Password Reset MITM
Researchers have demonstrated that attackers can set up a malicious website and use users account registration process to successfully perform a password reset process on a number of popular websites and messaging mobile applications.
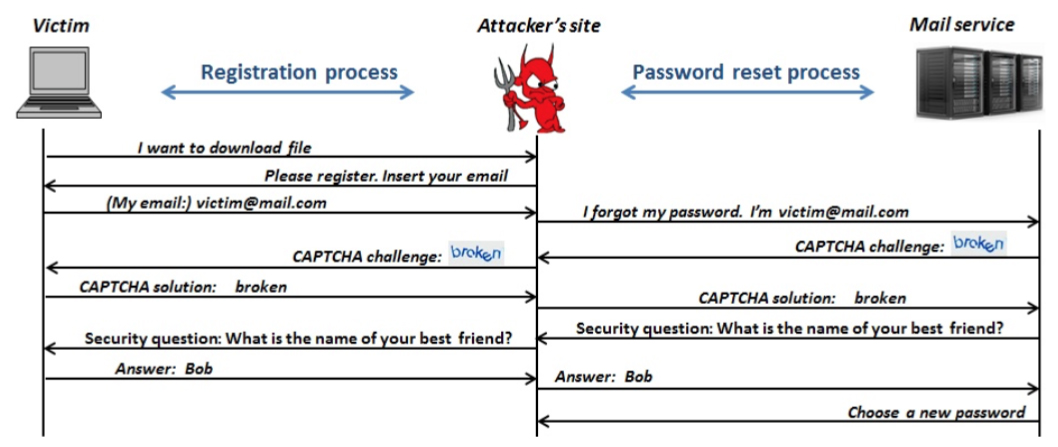
The Password Reset Man in the Middle (PRMITM) attack is here to exploit the registration and password reset processes.
To attack a victim, the attacker only needs to control a website. To entice victims to make an account on the malicious website, the attacker can offer free access to a wanted resource (e.g. free software). Once the user initiates the account registration process by entering their email address, the attacker can use that information to initiate a password reset process on another website that uses that piece of information as the username (e.g. Google, YouTube, Amazon, Twitter, LinkedIn, PayPal, and so on).
Every request for input from that site is forwarded to the potential victim, and then his or her answers forwarded back to that particular site.
In the most basic form (when the password reset request depends on security questions), the attack looks like this:
The attack is also successful if the password reset request depends on an SMS code for confirmation, or a phone code delivering the code.
The potential victim is, along with the email address, asked to input their mobile phone number so that the malicious site can “verify” that they are who they say they are and, in the majority of cases, they fail to find it suspicious that the SMS or phone call is coming from Google, or Facebook, and so on.
Some general guidelines that can be applied to prevent Password Reset MITM attacks, including avoiding relying on security questions, restricting the validity of the reset code to a short time, notifying users by email and phone when a password reset request is sent, not sending a code but a link, and adding interactivity to the phone call so that users are forced to listen to the message and understand what they are doing.
Source | helpnetsec