Two-Thirds of Hotel Sites Leak User Data
Two-thirds of hotel booking sites are leaking customers’ booking reference codes to third parties, potentially exposing their personal data to malicious insiders, according to Norton.
The Symantec company’s principal threat researcher, Candid Wueest, claimed 67% of the more than 1500 hotels in 54 countries he tried were affected by this issue, putting data such as name, email and postal address, mobile phone number and passport number at risk.
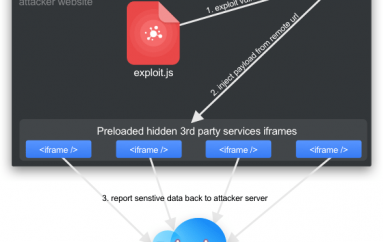
In over half of the cases (57%) it would be even easier for a third-party to access this information as the sites sent a confirmation email to the guest with a direct link to their booking — no log-in required.
Hotels shared the booking reference code with as many as 30 third parties on average, including social networks, search engines and ad and analytics firms.
“There are other scenarios in which the booking data may also be leaked. Some sites pass on the information during the booking process, while others leak it when the customer manually logs into the website. Others generate an access token, which is then passed in the URL instead of the credentials, which is not good practice either,” Wueest explained.
“In most cases, I found that the booking data remains visible, even if the reservation has been cancelled, granting an attacker a large window of opportunity to steal personal information.”
Other security errors included 29% of the sites studied failing to encrypt the booking reference link, meaning an attacker could intercept user credentials to view details or amend the booking, if they’re on public Wi-Fi or similar.
Wueest also claimed “multiple sites” had no protections in place against brute forcing of the booking reference or enumeration attacks.
Stolen data could be used to commit identity theft, launch convincing phishing or extortion attacks, or even to monitor high profile business and government employees, he warned.
Disappointingly, a quarter of data protection officers contacted about the privacy snafu failed to respond within six weeks, despite the threat of GDPR fines.
This post Two-Thirds of Hotel Sites Leak User Data originally appeared on InfoSecurity Magazine.