Posts From CCME
Estee Lauder is the latest big-name brand to suffer an embarrassing data leak after a researcher discovered 440 million records including plain text emails exposed via an online database. Security Discovery’s Jeremiah Fowler made the discovery on January 30, claiming
Google continues to enhance the safety of Google Play with continuous improvements, enhancements, and teams to fight against malicious apps and developers. Google Play Protect is built-in malware protection for Android, it was introduced in the year 2017, aiming to
Electric scooters, also called e-scooters, are a popular method of transportation in large cities. They are small, portable, and can zip around sidewalks and in between pedestrians with ease. Unfortunately, their popularity isn’t just with law-abiding citizens. Xiaomi M365 scooters
American bank Fifth Third has come under fire for sending customers a cryptic breach disclosure letter judged to be “vague and deceptive” by a consumer group. Fifth Third wrote to customers after discovering that at least two of its employees
Speaking on a panel at the TEISS conference in London on the theme of threats in the supply chain, chair Raef Meeuwisse asked where the supply chain sits in a company’s overall risk. Mike Seeney, head of supply chain information
Great Britain’s three nations are not in agreement over the use of facial recognition technology by police forces. The technology, which can be legally used by police in Wales, was officially introduced by England’s Metropolitan Police Service in East London
At The European Information Security Summit in London, Dr Stephanie Hare, author of the forthcoming book Technology Ethics, reflected on the need for ethical frameworks in technology. Technology ethics engages with a problem that no one has solved to anyone’s
The FBI’s Internal Crime Complaint Center (IC3) released the FBI 2019 Internet Crime Report, a document that outlines cybercrime trends over the past year. Here we are to analyze the annual FBI 2019 Internet Crime Complaint Center (IC3), one of the
Speaking at The European Information Security Summit in London, Helen L, technical director for sociotechnical security at the National Cyber Security Centre, discussed strategies for effective password management within the enterprise. Helen L challenged common, traditional password management strategies, saying
Canadian Cabinet Ministers Get Hacking Hotline
An around-the-clock phone line to report suspected cyber-attacks has been created for federal cabinet ministers in Canada. Newly released documents show that officials at the Canadian Centre for Cyber Security (CCS) set up the 24/7 telephone service last year to
Speaking at The European Information Security Summit in London, Stephen Eckersley, director of investigations at the Information Commissioner’s Office, outlined the privacy watchdog’s expectations for 2020 and beyond with particular focus on regulations and data protection. “We are still coming
At The European Information Security Summit in London, Thom Langford, founder of TL(2) Security, said that effective storytelling is important to security professionals if they want to evoke reactions, behaviors and actions from others. “Stories are important to us as
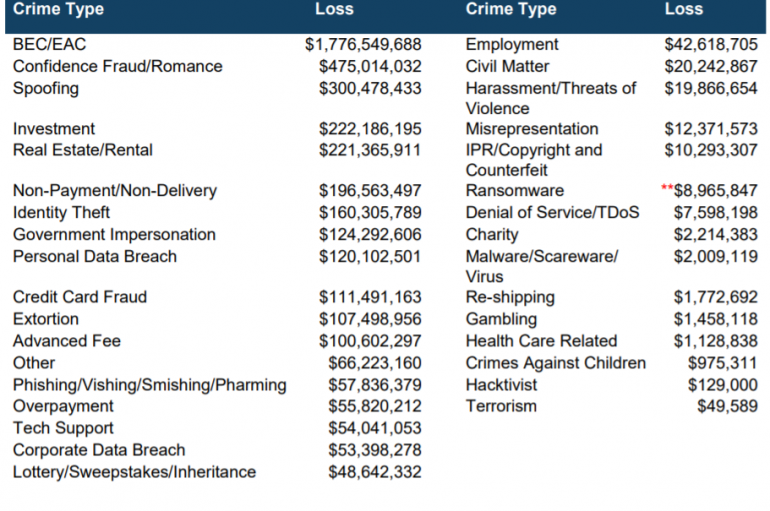
FBI: BEC Losses Soared to $1.8 Billion in 2019
Losses from business email compromise (BEC) attacks soared by hundreds of millions of dollars over the past year, to once again account for half of all cybercrime losses reported to the FBI. BEC scammers made nearly $1.8 billion in 2019,
Microsoft Fixes 99 Problems This Patch Tuesday
Microsoft has fixed almost a century of CVEs this month, although experts suggest the workload shouldn’t be too hard on admins. The 99 vulnerabilities fixed this month feature 12 critical CVEs, including one zero-day, and another four that have been
A Swiss company thought to have sold among the most secure encryption products in the world was actually owned by US and German intelligence, allowing the CIA and BND to spy on allies and enemies around the world, it has
A security expert discovered that the Cosmetic firm Estée Lauder exposed 440 million records online in a database that was left unsecured. The security expert Jeremiah Fowler discovered an unsecured database belonging to the Cosmetic firm Estée Lauder that contained