INDUSTROYER AND CRASHOVERRIDE
In December 2016, the capital of Ukraine, Kiev was a victim of a power grid hack that blacked out the entire capital for several hours thus showing of what skillful hackers can do to damage critical infrastructure.
A Slovakia-based anti-virus software outfit ESET and American firm Dragos that deals with critical infrastructure security have claimed to identify the malware that caused the power outage.
The malware is known as Industroyer and Crash Override, and the malware cannot only be manipulated to take out power supply operations but also water and gas systems, and transportation networks. Although the malware does exploit any zero-day software vulnerabilities but can damage critical infrastructure.
“The malware is really easy to re-purpose and use against other targets. That is definitely alarming,” said by ESET malware researcher Robert Lipovsky in a telephone interview. “This could cause wide-scale damage to infrastructure systems that are vital.”
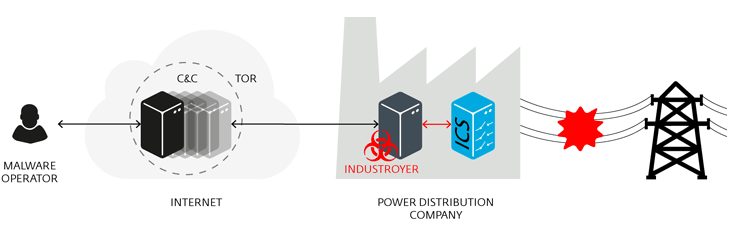
Crash Override can control electrical substation switches and circuit breakers where the attacker can just turn off the power distribution.
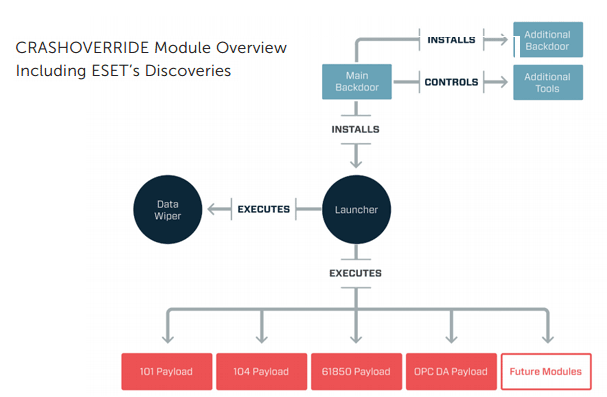
Industroyer, on the other hand, acts as a backdoor that installs four payload components so that taking control of switches and breakers can be done and then connects to a remote command-and-control server to receive commands from the attackers.
The four malware that have been successful in attacking industrial control systems include Stuxnet, Havex, BlackEnerggy and Crash Override. Stuxnet and Crash override are for sabotaging purposes, while BlackEnergy and Havex are known for conducting espionage.
Analysis of the malware
Crash Override analysis show that the power outages can be affected on a larger scale and can be long lasting than what Ukraine suffered.
Dragos CEO claims that the malware can affect the power distribution for days in portions of the countrys electric grid but cannot bring down the entire grid of the country.
Crash Override can be altered to different power utilities with the help of its interchangeable plug-ins components or can be also launch attacks on multiple targets.
Dragos provides a detailed analysis of the malware.
The security firms have already warned government authorities and power grid companies about the malware and have also advised them of how to defend against the threat.
Source: http://thehackernews.com/2017/06/electric-power-grid-malware.html