Archive
App Defense Alliance: Google tied up with mobile security companies to find bad apps before it reaches the user device. The primary goal of the alliance is to make Google play more secure. They are more than 2.5 billion Android
Bug hunters have earned a total of $195,000 for finding flaws in TVs, routers and smartphones on the first day of the Pwn2Own Tokyo 2019 contest. Pwn2Own is the annual hacking contest event organized by Trend Micro’s Zero Day Initiative
Facebook Reveals An Another Data Leak – 100+ 3rd Party Apps Accessed FB Groups Member Data
Facebook revealed a new security incident that affected the FB groups member by nearly 100+ 3rd party apps that accessed the group member’s information. These apps were misused the Facebook Groups API and retained access to group member information, such
The excuses made by companies that have suffered a data breach are being parodied online by a new website, whose creator is unknown. “Why the f*ck was I breached?” uses algorithms to generate a slew of entertaining excuses that attempt
California DMV Exposes Drivers’ Data for 4 Years
The Social Security information of thousands of drivers has been exposed following a data breach at the California Department of Motor Vehicles that went unnoticed for four years. Information relating to 3,200 people issued with driver’s licenses was inadvertently leaked
Facebook Admits Another Developer Privacy Snafu
Facebook has revealed yet another incident where third-party developers may have been allowed too much access to user data. In this case, names, profile pictures and other information relating to members of Facebook groups may have been accessed improperly by
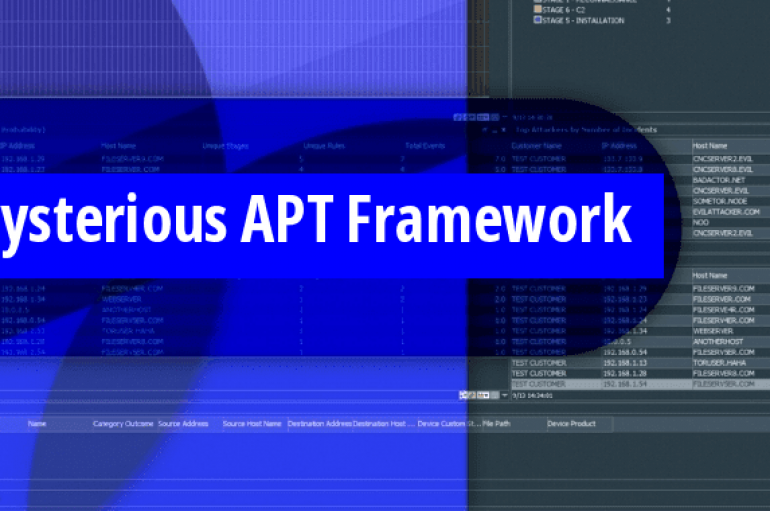
DarkUniverse – A Weaponized APT Framework Found via Interesting Script that Used in NSA Hacking Attack
Researchers found the existence of the new APT Framework named “DarkUniverse” using Tips from a script that used in the NSA breach in 2017 in which, shadow brokers published their well-known ‘Lost in Translation’ Hacking tools leak. “Lost in Translation”
The internet is awash with politically themed malware, used in everything from ransomware to remote access trojans (RATs), according to new research from Cisco Talos. The security firm’s study began with analysis of a regular-looking malicious spam campaign which used
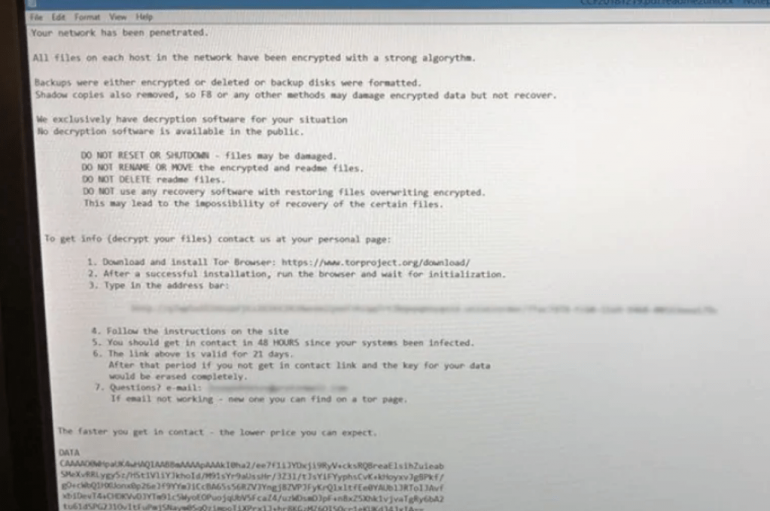
Another organization in the healthcare industry was a victim of a Ransomware attack, this time the victim is Brooklyn Hospital. A ransomware attack has infected several computer systems at the Brooklyn Hospital Center in New York, the organization permanently lost
The evolution of technology in Cybersecurity allows us to do amazing things that we only imagined doing in the past. Computers and technology have pushed the boundaries of the human mind and how society functions today. From smartphones to driverless
Drones could become a major network security threat from 2020, forcing organization to guard the airspace around their buildings, security researchers have warned. Small unmanned aerial vehicles (UAVs) will increasingly evolve from novelty items to “ubiquitous business tools” over the
Hackers compromised a network of ‘camgirl’ sites and exposed data belonging to millions of users and sex workers. Hackers compromised several ‘camgirl’ sites and have exposed millions of sex workers and users. All the sites were run by the Spanish
There is a sense of failure among security practitioners, believing that they cannot keep up with attacks, and this has created a sense of irrational fear. Speaking at the Tenable Edge conference in London, Tenable CEO Amit Yoran said that
Sumo Logic Acquires JASK
Californian security-event management company Sumo Logic has acquired JASK Labs, Inc. JASK makes security information and event management (SIEM) software and is best known for its flagship product, JASK Autonomous Security Operations Center (ASOC), which collects and analyzes data from
A ransomware attack disrupted IT operations in the territory of Nunavut (Canada), all government services requiring access to electronic data were impacted. A ransomware attack disrupted IT operations in the remote Canadian territory of Nunavut, all government services requiring access
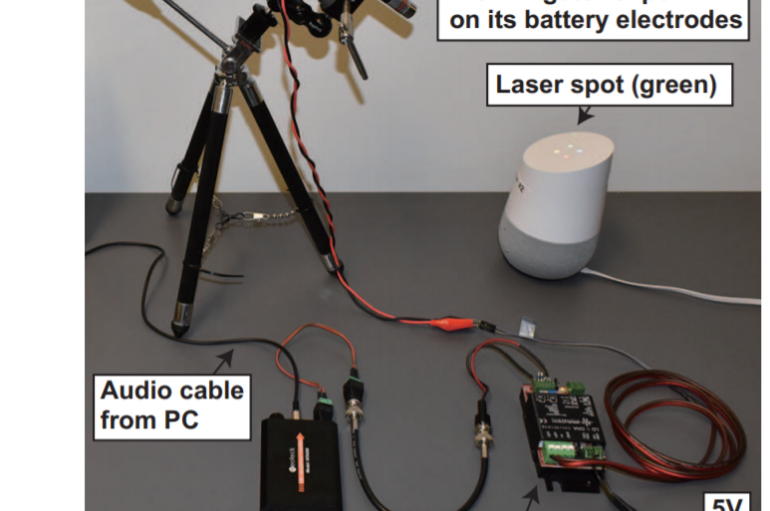
Experts demonstrated that is possible to hack smart voice assistants like Siri and Alexa using a lasers beam to send them inaudible commands. Researchers with the University of Michigan and the University of Electro-Communications (Tokyo) have devised a new technique,