PowerPoint Vulnerability Enables Malware Spreading
Researchers have discovered that cyber attackers are exploiting a vulnerability that allows them to elude antivirus software to deliver malware via Microsoft PowerPoint.
The flaw itself exists in the Windows Object Linking and Embedding (OLE) interface and attackers have previously used it to deliver infected Rich Text File (.RTF) documents. Trend Micro’s researchers noticed that attackers have now infected PowerPoint files to deliver malicious code.
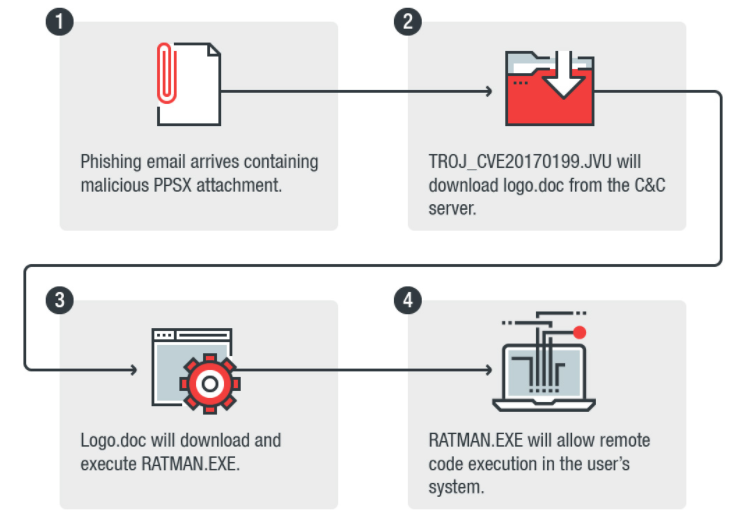
The attacks begin with a spear-phishing email with a message from a cable manufacturing provider. So far, those behind the recent attacks, have targeted organizations that operate in the electronics manufacturing industry with messages that appear to be sent from a business partner related to an order request.
The malicious PowerPoint file is attached to the email and tricks victims into thinking it contains shipping information. When opened, the file triggers an exploit for the CVE-2017-0199 vulnerability which then infects their system. The code is run using PowerPoint’s show animations feature and this allows it to download a file logo document which then executes a file called ‘RATMAN.EXE’ via PowerShell.
Image Credit: Trend Micro
This executable is merely a Trojanized version of the Remcos remote access tool that gives the attackers the ability to keylog, screenlog, tap into the systems microphone and webcam and even download and run other malware. The user’s machine is then under complete control of the attacker often without them even noticing that their device has been compromised.
Microsoft did release patches back in April to address the vulnerability and it is recommended that all users fully update their systems and stay on the lookout for emails similar in nature to the ones used in these attacks.
Source | betanews