Archive
Critical Flaw in Cisco IOS Routers Let Remote Hackers Take Complete Control of the Systems
Recently, Cisco has announced that it has fixed many vulnerabilities in Cisco IOS Routers, including more than a dozen vulnerabilities that are affecting the company’s industrial routers and switches. In total, 25 vulnerabilities of high and critical severity levels were
Meerut police uncovered a security breach, where over 13,500 phones manufactured by Vivo found running with the same IMEI number. IMEI number known as International Mobile Equipment Identity, a 15-digit number used to identify the device. The IMEI number is
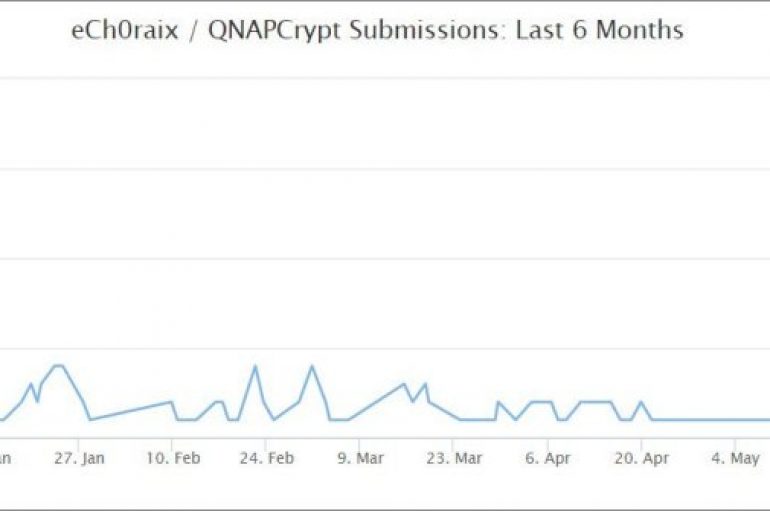
eCh0raix Ransomware operators are back after months of apparent inactivity, now are targeting QNAP storage devices in a new campaign. Threat actors behind the eCh0raix Ransomware have launched a new campaign aimed at infecting QNAP storage devices. The eCh0raix ransomware
Security experts have warned that hackers are using a new multi-platform Java ransomware “Tycoon” to target Windows and Linux users to lock down the files. We all know that hackers are constantly looking for new means to attack data centers
ST Engineering is the last victim of the Maze Ransomware operators that published their data on their leak website. ST Engineering is one of the leading engineering groups worldwide, it specializes in the aerospace, electronics, land systems, and marine sectors. The group operates in
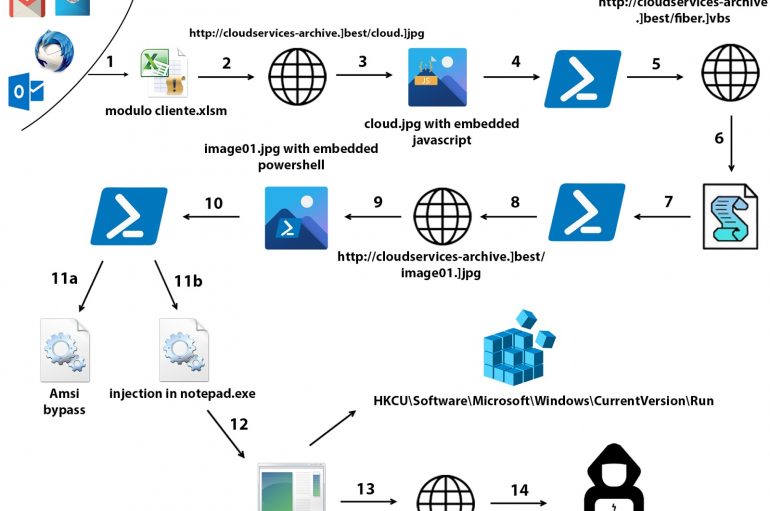
ZLab malware researchers analyzed the attack chain used to infect Italian speaking victims with the Netwire malware. Introduction Info stealer malware confirms to be one of the most adopted weapons of cyber actors. One of them is Netwire (MITRE S0198),
Maine residents hoping to pursue a career in cybersecurity will finally be able to study the subject at community college. Starting in fall 2020, Northern Maine Community College (NMCC) will be the first community college in the state to offer
“Systematic design flaws” have been discovered in leading internet-connected doorbell and security cameras by a Florida Institute of Technology student. Blake Janes unearthed vulnerabilities in devices manufactured by Ring, Nest, SimpliSafe, and eight other companies relating to the removal of
The operators of a North Dakota contact tracing app have had a rethink when it comes to sharing users’ data with third-party services. Care19 was created by ProudCrowd LLC to track the spread of COVID-19 in the Peace Garden State.
