Posts From CCME
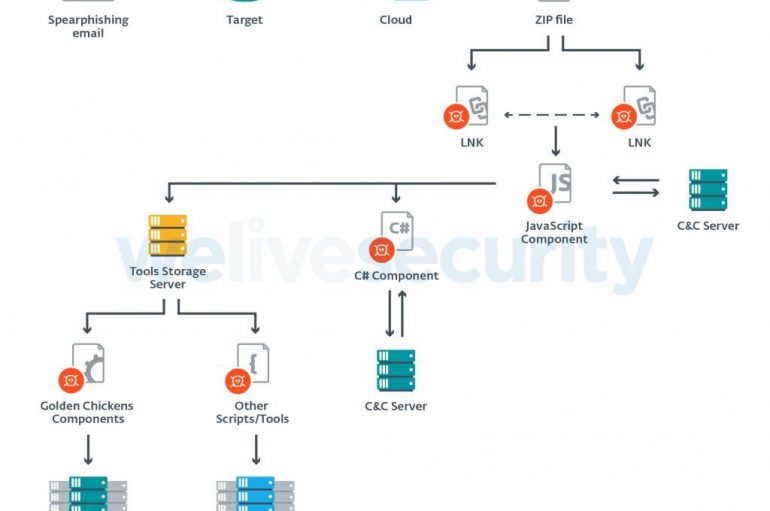
A threat actor tracked as Evilnum targeted financial technology companies, mainly the British and European ones, ESET researchers reported. Evilnum threat actor was first spotted in 2018 while using the homonym malware. Over the years, the group added new tools
A platform created by the SANS Institute to teach core cybersecurity skills is now available to students and young adults across the Middle East and Africa. CyberStart Game provides a gamified learning experience that can be used in the classroom
Vulnerability Found in Kasa Camera
A hobby farmer on the hunt for a vegetable-eating critter has discovered a flaw in a popular outdoor home security camera. Midwesterner Jason Kent purchased a Kasa camera to help identify whatever creature it was that had been eating his
Google Bans Stalkerware Ads From its Pages
Google has updated its advertising policy to effectively ban stalkerware from its pages. The tech giant announced the move in an update to its Enabling Dishonest Behavior policy. Although it didn’t mention the category by its more commonly known name,
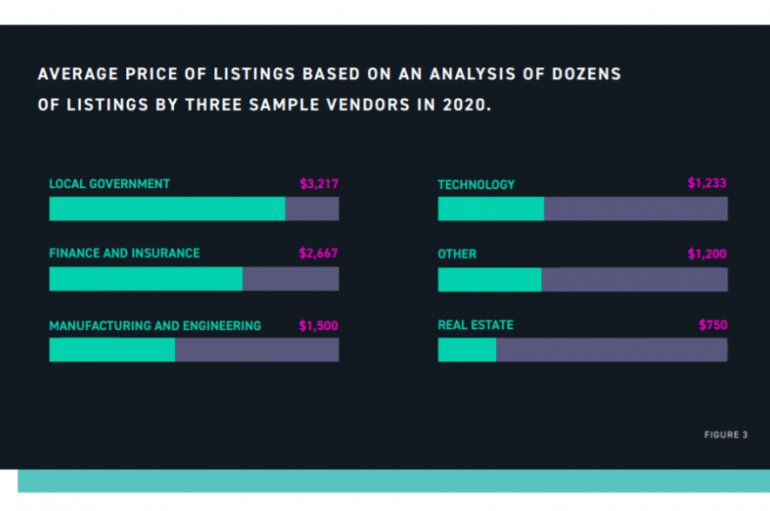
UK businesses have been slow to move to the cloud because of concerns over data loss and compliance breaches, according to the 2020 UK Veritas Databerg Report. It showed that just 47% of corporate data is currently stored in the
KingComposer, a WordPress plugin found installed with over 100,000 WordPress sites found vulnerable to Reflected Cross-Site Scripting. The vulnerability was found by the Wordfence security team with KingComposer Drag and Drop page building plugin. The vulnerability can be exploited by
Zoom Zero-Day Bug Hits Legacy Windows Users
Zoom is scrambling to fix another zero-day vulnerability in its Windows client, this time potentially leading to arbitrary remote code execution. Acros Security CEO, Mitja Kolsek, revealed the news in a blog post, claiming that the researcher who found the
UK pubs and restaurants are exposing their customers to the risk of phishing attacks as consumers head back to the bar after a long period of lockdown, according to Proofpoint. The security vendor analyzed the co.uk and .com domains of
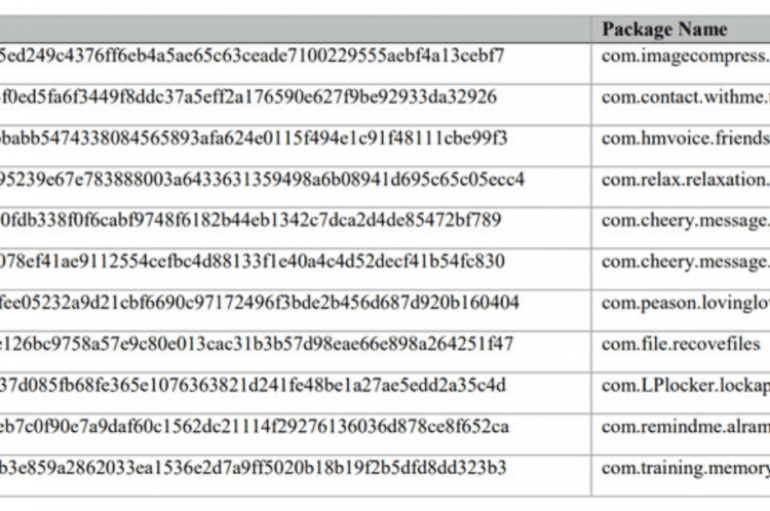
