Archive
Third-Party Breaches Plague Multiple Industries
From January 25 to 28, 2019, multiple organizations, including Discover Financial Services, Verity Medical Foundation, Verity Health Systems and Allen Chern LLP, have made routine filings in accordance with California state law, reporting cybersecurity incidents that may or may not
Digital transformation is exposing organizations to greater IT complexity and cyber-risk, according to new global research from Thales eSecurity. The security vendor polled 1200 execs with responsibility for IT and data security in nine countries around the world to compile
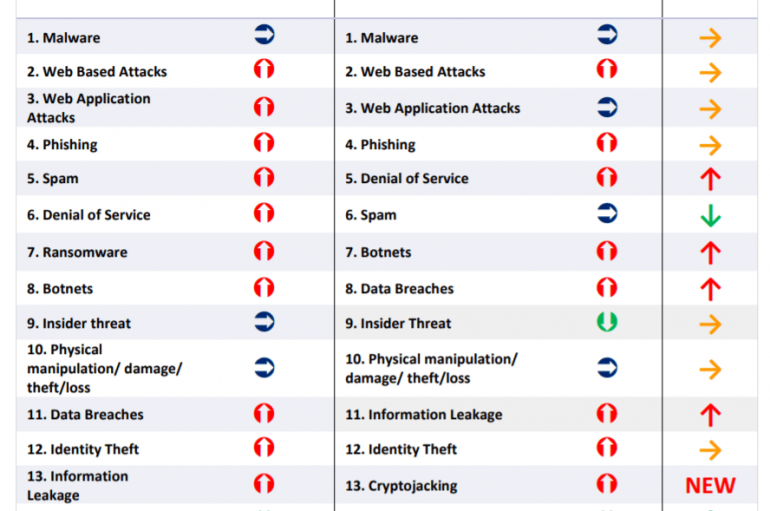
Reading The ENISA Threat Landscape Report 2018
According to the ENISA Threat Landscape Report 2018, 2018 has brought significant changes in the techniques, tactics, and procedures associated with cybercrime organizations and nation-state actors. I’m proud to present you the ENISA Threat Landscape Report 2018, the annual report
65 Fortune 100s Downloaded Flawed Apache Struts
Despite Apache Struts releasing multiple updates to its software in the nearly two years since the Equifax breach, Sonatype published research which found that between July and December 2018, two-thirds of the Fortune 100 companies downloaded the same vulnerable version
A joint operation conducted by law enforcement agencies in the United States and Europe allowed seizing the xDedic marketplace. Law enforcement agencies in the US and Europe announced the seizure of the popular xDedic marketplace, an underground market offering for
Attackers Exploit Zero-Day in WordPress Plugin
After being abandoned by its creator, WordPress plugin Total Donations is reportedly being compromised by attackers who are leveraging a zero-day exploit, according to Wordfence. Researchers confirmed that malicious actors are able to gain administrative access to affected WordPress sites
Europol has detailed how law enforcers across the globe are tracking down customers of notorious DDoS-as-a-service site webstresser.org. The site was taken down in April 2018 as part of Operation Power OFF, but that gave police a trove of information
Group FaceTime Disabled While Apple Works on Fix
A flaw in Apple’s FaceTime app allows users to spy on each other, which has resulted in a Twitter-storm of tweets encouraging iPhone users to disable FaceTime while Apple works on a fix. Infosecurity contacted Apple, but the company has
Info-Stealing FormBook Returns in New Campaign
