Posts From CCME
Microsoft is warning of an active spam campaign targeting European languages that leverages an exploit to infect simply by opening the attachment. Microsoft issued a warning on Friday about an ongoing spam campaign that is targeting European users. Spam messages
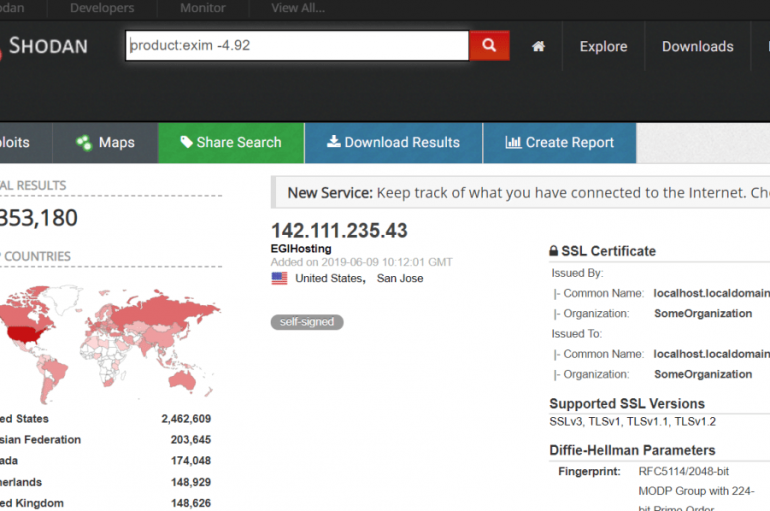
Critical Remote command execution vulnerability that affected Exim Email Server versions 4.87 to 4.91 let a local attacker or a remote attacker(with limited boundary) can execute an arbitrary command and exploit the server. Exim is a mail transfer agent which
Sites of colleges and universities are constantly subject to DDOS attacks. But who does it? do students really need to drop sites?” Hacking is a major vice of this generations young adult. Usually, it starts with the basics like hacking
Millions of Exim mail servers are exposed to attacks due to a critical vulnerability that makes it possible for unauthenticated remote attackers to execute arbitrary commands. A critical vulnerability affects versions 4.87 to 4.91 of the Exim mail transfer agent
Critical RCE Affects Older Diebold Nixdorf ATMs
Automated teller machine vendor Diebold Nixdorf has released security updates to address a remote code execution vulnerability in older ATMs. Diebold Nixdorf discovered a remote code execution vulnerability in older ATMs and is urging its customers in installing security updates
The cyber world is a weird world and cell phones have added a new dimension to it. You can’t judge your friends and enemies in this virtual world. The proliferation of mobile devices in our lives have handed new life
SanboxEscaper, an anonymous hacker came back and leaked an another Windows zero-day PoC that exploits already patched (CVE-2019-0841) local privilege escalation vulnerability that resides in Windows 10. This is a second zero-day that bypass CVE-2019-0841, An elevation of privilege vulnerability
New Adware Found in 200+ Google Play Apps
A new adware known as BeiTaAD was found embedded in 238 applications in the official Google Play store and have been installed by 440 million Android users, according to security researcher Kristina Balaam of Lookout. “BeiTaAd is a well-obfuscated advertising
Entrust Datacard announced today that it has completed its acquisition of Thales’ General Purpose Hardware Security Module (GP HSM) business, nCipher Security. With this acquisition Entrust Datacard enhances its existing public key infrastucture (PKI) and SSL offerings, which the company
Cloud migration is the process of moving applications into the public and private cloud infrastructure to achieve cloud’s agility, resiliency and scalability drive business growth. Migrating to the cloud infrastructure provides the ability for the business to change the IT
Iranian MuddyWater APT Hackers Adds New Exploits in Their Hacking Arsenal to Attack Government Networks
Threat actors from MuddyWater APT groups now add a new set of latest exploits to their hacking arsenal and tactics, techniques and procedures (TTPs) to target government entities and telecommunication sectors. Iran sponsored MuddyWater group operating by advanced persistent threat
Researchers have discovered over 40,000 Kubernetes and Docker container hosting devices exposed to the public internet through misconfigurations. Palo Alto Networks’ Unit 42 revealed the results of its latest research in a blog post yesterday. The discovery was made via
GateHub Users Lose $9.7m to Hackers
Two cryptocurrency firms have come under attack over recent days with users of one, GateHub, suffering losses estimated at nearly $9.7m. The cryptocurrency wallet service provider sounded the alarm in a statement on Thursday, claiming an investigation had been started
A new botnet tracked as GoldBrute is scanning the web for Windows machines with Remote Desktop Protocol (RDP) connection enabled. A new botnet tracked as GoldBrute has appeared in the threat landscape, it is scanning the web for Windows machines
The Cryptocurrency startup Komodo hacked itself to protect the funds of its users and avoid that hackers steal them exploiting a flaw in its Agama wallet. The story I’m going to tell you is amazing, the Cryptocurrency startup Komodo hacked
Frankenstein Campaign: Threat Actors Put Together Open-Source Tools for Highly-Targeted Attacks
Cisco Talos experts uncovered a new wave of attacks tracked as Frankenstein campaign, attackers used tools built by combining four open-source techniques. Security experts at Cisco Talos uncovered a series of highly targeted attacks, tracked as Frankenstein campaign, hackers used