Archive
Canadian Telco Exposes Unencrypted Card Details
Canadian telco giant Freedom Mobile has become the latest big-name brand whose security has been found wanting after researchers discovered an unprotected database exposing over five million customer records. A research team at vpnMentor claimed to have discovered the Elasticsearch
State-sponsored attacks, cloud storage misconfiguration, ransomware and social threats targeting the C-suite all posed major risks to global organizations over the past 12 months, according to Verizon. The vendor’s newly released Data Breach Investigations Report 2019 comprises analysis of over
Cisco released a new security update with the fixes for a critical vulnerability that resides in the Cisco Elastic Services Controller REST API let attackers full control of the system remotely. Cisco Elastic Services Controller is a virtual network functions
After its acquisition of SecureData earlier this year, Orange has announced another agreement it has signed to acquire SecureLink, a transaction that will advance Orange’s position in the EU’s cybersecurity industry, according to a May 7 press release. The deal
Binance hacked, hackers, stolen 7,000 Bitcoin that worth more than $40 Million using a variety of attack methods that include phishing, viruses, and other attacks. By using the hacking methods, they obtain a large number of user API keys, 2FA
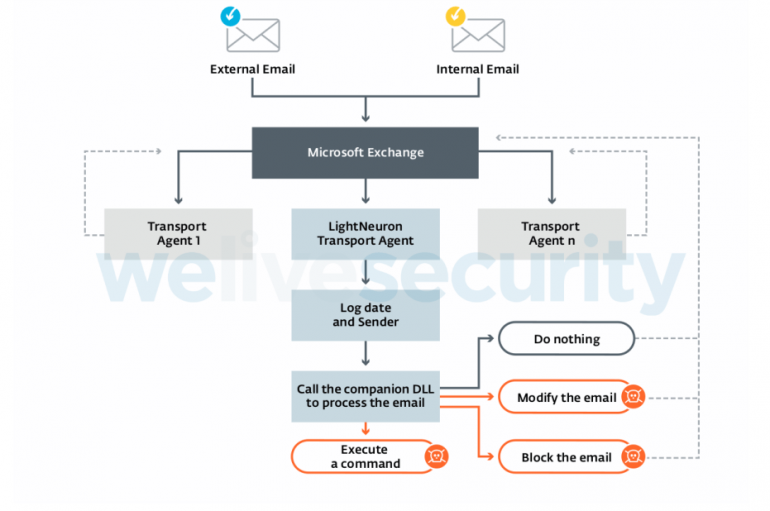
Russia-linked APT group Turla has been using a sophisticated backdoor, dubbed LightNeuron, to hijack Microsoft Exchange mail servers. Russia-linked APT group Turla has been using a sophisticated backdoor, dubbed LightNeuron, to hijack Microsoft Exchange mail servers. Turla group (also known
Artificial Intelligence in Cyber Security is always evolving, say from the old school days when AV was thought to be an effective defender to the present days where AV, SIEM, IPS, endpoint security and protection play a crucial part in
Major Uptick in IoT-Related Breaches and Attacks
Researchers have identified a significant uptick in breaches and attacks related to the internet of things (IoT), according to a new Ponemon Institute report, The Third Annual Study on Third Party IoT Risk: Companies Don’t Know What They Don’t Know.
In a move expected to augment its cloud-based architecture and people-centric security platform, Proofpoint announced that it has entered into a definitive agreement to acquire zero trust network access innovator, Meta Networks. Subject to customary closing conditions, the deal is
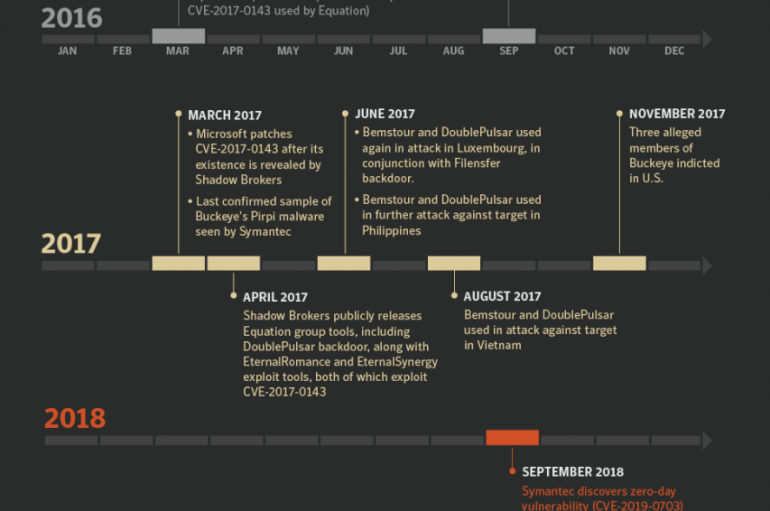
China-linked APT group tracked as APT3 was using a tool attributed to the NSA-linked Equation Group more than one year prior to Shadow Brokers leak. China-linked APT group tracked as APT3 (aka Buckeye, APT3, UPS Team, Gothic Panda, and TG-0110)
New Magecart Group Targets 201 Campus E-Stores
A cybercrime group has been spotted using infamous digital skimming code techniques to infect 201 online campus stores in the US and Canada in a supply chain attack. The gang targeted PrismWeb, an e-commerce platform owned by PrismRBS which is
Matrix-Themed Ransomware Spikes in May
Security experts are warning organizations of a new, highly targeted ransomware strain known as MegaCortex, which appears to have been written by a fan of ’90s cult film The Matrix. Although the ransomware first appeared at the start of the
New MegaCortex Ransomware Attack on a Large Number of Enterprise Networks using Red-Team Attack Tools
A new ransomware strain MegaCortex leverages both automated and manual components to infect a large number of victims around the world including Italy, the United States, Canada, the Netherlands, Ireland, and France. Security researchers from Sophos detected a sudden spike
A Bug in Mirai Code Allows Crashing C2 Servers
Ankit Anubhav, a principal researcher at NewSky Security, explained how to exploit a vulnerability in the Mirai bot to crash it. Ankit Anubhav, a principal researcher at NewSky, explained how to exploit a trivial bug in the code of the
ICS-CERT is warning of several vulnerabilities in the GE Communicator software, including hardcoded credentials and privilege escalation bugs. ICS-CERT is warning of five flaws affecting the GE Communicator software, including privilege escalation issues and hardcoded credentials GE Communicator is a
Hacker Compromised Several IoT Botnet C2 Servers and Taken Control of It Due to Weak Credentials
A Hacker who goes by name Subby has compromised more than 29 IoT botnet command and control servers that were using weak login credentials. He launched a brute force attack on these C2 servers and gain access to a number