New Dramer Android Hack lets Apps take Full control (root) of your Phone
Earlier last year, security researchers from Google’s Project Zero outlined a way to hijack the computers running Linux by abusing a design flaw in the memory and gaining higher kernel privileges on the system.
Now, the same previously found designing weakness has been exploited to gain unfettered “root” access to millions of Android smartphones, allowing potentially anyone to take control of affected devices.
Researchers in the VUSec Lab at Vrije Universiteit Amsterdam have discovered a vulnerability that targets a device’s dynamic random access memory (DRAM) using an attack called Rowhammer.
Although we are already aware of the Rowhammer attack, this is the very first time when researchers have successfully used this attack to target mobile devices.
What is DRAM Rowhammer Attack?
The Rowhammer attack against mobile devices is equally dangerous because it potentially puts all critical data on millions of Android phones at risk, at least until a security patch is available.
The Rowhammer attack involves executing a malicious application that repeatedly accesses the same “row” of transistors on a memory chip in a tiny fraction of a second in a process called “Hammering.”
As a result, hammering a memory region can disturb neighboring row, causing the row to leak electricity into the next row which eventually causes a bit to flip. And since bits encode data, this small change modifies that data, creating a way to gain control over the device.
In short, Rowhammer is an issue with new generation DRAM chips in which repeatedly accessing a row of memory can cause “bit flipping” in an adjacent row that could allow anyone to change the value of contents stored in the memory.
Is Your Android Phone Vulnerable?
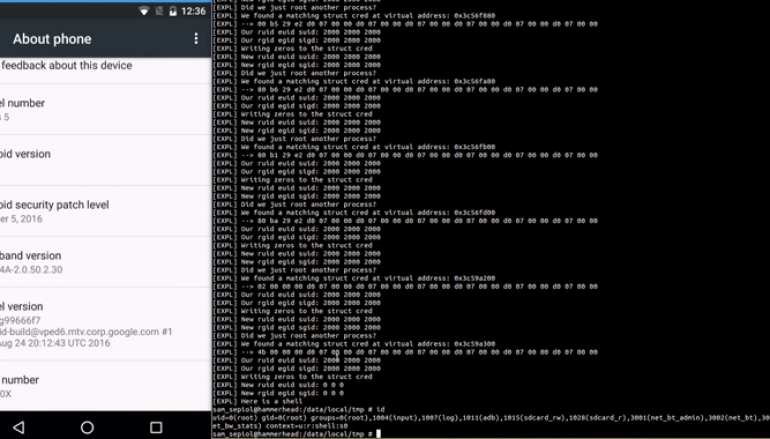
To test the Rowhammer attack on mobile phones, the researchers created a new proof-of-concept exploit, dubbed DRAMMER, and found their exploit successfully altered crucial bits of data in a way that completely roots big brand Android devices from Samsung, OnePlus, LG, Motorola, and possibly other manufacturers.
The researchers successfully rooted Android handsets including Google’s Nexus 4 and Nexus 5; LG’s G4; Samsung Galaxy S4 and Galaxy S5, Motorola’s Moto G models from 2013 and 2014; and OnePlus One.
“Not only does our [DRAMMER] attack show that practical, deterministic Rowhammer attacks are a real threat to billions of mobile users, but it is also the first effort to show that Rowhammer is…(reliably exploitable) on any platform other than x86 and with a much more limited software feature set than existing solutions,” the researchers wrote in their paper [PDF] titled, “Drammer: Deterministic Rowhammer Attacks on Mobile Platforms.”
Source | thehackernews





