Archive
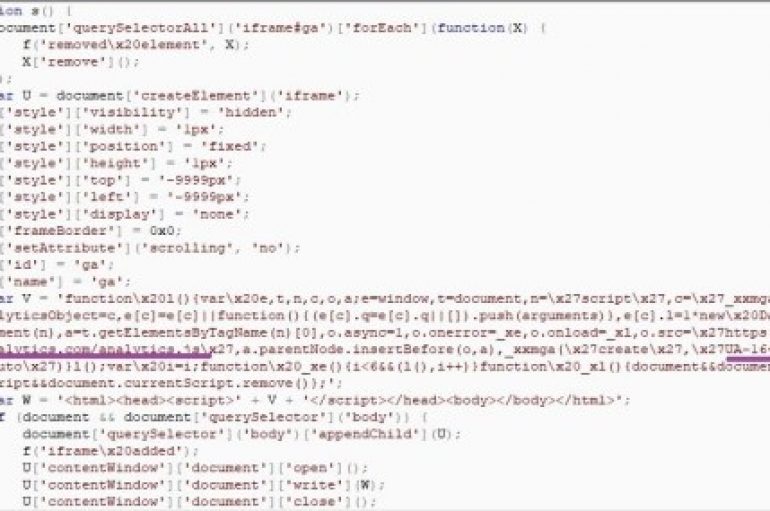
Security researchers at Kaspersky uncovered a web skimming campaign leveraging Google Analytics service to steal user data. Recently, researchers at Kaspersky identified several web skimming attacks that abused Google Analytics service to exfiltrate data stolen with an e-skimmer software. Threat
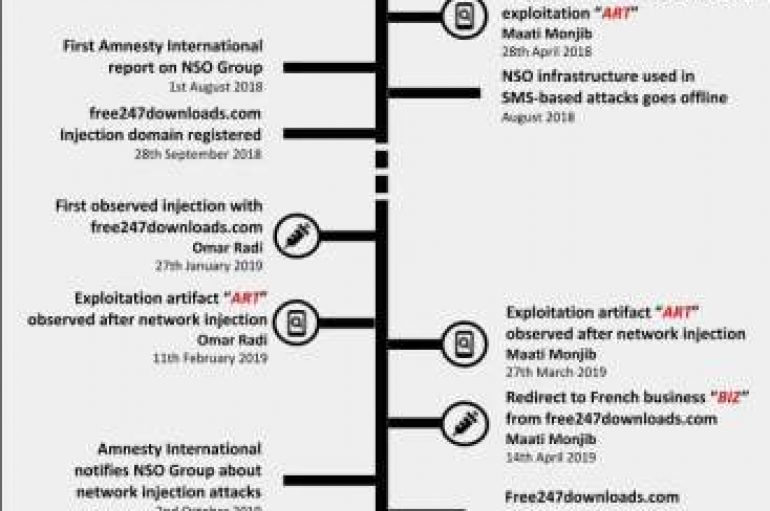
Researchers at Amnesty International collected evidence that a Moroccan journalist was targeted with network injection attacks using NSO Group ‘s spyware. In October 2019, security experts at Amnesty International’s Security Lab have uncovered targeted attacks against Moroccan human rights defenders
Security researchers are warning players of a popular MMO game that over 1.3 million user records are being sold on dark web forums. Usernames, passwords, email addresses, phone numbers and IP addresses belonging to players of Stalker Online were found
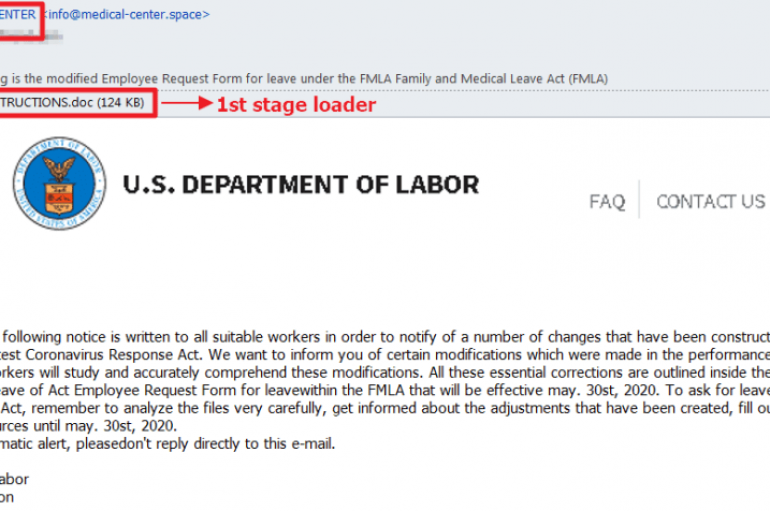
Experts spotted a new version of the IcedID banking trojan that uses steganography to infect victims as part of COVID-19 themed attacks. A new version of the IcedID banking trojan was employed in COVID-19 themed attacks, the new variant uses
Burp Suite 2020.5.1 Released – Security Bugs Fixed & Improvements to the HTTP Message Editor
Burp Suite is one of the most famous tools used by pentesters & bug hunters, which incorporates a full static code investigation engine to discover vulnerabilities. It is a widely used tool to identify vulnerabilities with web applications. Penetration testers
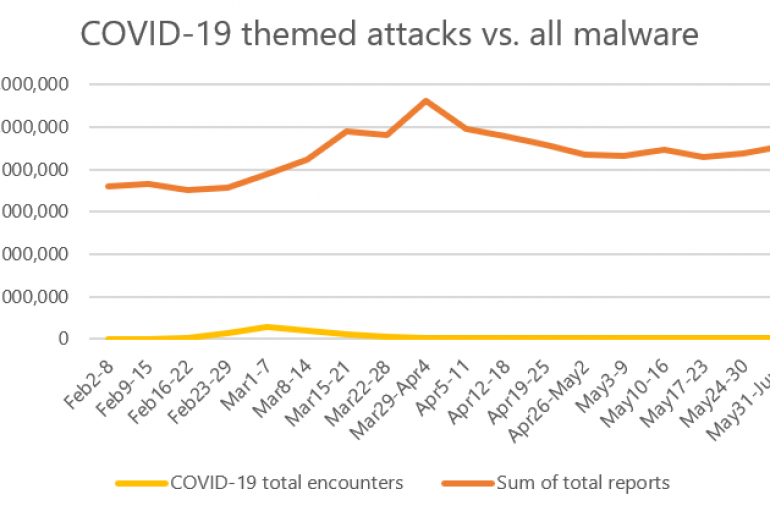
Threat actors adapted their tactics to exploit the interest in the ongoing COVID-19 pandemic, Microsoft says. Since the beginning of the COVID-19 pandemic, threat actors started to actively deploy opportunistic campaigns using Coronavirus lures. Anyway, Microsoft says that malware attacks
Massive Spying Campaign Targets Chrome Browser, Over 32 Million Users Potentially Impacted
A newly discovered massive spyware campaign uses Chrome browser extensions aimed to steal sensitive data from users across multiple geographies and industry segments. Researchers from Awake Security researchers uncovered more than 111 malicious Chrome extensions that use GalComm domains for
Security researchers discovered a new Mac malware Shlayer spreading through Google poisoned search results. The malware distributed masqueraded as a fake Adobe Flash Player installer (.DMG disk image). The malware installer and its payload had a 0/60 detection rate among
