Archive
Most popular video app VidMate caught up for various malicious activities in their customers Android mobiles including drain users battery, collecting personal information, Create fake ad click-through invisible ads to generate revenue from 500 million users who have installed VidMate.
Security researchers from Chronicle, Alphabet’s cyber-security division, have spotted a Linux variant of the Winnti backdoor. Security experts from Chronicle, the Alphabet’s cyber-security division, have discovered a Linux variant of the Winnti backdoor. It is the first time that researchers
A new data leak made the headlines, a database containing the contact information of millions of Instagram influencers, celebrities and brand accounts has been found online. The news was first reported by the TechCrunch website, a database was left unprotected
An identity thief can steal your sensitive information to commit fraudulent activities, such as file tax, apply for medical services or credit. Identity theft can damage your reputation, credit status, and cost your money and time. If you receive mysterious
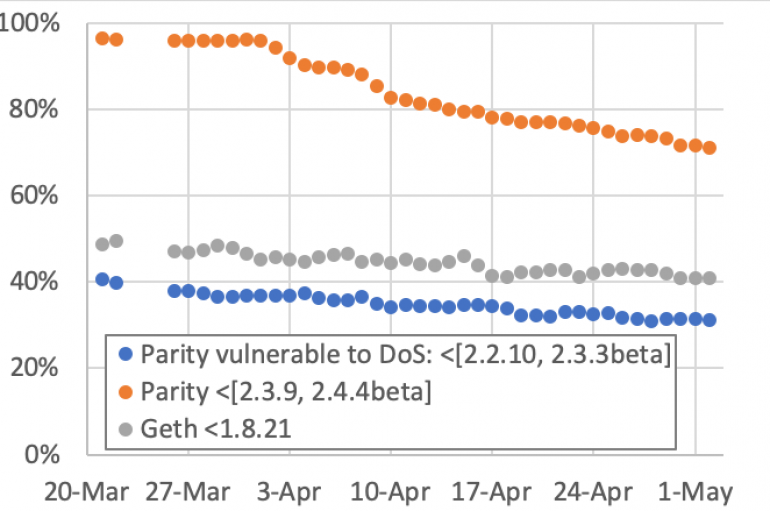
Security researchers from SRLabs have published a report that analyzed the risks for Ethereum network caused by unpatched Ethereum clients. Researchers at SRLabs published a report based on ethernodes.org data, that revealed that a large number of nodes using the
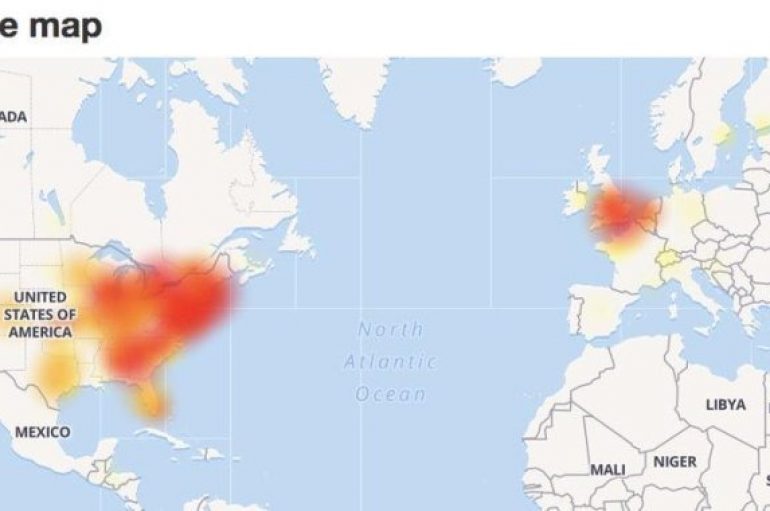
Salesforce is facing a huge outage, it shut down a good portion of its infrastructure due to change to the production environment. A change in the production environment is the root cause of the broad outage suffered by Salesforce. The
Google Using Gmail to Read Your Online Purchase Invoice Data to Track Your Purchase History
Google tracks every single purchase that you have made online in years if you have the receipts sent to your personal Gmail account. The purchase records can be accessed through a page called Purchases, which shows a list of products
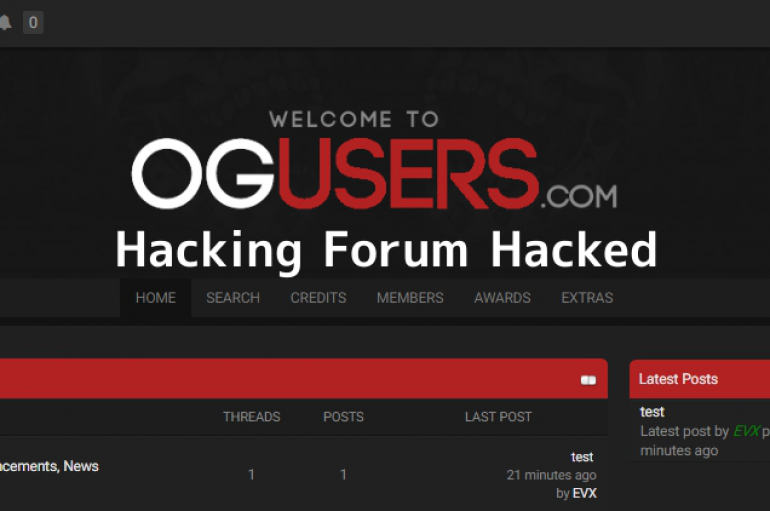
OGusers Hacked – A Hacking Forum Where Hackers Involved in Hijacking Online Accounts Itself Hacked
OGusers, a popular forum where cyber criminals involved in various hacking activities, including hijacking online accounts, conducting SIM swapping attacks, trade stolen Instagram, and Twitter accounts hacked by other hackers. The breach exposed nearly 113,000 forum users sensitive information including
