Archive
Facebook has announced plans to ban deepfake videos. In a blog post, Monika Bickert, the company’s vice-president for global policy management, acknowledged that “while these videos are still rare on the internet, they present a significant challenge for our industry
Imperva Appoints Pam Murphy as New CEO
Cybersecurity company Imperva today announced the appointment of Pam Murphy as CEO, effective immediately. Murphy will take over from interim CEO Charles Goodman, who will continue to serve as chairman of the board. Murphy brings a wealth of experience to
Security experts have found a malicious app in the Google Play that exploits the recently patched CVE-2019-2215 zero-day vulnerability. Earlier October, Google Project Zero researchers Maddie Stone publicly disclosed a zero-day vulnerability, tracked as CVE-2019-2215, in Android. Maddie Stone published technical
TOR is an important, popular, and controversial tool. It is important because Tor network offers the most effective way to surf the web anonymously, and it’s pretty popular – over 2 million people use it daily. At the same time,
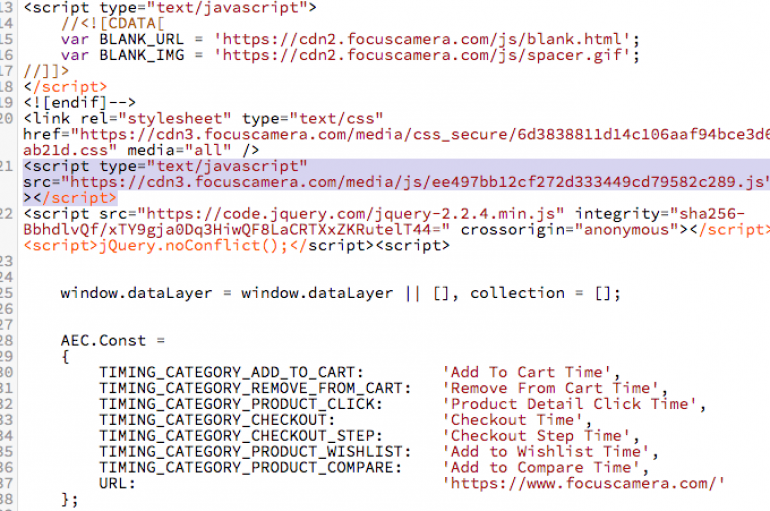
A new MageCart attack made the headlines, this time the gang compromised the website of popular Focus Camera. The Magecart group has compromised the website of the photography and imaging retailer Focus Camera. The hack took place last year, the
Google has recently disabled all Xiaomi smart home integrations on Nest Hub after being informed that some users could access other people’s camera feeds. On January 1st, 2020, a Reddit user (‘/u/Dio-V’) posted a discussion revealing that Nest Hub was
US Biz Closes Doors After Ransomware Attack
A US fundraising firm has been forced to close its doors after more than 60 years in business following a crippling ransomware attack in October. The Heritage Company, based in Sherwood, Arkansas, let its 300 employees go just before Christmas,
Hackers using New Evasion Techniques in Web Skimmers To Bypass the Detection & Steal Credit Card Data
Researchers discovered a new evasion technique used by attackers in client-side web skimmer to bypass their conceal their fraudulent activity. Recently, a security researcher revealed a steganography-based credit card skimmer in which they found that the attackers uploads or modifies
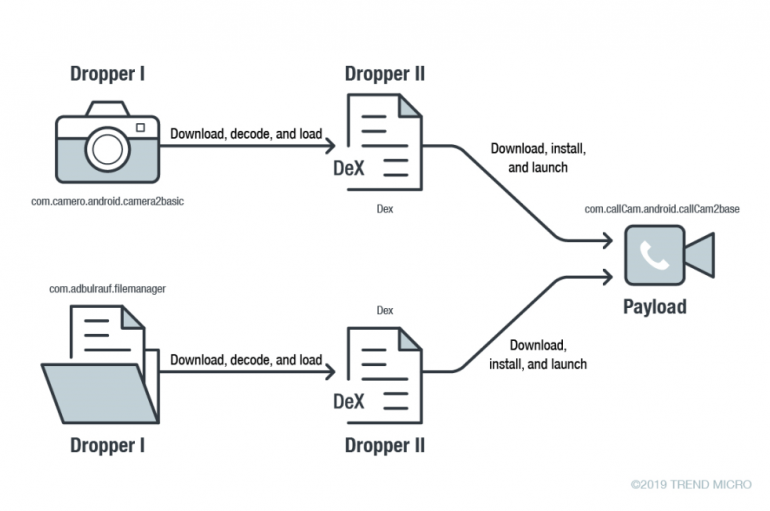