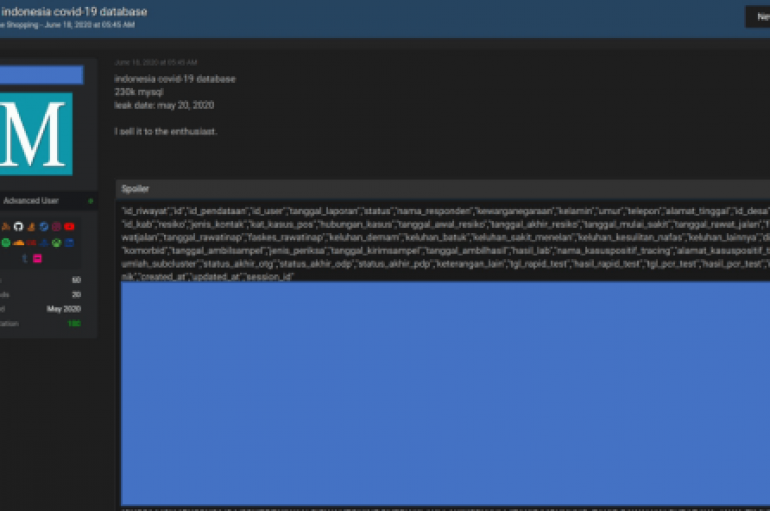
Security researchers at threat intelligence firm Cyble discovered over 230.000 Indonesian COVID-19 patients records leaked in the darknet. As part of a regular Deepweb and Darkweb monitoring activity, researchers at threat intelligence firm Cyble identified a credible threat actor who
A vulnerability with Cisco Webex Meetings Desktop App for Windows allows an authenticated local attacker to gain access for sensitive information on a vulnerable system. The vulnerability can be tracked as CVE-2020-3347 and it is due to unsafe usage of
New AcidBox Malware employed in targeted attacks leverages an exploit previously associated with the Russian-linked Turla APT group. Palo Alto Networks researchers analyzed a new malware, dubbed AcidBox, that was employed in targeted attacks and that leverages an exploit previously associated
A flaw in Cisco Webex Meetings client for Windows could allow local authenticated attackers to gain access to sensitive information. A vulnerability in Cisco Webex Meetings client for Windows, tracked as CVE-2020-3347, could be exploited by local authenticated attackers to
A state-based actor is launching cyber attacks against government, public services and businesses, Australia ‘s prime minister said. Australia ‘s prime minister Scott Morrison said that a “state-based actor” is targeting government, public services, and businesses. Warning Australians of “specific
Google has removed scores of malicious and fake Chrome extensions being used in a global eavesdropping campaign. The threat was spotted by Awake Security, which detected 111 of the malicious extensions over the past three months. When it notified Google
Australian Prime Minister Scott Morrison today warned of a major state-sponsored cyber-espionage campaign targeting government and private sector businesses. He urged domestic organizations to take steps to improve their resilience, including the use of multi-factor authentication to access cloud and
Unpatched zero-day Flaw in 79 Netgear Routers Allows Hacker to take Full Control of the Device
Researchers discovered unpatched zero-day vulnerability with 79 Netgear routers that allow attackers to take control over the device remotely. The flaw allows attackers to run arbitrary code as “root” user and to take full control over the device remotely. The