Archive
New Grab-and-Go Stealer Is Making Waves
Researchers suspect that a new stealer malware dubbed Baldr, first detected in January, has incorporated three known threat actors, according to Malwarebytes. In today’s blog post, researchers said that Baldr has earned positive reviews on Russian hacking forums for its
WPScan – Penetration Testing Tool to Find The Security Vulnerabilities in Your WordPress Websites
WPScan is a WordPress security scan for detecting and reporting WordPress vulnerabilities. WordPress is a free online Open source content Managed system focused on PHP and MySQL. It is one of the powerful and most used blogging tools. As there
A Japanese manufacturer has seen output plummet for several days after being hit by the first stage in an attempted crypto-mining cyber-attack, according to reports. Optical equipment maker Hoya, which operates in over 30 countries worldwide, is said to have
Cyber-criminals have been trading stolen identities in Genesis, an underground marketplace, and then using them to bypass anti-fraud protections, according to Kaspersky Lab. At the 2019 Security Analyst Summit (SAS), researchers announced the findings of their Genesis investigation. According to
Verizon Fios Router Vulnerabilities Allows Attackers to Gain Complete Control Over the Network
Security researchers at Tenable uncovered multiple flaws with Verizon Fios Quantum Gateway router that allows a remote attacker to gain complete access over the network. By exploiting the vulnerability an attacker could sniff into victims network traffic and van exfiltrate
Adobe Released Security Updates & Fixed 43 Vulnerabilities in Acrobat Reader, Adobe Flash & More
Adobe security updates released for April with the fixes of 43 vulnerabilities that affected different Adobe products. There are 8 different Adobe products are affected including Adobe Flash Player, Shockwave Player, Dreamweaver, Adobe XD CC, Adobe Experience Manager Forms, and
FileTSAR, a free open source tool that combines various open source forensic investigation tools used by law enforcement agencies. The all-in-one cybersecurity toolkit was developed by Purdue Polytechnic researchers to help detectives in the reconstruction of digital evidence from multiple
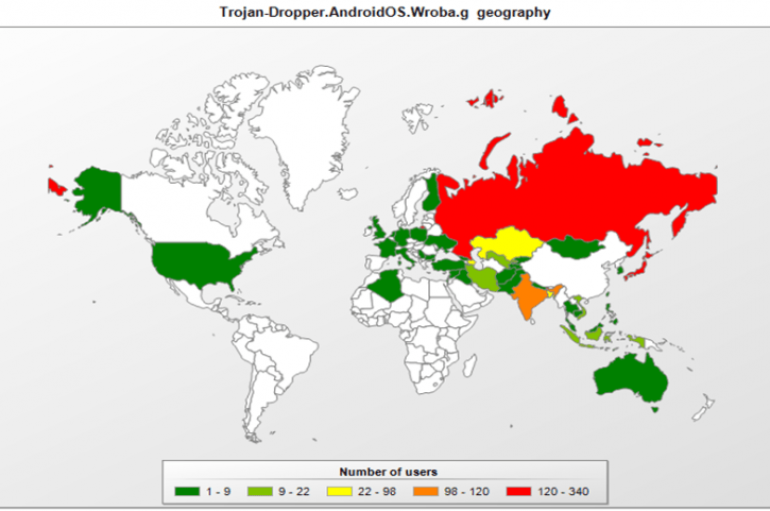
Kaspersky Lab reported that hundreds of users have been targeted with malware over the past month as part of a recent Roaming Mantis campaign. Security experts at Kaspersky Lab reported that hundreds of users have been targeted with malware over
