Archive
The malware hinders operations and threatens patient care, making health care facilities and medical centers good targets for criminals. When Hollywood Presbyterian Medical Center admitted in February to paying a $17,000 ransom to decrypt data scrambled by malware, the only
Lawmakers are demanding that the Obama administration comes clean on how many Americans have been caught up in its domestic surveillance programs. Without that information, a bipartisan group of leading lawmakers aren’t able to fully determine what changes need to
Sirin Labs, a new high-end smartphone manufacturer, has raised a $72 million seed round from Singulariteam founder Moshe Hogeg, Kazakh businessman Kenges Rakishev, and the Chinese social networking service Renren to launch a new, secure smartphone. The phone will be revealed in May
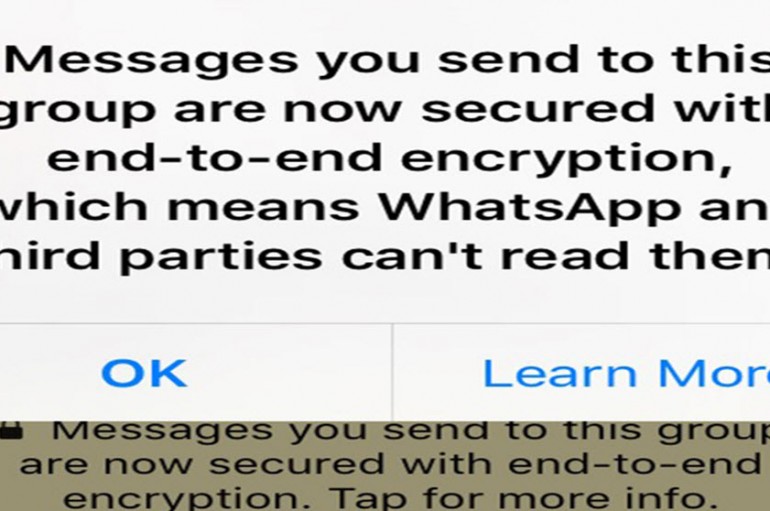
End-to-end encryption has just gone massively mainstream. In an update on March 31st, the Facebook-owned messaging platform WhatsApp quietly pushed an update adding end-to-end encryption enabled by default to its chat and call functionality. They announced the change publicly on Tuesday, allowing the app’s
WhatsApp is, without any doubts, one of the most popular mobile messaging out there, being used by 1 billion people who keep in touch with their friends and families. The application is using the internet connection to send and receive
The U.S. no longer requires Apple’s help to unlock an iPhone 5s phone used by the accused in a drug investigation, stating that an “individual provided the passcode to the iPhone at issue in this case.” The Department of Justice
A new bill will force companies to place a backdoor in their devices to undermine their own encryption
The government wants to access information from digital devices in emergencies and legal investigations. It can’t do that right now because some services (like WhatsApp) and some devices (like iPhones) are encrypted. While terrorists may still be using burner phones, law enforcement
Akamai SIRT (Security Intelligence Response Team) issued yesterday a new threat advisory warning companies that one of Anonymous’ most famous hacktivism campaigns has now changed its MO, with DDoS attacks carried out all over the globe, not just in Japan. OpKillingBay
FBI director James Comey, speaking at the Aspen Security Forum in London today, suggested his agency paid as much as $1.3 million to the as-yet-unnamed private group that hacked into the iPhone of San Bernardino shooter Syed Farook. Comey wouldn’t
Security and hacking conferences provide platforms for cutting edge research into computer vulnerabilities, exploitable systems, and new defensive measures. These often vast events also let researchers and hackers rub shoulders with their friends and peers, network, and blow off steam.
Hackers target India Inc with ransomware, trojan
Mumbai: Indian organisations were the sixth most targeted in Asia, receiving two attacks on an average by cyber criminals, said a report by Symantec. According to latest Internet Security Threat Report, cybercriminals have made an organisational shift and are adopting
When the FBI dropped its case against Apple last month after announcing that it had purchased a hacking solution to get into the locked iPhone belonging to one of the alleged San Bernardino shooters, the bureau wouldn’t say where it
Researchers have uncovered a wide-ranging vulnerability in the way non-Bluetooth dongle devices interact with wireless mice and keypads, which could enable a nearby hacker to take over a victim’s computer using radio frequency signals. According to a white paper from Internet
ADAC Reveals Keyless Entry Systems Vulnerability
After trying out over 20 models with keyless entry from more than 12 different car manufacturers, Germany’s national motoring body, ADAC, found that every single one of them could be opened and stolen within seconds. If that doesn’t send a
Recently it was widely reported that tens of thousands of computers could have been exposed to hacker threat due to malicious online advertisements that ran on major media companies’ websites including the BBC, the New York Times, and MSN. In
As many as 3.2 million computers running unpatched versions of the JBossmiddleware software may be vulnerable to being used as vectors to distribute SamSam and other ransomware, reinforcing the ongoing problem of unpatched systems for enterprises. While scanning for machines