A file-hosting service registered within the last week is being used to spread information-stealing malware in another FormBook campaign, currently attacking retail and hospitality businesses both within and outside of the US, according to Deep Instinct. Though FormBook has been
Fileless Infection Steals Creds with Bank Trojan
A new variant of the password-stealing Ursnif bank Trojan has been found in the wild delivering fileless infections while remaining undetected, according to Cisco Talos Intelligence. In a blog post, researchers wrote that the banking Trojan employs “fileless persistence which
Experts from Alias Robotics released a free, open-source tool dubbed Aztarna that could be used to find vulnerable robots. A group of experts working a startup focused on robot cybersecurity has released a free, open-source framework dubbed Aztarna that could
Security experts at Wordfence security firms discovered WordPress Sites compromised via Zero-Day vulnerabilities in Total Donations Plugin The Total Donations WordPress plugin was abandoned by its developers for this reason security experts are recommending to delete it after they discovered
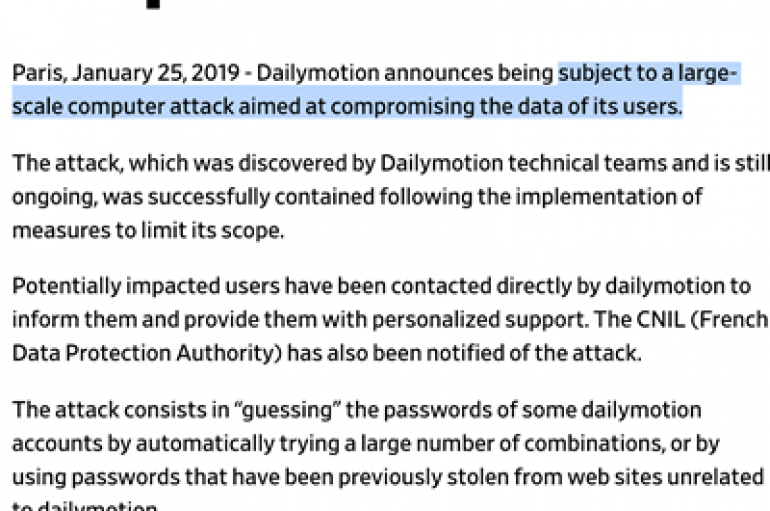
Complying with General Data Privacy Regulations (GDPR), video-sharing platform Dailymotion disclosed to France’s Commission Nationale de l’Informatique et des Libertes (CNIL) on Friday that it suffered a credential-stuffing attack. “The attack consists in ‘guessing’ the passwords of some dailymotion accounts
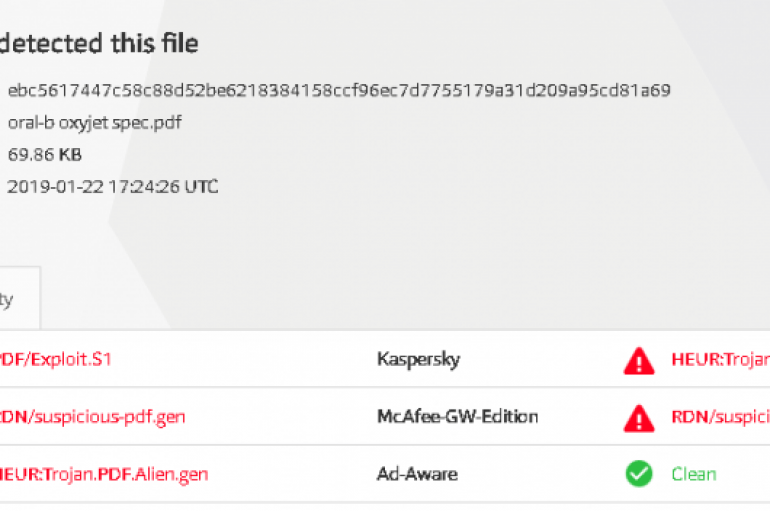
Using Steganography To Obfuscate PDF Exploits
Experts discovered PDF exploit that was using steganography to hide malicious JavaScript code in images embedded in PDF files. The exploit analysis firm EdgeSpot recently discovered PDF exploit that was usingsteganography to hide malicious JavaScript code in images embedded in
Modular Anatova Ransomware Resists Analysis
Security researchers are warning of a newly discovered and highly sophisticated strain of modular ransomware featuring special capabilities to resist analysis. Dubbed “Anatova” by McAfee, the malware has been detected across the globe, in the US, UK, Russia, Italy, Sweden
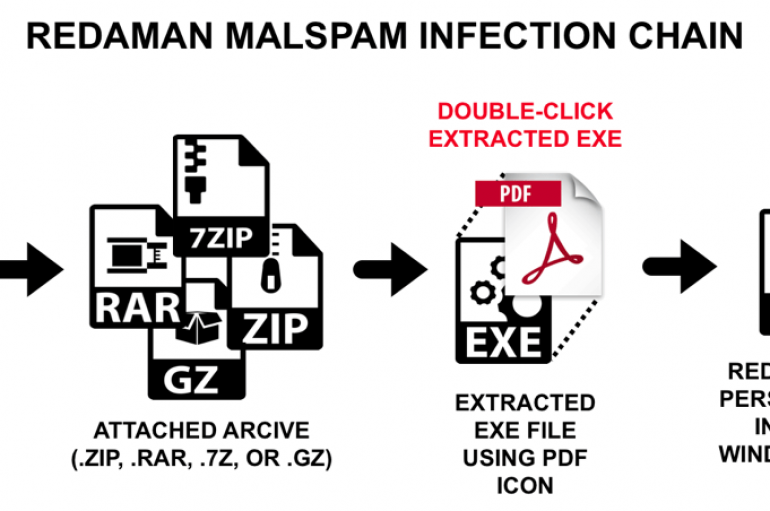
A still ongoing spam campaign that has been active during the last months has been distributing the Redaman banking malware. Experts at Palo Alto Networks continue to monitor an ongoing spam campaign that has been distributing the Redaman banking malware.