Posts From CCME
A vulnerability in the Guardzilla home video surveillance system could be exploited by users to watch Guardzilla footage of other users. The Guardzilla All-In-One Video Security System is an indoor video surveillance solution. The flaw was discovered by the researchers
A critical vulnerability affects Schneider Electric electric vehicle charging stations, the EVLink Parking systems. EVlink Parking charging solutions are usually in parking environments, including offices, hotels, supermarkets, fleets, and municipals. According to the company, the issue is tied to a
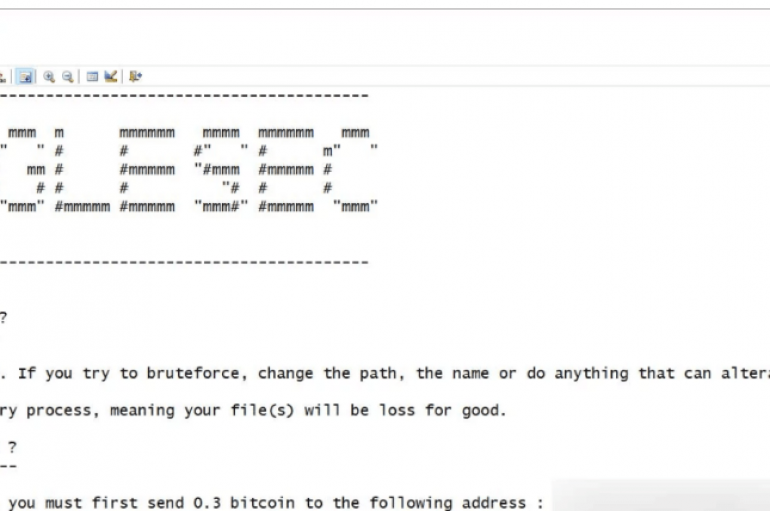
Since November, a new ransomware called JungleSec has been infecting servers through unsecured IPMI (Intelligent Platform Management Interface) cards. Security experts at BleepingComputer wrote about a new ransomware called JungleSec that is infecting victims through unsecured IPMI (Intelligent Platform Management
UK Launches Long-Awaited Cyber Skills Strategy
The UK government has launched a new cybersecurity skills strategy designed to reduce industry shortages, and a new independent body to help shape the future of the profession. The Initial National Cyber Security Skills Strategy sets out not only to
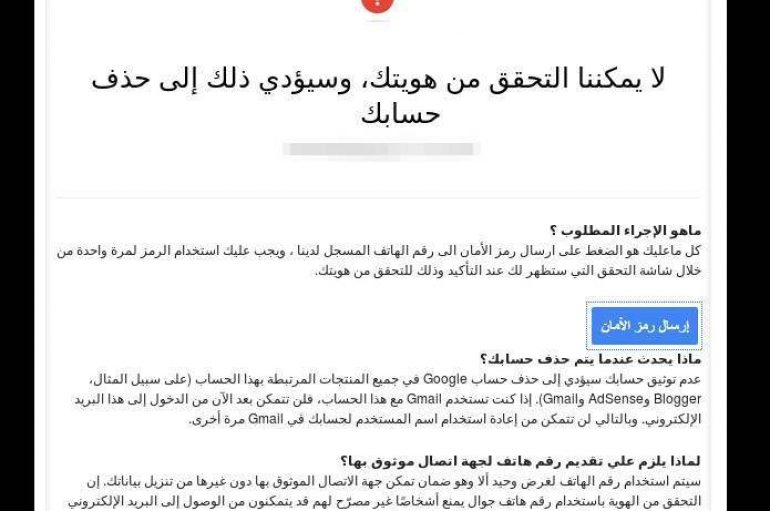
Amnesty International warns of threat actors that are launching phishing attacks aimed at bypassing Gmail, Yahoo 2FA at scale Amnesty International published a report that details how threat actors are able to bypass 2FA authentication that leverages text message as
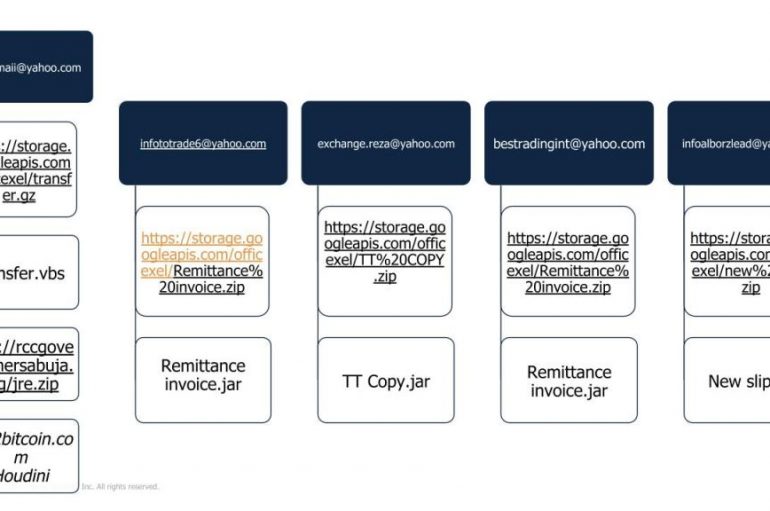
Researchers at Menlo Labs uncovered a malicious email campaign targeting employees of banks and financial services companies abusing Google Cloud Storage. The campaign targeted organizations in the US and the UK, the attackers have been abusing Google Cloud Storage to
Nearly 20,000 Orange modems are being targeted thanks to a vulnerability leaking their SSID and Wi-Fi passwords, researchers at Bad Packets have warned. The firm’s honeypots first picked up the attack traffic targeting Orange Livebox ADSL modems. After conducting a
The personal data of more than half a million staff and students of San Diego high schools from the past decade is now likely in the hands of hackers, it has emerged. A statement from the San Diego Unified School
New App Protects User Data on the Internet