Researchers from Malwarebytes have found yet another phone with pre-installed malware via the Lifeline Assistance program sold in the United States. Researchers at Malwarebytes have found malware pre-installed on smartphones sold in the United States, this is the second time
Zoom 0day Vulnerability Let Remote Attacker to Execute Arbitrary Code on Victim’s Computer
A new remote code execution “0day” flaw with Zoom Client for Windows allows remote attackers to execute arbitrary code on Windows computer where the vulnerable version of Zoom client installed. The vulnerability was found by a researcher who wants to
Check Point research discovered that the Joker (aka Bread) Android malware once again has bypassed protections implemented by Google for its Play Store. Researchers from security firm Check Point discovered samples of the Joker (aka Bread) malware were uploaded on
How to Protect Your Smart Home from IoT Threats?
Our world is increasingly becoming digital as we are moving towards a society that is interconnected through a web of internet-enabled devices. We call this network or technology IoT (Internet of Things) which is also understood as ‘smart homes’. But
Cyber-Attack Downs Alabama County’s Network
A suspected ransomware attack has caused the temporary closure of an Alabama county’s computer network. Chilton County implemented a shutdown after being targeted by a suspected ransomware attack on the morning of July 7. County Commission Chairman Joseph Parnell announced
Just 5% of Brits are able to recognize all scam emails and texts, a study from Computer Disposals Limited has found. Scam emails purporting to be from Facebook were shown to be most likely to trick people. Additionally, participants found
More than 15 billion username and passwords are available on cybercrime marketplaces, including over 5 billion unique credentials, states the experts. A report published by security firm Digital Shadows revealed the availability of more than 15 billion credentials shared on
Security professionals are struggling to effectively manage high volumes of security alerts. According to the 2020 State of SecOps and Automation Report, a study conducted by Dimensional Research on behalf of Sumo Logic, managing the sheer volume of security alerts