Hackers Exploit Android Vulnerability to Install Malware Without User Interaction Via Google Play
Security researchers from Trend Micro observed three malicious apps on Google play that aims to compromise victim’s devices and to steal information. The three apps include “Camero, FileCryptManager & CallCam,” among the three Camero is the one exploits use-after-free vulnerability
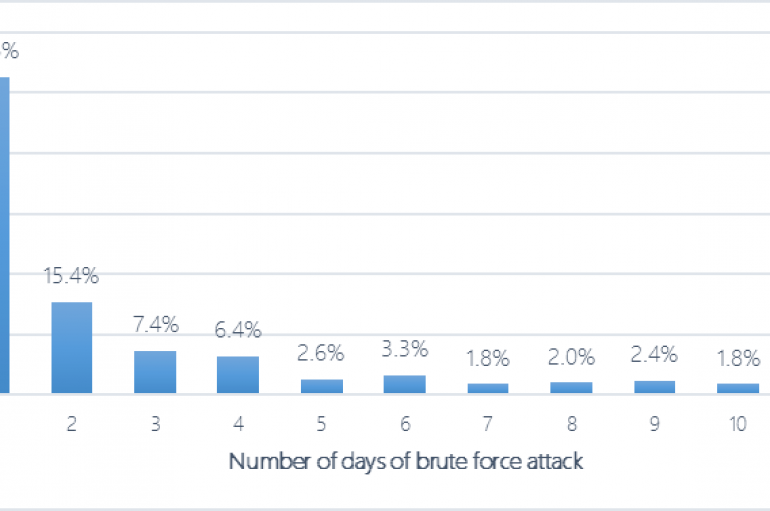
Microsoft published an interesting analysis of RDP brute-force attacks that targeted the 45,000 have analyzed in months of study. Researchers from Microsoft have analyzed several months’ worth of data to investigate RDP brute force attacks occurring across Microsoft Defender ATP
Austria’s Foreign Ministry Hit by Cyber-Attack
The Austrian government has been hit by a cyber-attack that could be the work of a rival foreign power. The attack, which was leveled against the country’s Foreign Ministry, began late on Saturday night. A spokesperson for the ministry described
US Braced for Cyber Retaliation from Iran
The US government has echoed concerns from the cybersecurity industry that Iranian state hackers could respond to the assassination of a top Tehran general with attacks on US critical infrastructure (CNI). Widely considered the second most powerful man in Iran,
Japanese Love Hotel Site Breached
A booking site for customers of Japanese “love hotels” has been hacked, raising fears over follow-on identity fraud and blackmail attempts. In a country known for its focus on convenience, love hotels are a popular feature in towns and cities,
The websites of a major global currency exchange business are still down after a “software virus” struck the firm on New Year’s Eve last week. London-headquartered Travelex, which describes itself as “the world’s leading foreign exchange specialist,” operates online around
DeathRansom – A new ransomware strain that evolves from no encryption to using a combination of encryption algorithms to encrypt files. The ransomware strain observed first in earlier November, it pretends to encrypt files, but it only appends the extension,
Normally, every website you visit is recorded in your browser’s history. Your browser will remember the URLs of websites you regularly visit, files you’ve downloaded, data “cookies” that track your activity on certain sites, what you’ve typed into search engines,