Microsoft’s BITS file transfer tool fooled into malware distribution
Researchers at Dell SecureWorks have spotted a new and dangerous way to misuse of Microsoft’s Background Intelligent Transfer Service (BITS).
While working on a customer clean-up project, SecureWorks staff found that attackers had created self-contained BITS tasks that didn’t appear in the registries of affected machines, and their footprints were limited to entries on the BITS database.
The attack was spotted on a Windows 7 machine in an academic administration environment.
The scripts ran the usual gamut of malicious activity: pulling malware from a remote server, running an installation script, and running a clean-up script after the payload was installed.
Once a transfer was complete, BITS launched a notification program which:
- Created and launched a Windows batch script to finalise and clean up the BITS job entry, and check the download;
- Launched the downloaded program (with checks in case it got left behind in the tmp directory);
- Deleted itself on completion.
SecureWorks’ advice for sysadmins: if you’ve remediated a host, but it continues to generate network or host alerts, find out whether there are poisoned BITS tasks still pending.
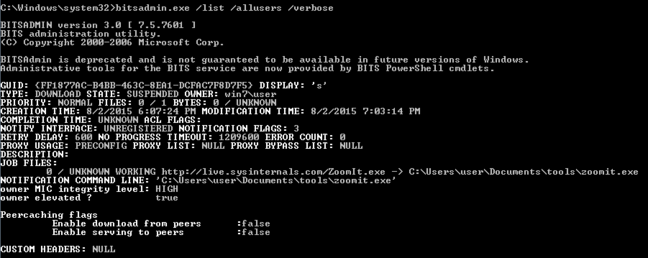
“One way to enumerate these tasks is to execute the bitsadmin client from a cmd.exe session with elevated privileges (bitsadmin /list /allusers /verbose)”, the post notes, producing the output below.
The post also lists the malware-hosting domains observed in this attack. ®
Source | TheRegister