Posts From CCME
Zoom has brought former Facebook CSO Alex Stamos on board to bolster a new security push, as reports emerged that Google and the US Senate have told users to avoid the video conferencing platform. As promised by CEO Eric Yuan
Half of UK Adults Exposed to #COVID19 Fake News
Half of UK adults have been exposed to online misinformation about COVID-19, making access to credible news sources increasingly important, according to regulator Ofcom. Ofcom is surveying 2000 adults each week to better understand how online users are receiving information
Leading cloud backup, recovery and restore software provider Asigra Inc., today announced that in a recent feature by Storage Newsletter, the company has ranked number one in a list of the Top 25 Cloud Backup Enablers. Storage Newsletter highlights the
FBI Warns of Cloud-Based BEC Attacks
The Federal Bureau of Investigation (FBI) has issued a warning over cloud-based business email compromise (BEC) scams that have cost US companies more than $2bn. A BEC is a sophisticated scam targeting businesses that perform electronic payments, such as wire
New Version of Privacy and Anonymous Operating System Tails 4.5 Released with Fix for Security Issues
Tails is a security-focused Debian based live operating system, no installation required. You can use the live operating system on any computer from a USB stick or a DVD. The operating system aimed to provide privacy and anonymity, all its
It wasn’t quick or simple, but researchers at Cisco Talos have managed to break into devices secured with biometric authentication. New research published today by Paul Rascagneres and Vitor Ventura revealed that manufactured fingerprints, created using 3D printing technology and
Microsoft has warned that cyber-criminals are preying on people’s vulnerable psychological states during the COVID-19 pandemic to attack businesses. During a virtual press briefing, the multinational technology company provided data showing how home working and employee stress during this period
This week, NASA sent out a memo to its personnel warning of a significant increase in the cyberattacks during the Coronavirus outbreak. NASA sent out a memo to its personnel warning of a significant increase in cyberattacks on the agency while
Accenture Acquires Revolutionary Security
Accenture has acquired a privately held Philadelphia company specializing in enterprise cybersecurity for information technology and operational technology environments. Global professional services company Accenture announced its acquisition of Revolutionary Security on April 7. The financial terms of the deal were
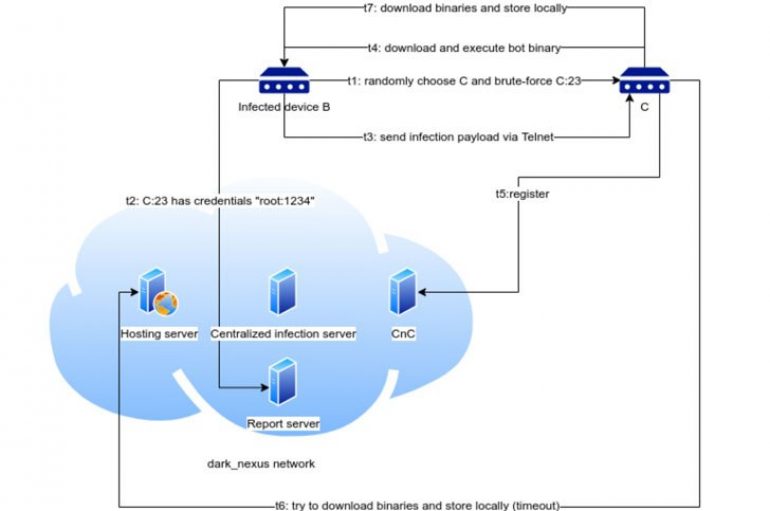
Cybersecurity researchers discovered a new IoT botnet, tracked as Dark Nexux, that is used to launch distributed denial-of-service (DDoS) attacks. Dark Nexux is the name of a new emerging IoT botnet discovered by Bitdefender that is used to launch DDoS
A quarter of organizations have suffered a breach related to their application development process over the past year, with most of these coming via open source components, according to Sonatype. The DevOps automation firm’s 2020 DevSecOps Community Survey is based
Over 350,000 Exchange servers around the world are still exposed to a critical vulnerability patched by Microsoft in February and actively being exploited in the wild, according to Rapid7. The security vendor deployed its Project Sonar scanning apparatus to find
Europe’s data protection tsar has called for a pan-EU COVID-19 health tracking app to avoid fragmented member state approaches which may not follow privacy-by-design principles. European data protection supervisor (EDPS), Wojciech Wiewiorowski, said his team is already cooperating with other
The internet is proving to be the most valuable resource at the moment, and opportunities will await those who adapt and are more prepared. Speaking as part of the Akamai Edge conference, delivered as a virtual summit, Andy Ellis, CSO
The drug testing firm Hammersmith Medicines Research LTD (HMR), which performs live trials of Coronavirus vaccines, discloses a data breach. Hammersmith Medicines Research LTD (HMR), a London-based company that carries out clinical trials for new medicines and that is on standby to
The Android XHelper malware was first identified in October 2019, it is known for its persistent capabilities. Once it gets installed to the device, the malware remains active even after the user deletes it and restore the factory settings. The