Some 90% of critical infrastructure (CNI) providers claim that their IT/OT environment has been damaged by a cyber-attack over the past two years, according to a new Ponemon Institute report. Sponsored by security vendor Tenable, the Cybersecurity in Operational Technology:
A test carried out by ethical hackers against the cyber defenses of 50 universities found that they can cripple the defense and exfiltrate sensitive data within two hours. The penetration testing conducted ethical hackers” working for Jisc, who provides internet
New DNS Hijacking Attack Exploiting DLink Routers to Target Netflix, PayPal, Uber, Gmail Users
Cybercriminals continuously perform DNS hijacking attack to the consumer’s routers over the past 3 months, and the sites targeted for phishing includes Netflix, PayPal, Uber, Gmail. DNS hijacking is a type of malicious attack that used to redirect the users
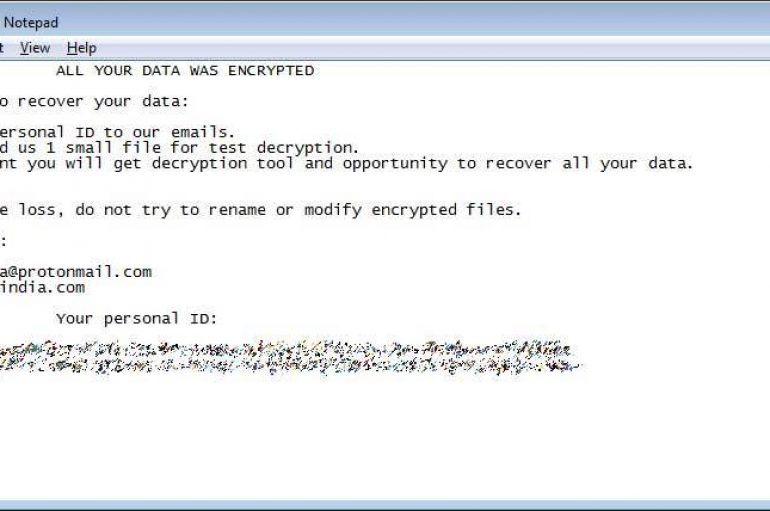
Researchers at Emsisoft developed a decryptor for the Planetary Ransomware family that could allow victims to decrypt their files for free. Good news for the victims of the Planetary Ransomware, security firm Emsisoft has released a decryptor that allows victims
As a normal Internet user, you have the sensible hope that your correspondences and transaction are private and secure in Internet security Environment. Numerous activities in our everyday lives now depend on the Internet, including different types of communication, shopping,
With the use of deep learning, researchers Yisroel Mirsky, Tom Mahler, Ilan Shelef and Yuval Elovici at Cyber Security Labs at Ben-Gurion University demonstrated in a video proof of concept (PoC) that an attacker could fool three expert radiologists by
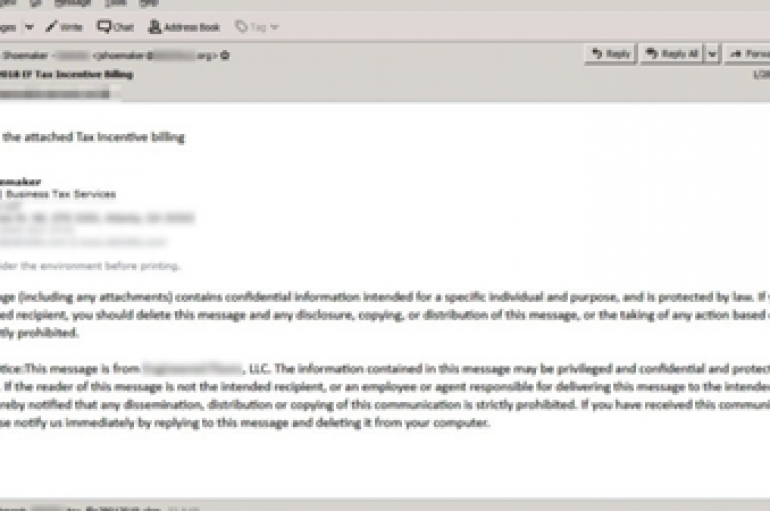
TrickBot Used in Tax Season Email Spoofing
As April 15, the US tax-filing deadline, swiftly approaches, cyber-criminals are taking advantage of the season, using campaigns to deceive three of the biggest accounting, tax services and payroll companies in the US, according to researchers at IBM X-Force. In
A Serious vulnerability that discovered in MikroTik RouterOS allows attackers to perform DoS attack on the vulnerable router that causes the device to reboot. MikroTik provides hardware and software for Internet connectivity around the world and they also created a