tool for Citrix ADC and Gateway Vulnerability – Sysadmins Can Test Now
CISA has released a new tool for administrators and users to check for Citrix Application Delivery Controller (ADC) and Citrix
Texas School District Loses $2.3m in Phishing Raid
A Texas school district has found out the hard way that phishing attacks remain a serious financial threat to organizations
Aussie Bushfires Donation Site Hit by Magecart Thieves
A website set-up to accept donations for victims of the devastating Australian bushfires has become a victim itself — of
#THIREurope: How Target Improved Its Threat Hunting Capabilities
A threat hunting team can be better enabled when given the time and interest to focus on what it wants.
Seattle to Host Major New Cybersecurity Event
The verdant city of Seattle is to host a new three-day event dedicated to cybersecurity and the cloud. CSA SECtember
TSA Desires “Cybersecurity by Design”
The United States Transport Security Administration (TSA) has publicly announced that it’s on a “quest to merge cybersecurity and information
#THIREurope: APT Groups Now Using Similar Tools in Espionage and Cybercrime Attacks
Speaking at the SANS Institute Threat Hunting and IR Europe conference in London, Tom Hall, principal consultant for incident response
Citrix Admins Urged to Act as PoC Exploits Surface
IT administrators are being urged to put in place mitigations for a serious Citrix vulnerability which the vendor says won’t
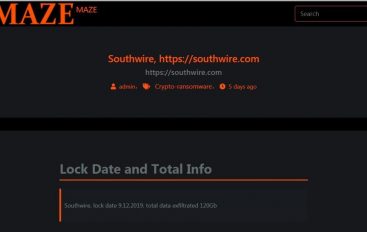
Maze Ransomware Operators Leak 14GB of Files Stolen from Southwire
The Maze ransomware gang has released 14GB of files that they claim were stolen from one of its victims, the
The U.S. Government Funded Smartphones Comes Pre-installed With Unremovable Malware
Security researchers from Malwarebytes found pre-installed malware on UMX U683CL handsets. The phones are made under the Lifeline program to
Top 10 Best Linux Distro Operating Systems For Ethical Hacking & Penetration Testing – 2020
There are different OS for Hacking and Penetration Testing with Linux distro is dedicatedly developed for Security Researchers or Ethical
Hundreds of Millions of Broadcom Modems “Haunted” by New Bug
Security researchers are warning of a new critical vulnerability affecting multiple cable modem manufacturers that use Broadcom chips — exposing