Archive
A Canadian hospital’s website has been hacked in order to serve up the notorious Teslacrypt ransomware to unsuspecting visitors. Jérôme Segura, a senior security researcher at Malwarebytes, explains in a blog postthat out-of-date server-side software is likely to blame for
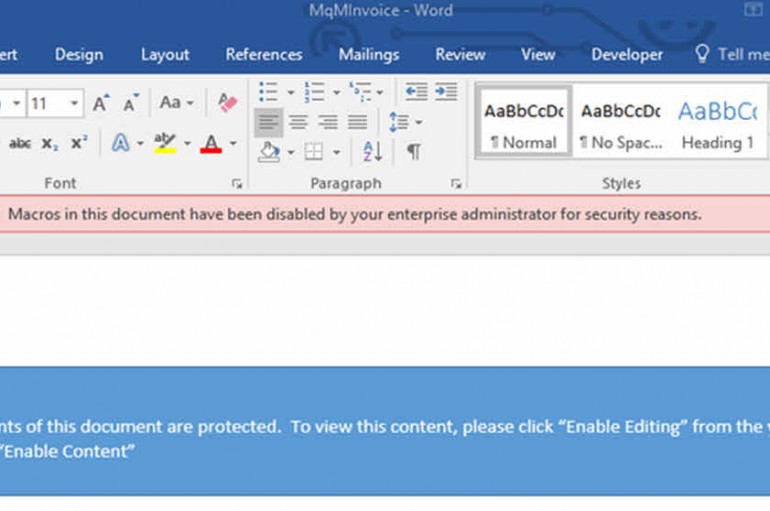
With macro-based malware infections on the rise, Microsoft has launched a new Office 2016 feature that can help enterprise admins neuter the threat. Macros are disabled by default in Word, Excel and PowerPoint but attackers behind the banking malware Dridex
The ripple effects of Donald Trump’s presidential candidacy have led to a civil war in the Republican party. But they have also had the unexpected consequence of leading to a subterranean civil war within Anonymous, the mysterious hacking collective. Most
A new USB-based malware has been identified which has unusual powers to evade detection, and which can also leverage the mobility of ‘portable’ applications such as ‘standalone’ versions of Firefox Portable, Notepad++ and TrueCrypt. The malware, called Win32/PSW.Stealer.NAI or ‘USB
The Justice Department will unveil indictments against hackers linked to the Iranian government Thursday for infiltrating U.S. critical infrastructure, according to a person familiar with the matter. The indictments will include charges for a 2013 cyberattack on the Bowman Avenue Dam,
Top Of The Order: So, That’s Why…: Earlier this week, the court fight between the FBI and Apple was put on hold when the law-enforcement agency said it might not need Apple’s help to get into the iPhone that belonged to
nald Trump smelled blood and took the bait. The Anonymous hacking community set up a tidy little trap for Trump, his presidential campaign staff, the Secret Service, and the FBI — and they all fell for it. On Friday, Anonymous
A researcher with RSA says faulty firmware found in security cameras sold by at least 70 vendors may be a contributor to many of the credit card breaches that have proved costly to retailers. Rotem Kerner based his research on a
Yesterday, an Israeli judge at the Beersheba District Court in Israel indicted Maagad Ben Juwad Oydeh, a Palestinian known as the main hacking expert for the Palestinian Islamic Jihad (PIJ) movement. Israeli forces arrested Oydeh at the start of the
The supreme court has rejected a challenge by the publisher of the Daily and Sunday Mirror against the landmark £1.2m in damages awarded to eight phone-hacking victims, including actor Sadie Frost and ex-footballer Paul Gascoigne. Mirror Group Newspapers took its
Earlier this month, digital rights group the Electronic Frontier Foundation (EFF) filed a strongly worded amicus brief arguing that the warrant used by the FBI for its use of malware to identify visitors of a dark web child pornography site
Hackers hijacking water treatment plant controls shows how easily civilians could be poisoned
A group of hackers managed to infiltrate a water treatment plant and change the levels of chemicals being used to treat tap water four times during the cyberattack, security researchers report. The potential trouble caused by hacking critical infrastructure has
A businessman from China pleaded guilty on Wednesday to conspiring to hack into the computer networks of major U.S. defense contractors including Boeing, the U.S. Department of Justice said in a statement. Su Bin, 50, faces a maximum five-year sentence
Tomáš Gardoň, a malware analyst at ESET, explains to We Live Security why a trojan, detected by ESET as Win32/PSW.Stealer.NAI – and dubbed USB Thief – is worth knowing about. “The USB Thief is, in many aspects different from the
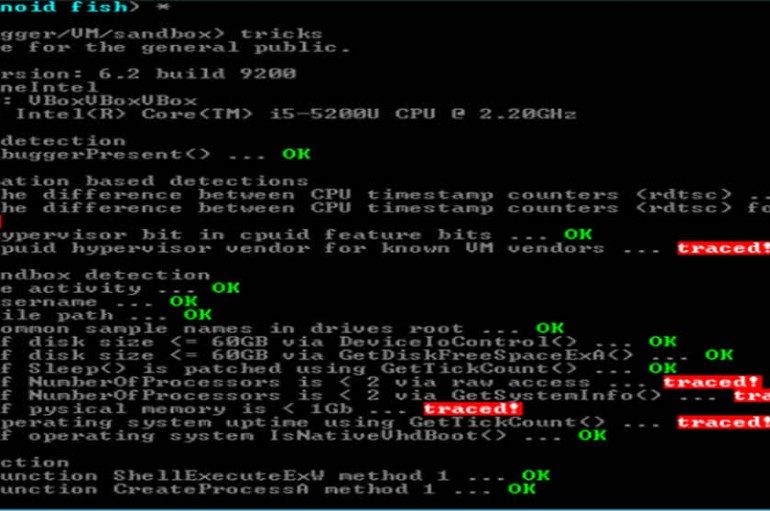
If you think an application is suspicious, then you might run it in a sandbox, a virtual machine, maybe use a debugger, and watch what it does. And if nothing happens then that means it’s safe. Right? Well, maybe not.
Amazon Web Services (AWS) has released an encryption SDK to help developers build applications that correctly implement encryption and thus ensure that data is kept as secure as possible in the AWS cloud. Available now, the AWS Encryption SDK is