Archive
IBM is training Watson to hunt hackers
Watson, IBM’s computer brain, has a lot of talents. It mastered “Jeopardy!,” it cooks, and even tries to cure cancer. But now, it’s training for a new challenge: Hunting hackers. On Tuesday, IBM Security announced a new cloud-based version of the cognitive technology, dubbed
WhatsApp and Telegram, both the messaging services that claim to offer end-to-end encryption for chats, can witness hackers logging into user chats and even replying on their behalf, according to a new research. The vulnerability mainly stems from the Signaling
Apple provides plenty of protection for iPhone users, as the FBI learned over the last few months. But it can never offer total security. That’s why pro iOS hackers like Stefan Esser are around to poke holes in Apple’s operating
With the Panama Paper being released to the public and a recent hacker hitting major email accounts across the world, cyber attacks are on everyone’s mind. And while you might think this surge in hacker activity would keep corporations abreast
Flaws in the mobile signalling protocols can be abused to read messaging apps such as WhatsApp and Telegram. Security researchers at Positive Technologies found they can intercept messages and respond as if they were the intended recipient in services such
North Korea’s conventional military of aging Soviet jets and tanks can’t compete against the high-tech military of the US, but its capabilities in cyber warfare keep on getting better, according to a top US Army general. “This is an area
Kiddicare customer data stolen by hackers
ustomer data from baby superstore Kiddicare has been accessed by hackers, the retail chain said. A small number of customers received a “possible phishing communication” in the form of a text message from a website claiming to be a subsidiary of Kiddicare.com. It
Attackers have wasted no time targeting a critical vulnerability that could allow them to take complete control over websites running a widely used image-processing application, security researchers said. Attack code exploiting critical ImageMagick vulnerability expected within hours. As Ars reported last
It’s clear from the last six months that the cyber threat landscape has gotten worse quickly. Hospitals are under siege from ransomware, breaches are increasingly moving to mobile devices and we’ve seen a successful attack against a public utility. The
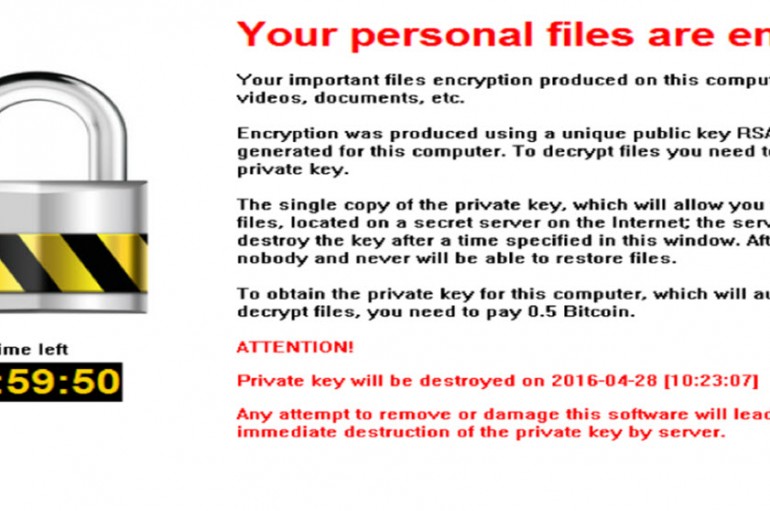
A cyber-crime group is at the heart of many non-standard ransomware infections, which appear to be carried out via a re-tooled version of the Bucbi ransomware that hasn’t been seen in usage at such a massive scale since 2014, the
This town in Romania is a hackers paradise
How would you react if your town or city is known as the global centre of cybercrime? Well, there is a town in Romania full of hackers and scammers that it has become famous as the global centre of cybercrime Râmnicu Vâlcea
The Anonymous campaign OpIcarus launched against the banking sector seems to be ramping up, with eight more financial institutions suffering DDoS attacks during the past few days, ever since the campaign was publicly announced. The first DDoS attacks part of
Those who are into hacking may be familiar with the venerable Phrack e-zine. Phrack is an ezine written by and for hackers first published November 17, 1985. Described by Fyodor as “the best, and by far the longest running hacker zine,”
95% of the time, if you provide a bad service or a bad customer experience, your client/customer will share that with others, says a report by American Express. The study also highlights that only 29% of the customers believe that
Apple’s FBI row was an opportunity missed
owards the end of last year, the FBI locked horns with Apple over the matter of an encrypted iPhone. It belonged to the employer of one of theSan Bernardino killers and, because of an unbelievable cock-up, the FBI had failed
A NUMBER of young technology security companies are losing access to the largest collection of industry analysis of computer viruses, a setback industry experts say will increase exposure to hackers. The policy change at the information-sharing pioneer VirusTotal takes aim