In response to the issues of data privacy questions that have erupted in the aftermath of the Facebook-Cambridge Analytical scandal, a startup, FigLeaf, co-founded by CEO Slava Kolomeichuk and CRO Yuriy Dvoinos, is developing an app that will help users
Hacking the Twinkly IoT Christmas lights
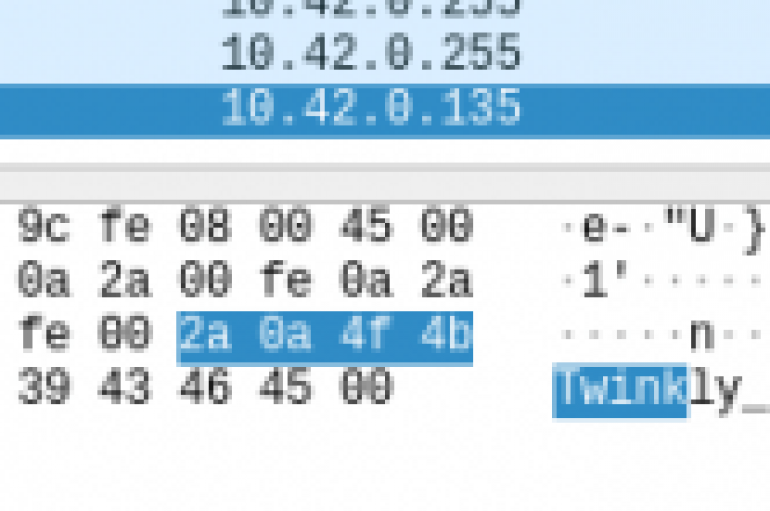
Security researchers discovered some flaws in the Twinkly IoT lights that could be exploited display custom lighting effects and to remotely turn off them. Security researchers from MWR InfoSecurity have discovered some flaws in the Twinkly IoT lights that could
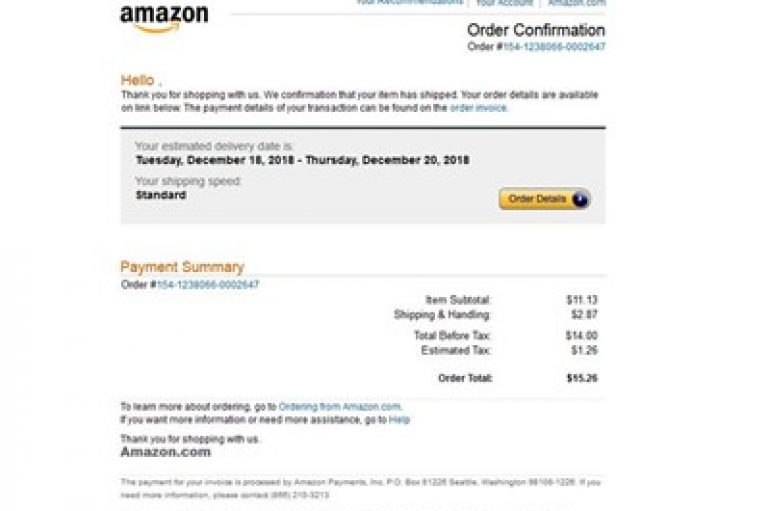
Amazon Order Confirmation Phishing Scam
All those who have relied upon the e-commerce giant Amazon to order their holiday gifts should heed caution when receiving order confirmation emails, as EdgeWave reportedly discovered a new and highly sophisticated malspam campaign sending fake Amazon order confirmation messages.
Cisco Adaptive Security Appliance (ASA) Software is affected by a vulnerability that could be exploited by an attacker to retrieve files or replace software images on a device. A privilege escalation vulnerability tracked as CVE-2018-15465 affects the Cisco Adaptive Security
Privacy Legislation Might Have Stopped Facebook
In the aftermath of an extensive New York Times investigation into Facebook’s data privacy regulations and whether the company violated the privacy and public policy regulations of the Federal Trade Commission, Sen. Amy Klobuchar (Minn.) said that it is time
Caribou Coffee notified customers a payment card breach that hit more than 260 of its stores in the United States. A payment card breach hit over 260 Caribou Coffee stores, the company owned by German JAB Holding Company detected the
Criminal Charges Filed in DDoS-for-Hire Services
Efforts to take down multiple domains that offered distributed denial-of-services (DDoSs) for hire were successful and resulted in another announcement from the Justice Department (DOJ), which yesterday declared that it had seized 15 internet domains, as well as filed criminal
Air Force Fixes 120 Bugs, Pays $130K in Bounties
The US Air Force‘s third bug bounty program has concluded after a month-long hacking period, which ran from October 19 to November 22, 2018. As a result of their research findings, hackers were awarded more than $130,000 in bounties. According