Updated Rakhni malware strain can be ransomware or a cryptominer
The five-year-old Trojan-Ransom.Win32.Rakhni family has received a facelift that now allows it to decide whether or not to install its traditional ransomware or to drop a cryptominer instead.
For the most part the injection chain remains unchanged, Kaspersky Labs reported. However, the malware moves along a rather complicated path before it decides which form it will take. During the process it will check to make sure the device is not a virtual machine, it will check for and disarm an AV software and also Widows Defender and finally erase most of the footprints made during the malware installation.
The malware is delivered through spam campaigns where the email comes with a PDF attached which the receiver is prompted to save and then enable editing. When the victim attempts to open the document he or she is presented with an executable that portrays itself as an Adobe Reader plugin and it asks the person to allow it to make changes to their computer.
The executable, which is written in Delphi and has its strings encrypted, then presents a message box that states the PDF could not be opened, basically to keep the victim from thinking anything negative is about to happen.
The malware then starts to move through a decision chain that will eventually lead it to deciding what to drop onto the device.
It first checks that the device has one of the substrings:
· \TEMP
· \TMP
· \STARTUP
· \CONTENT.IE
· Registry check
It then checks to see if the registry contains Checks that in the registry there is no value HKCU\Software\Adobe\DAVersion and if it finds this is so it creates HKCU\Software\Adobe\DAVersion = True.
The next stop is to check that at least 26 process are running, but it also compares these to a rather long list of process that if detected will stop the installation.
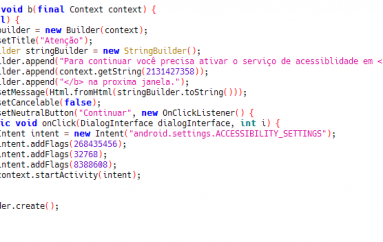
It checks to see if the device under attack is a virtual machine, installs fake root certificates and then it searches for a specific folder, %AppData%\Bitcoin, before it makes its final decision on what to drop.
“If the folder exists, the downloader decides to download the cryptor. If the folder doesn’t exist and the machine has more than two logical processors, the miner will be downloaded. If there’s no folder and just one logical processor, the downloader jumps to its worm component, which is described below in the corresponding part of the article,” Kaspersky wrote.
The malware makes on final deposit into the target machine. It pushes a worm and tries to copy itself to other computers on the local network.
Source | scmagazine