Cybercriminals targeted the email accounts of President Donald Trump’s and Democrat Joe Biden campaign staffers, Google researchers said. Google’s TAG who deals with nation-state hacking detected that Chinese state-backed hackers targeted the Email accounts of Biden campaign staffers whereas the
Sophos has confirmed that it is implementing some internal restructuring, but denied that it plans to close its Naked Security blog. Following reports which emerged last night about Sophos’ plans to furlough staff and close the award-winning blog, a spokesperson
Experts recently discovered a multi-platform ransomware, dubbed Tycoon Ransomware, that uses a Java image file (JIMAGE) to evade detection. Experts from BlackBerry Threat Intelligence and KPMG recently discovered a new strain of multi-platform ransomware dubbed Tycoon ransomware. The Tycoon ransomware
DDoS-ers Target Black Lives Matter Groups
Widespread violent protests across the US over the past week have been followed by attempted DDoS attacks on several rights groups, according to Cloudflare. The web security firm analyzed malicious HTTP requests it blocked across the weekend of April 25/26
Chinese and Iranian state-sponsored hackers have been caught targeting the Trump and Biden Presidential campaigns, according to Google. Shane Huntley, director of Google’s Threat Analysis Group, revealed the news in a couple of tweets yesterday. He confirmed that there was
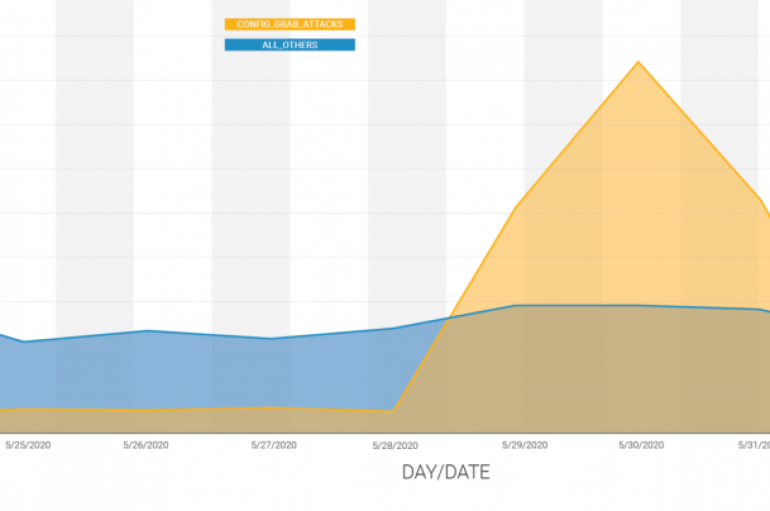
Security experts have observed a large-scale campaign over the weekend aimed at stealing configuration files from WordPress sites. Security researchers from WordFence have observed a large-scale campaign over the weekend aimed at stealing configuration files from WordPress sites. Threat actors
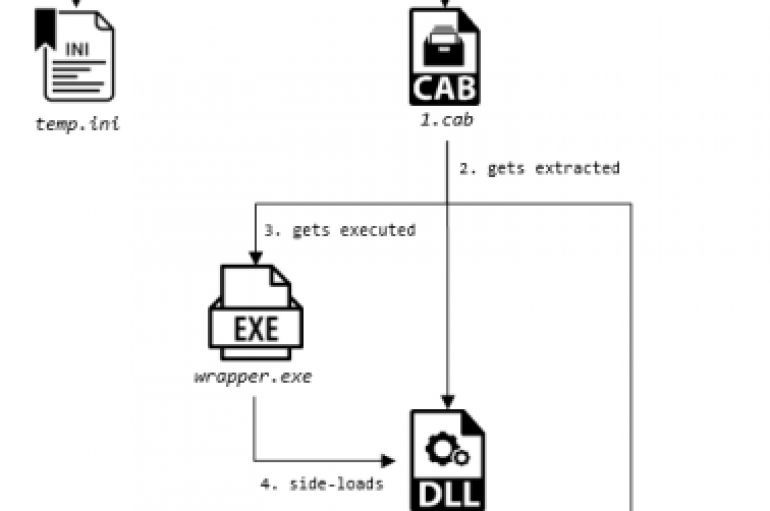
A Chinese threat actor tracked as Cycldek (aka Goblin Panda, or Conimes) has developed new tool to steal information from air-gapped systems. Security experts from Kaspersky Lab reported that the Chinese threat actor tracked as Cycldek (aka Goblin Panda, or