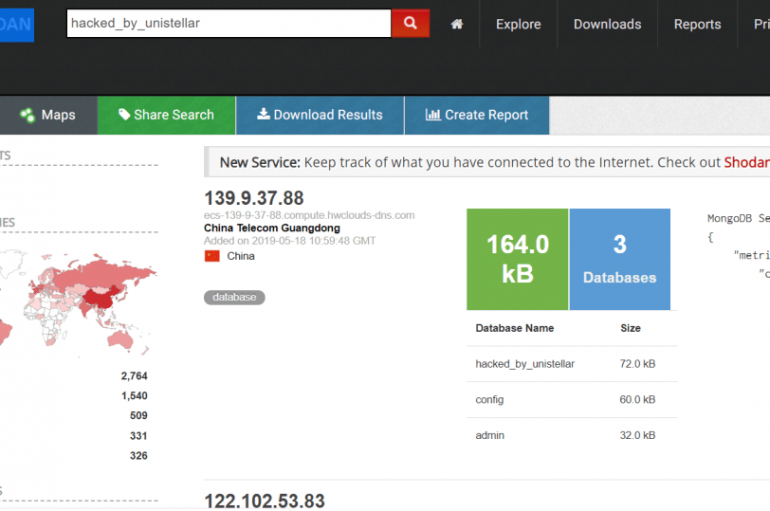
Unistellar attackers have already wiped roughly 12,000 unsecured MongoDB databases exposed online over the past three. Every time hackers deleted a MongoDB database they left a message asking the administrators to contact them to restore the data. Unfortunately, the criminal practice
Hackers come in many forms with sophisticated Hacking Techniques, While there has been a lot of discussion about online security in recent years, many people are still unfamiliar with the types of attacks they are most likely to be targeted
An Unauthenticated Persistent Cross-Site Scripting vulnerability in WP Live Chat Support WordPress plugin allows hackers to inject malicious JavaScript payloads in the vulnerable website. More than 60,000+ users used the plugin, it allows web admins to chat with visitors for
Researchers discovered a new malware that infect MacOS via malicious website by disguised as WhatsApp official website where it also drops a malware for Windows Operating system. Attackers are targeting both Windows and MacOS operating system to injecting a backdoor
The German newspaper Der Spiegel revealed that the software company behind TeamViewer was compromised in 2016 by Chinese hackers. China-linked hackers breached German software company behind TeamViewer in 2016, this news was reported by the German newspaper Der Spiegel According
Cisco had issued security updates to address 57 security flaw, including three flaws in networks management tool Prime Infrastructure. One of the flaws addressed by Cisco in the Prime Infrastructure management tool could be exploited by an unauthenticated attacker to
Slack users have been urged to upgrade their applications and clients to the most recent version, 3.4.0, after Tenable researcher David Wells discovered a new vulnerability that would allow an attacker to share malicious hyperlinks that could alter where a
Top 5 Best Hacking Simulator for Every Aspiring Hackers to Practice Their Hacking Skills
Hacking Simulator is known for simulating the hacking operation and play with a lot of hacking tricks. Hacking is a skill that needs to be brushed on to stay on track with the latest security and network penetration methodologies. To