Talos Experts Found a Critical RCE in GoAhead Web Server
Experts at Cisco Talos found two vulnerabilities in the GoAhead embedded web server, including a critical remote code execution flaw.
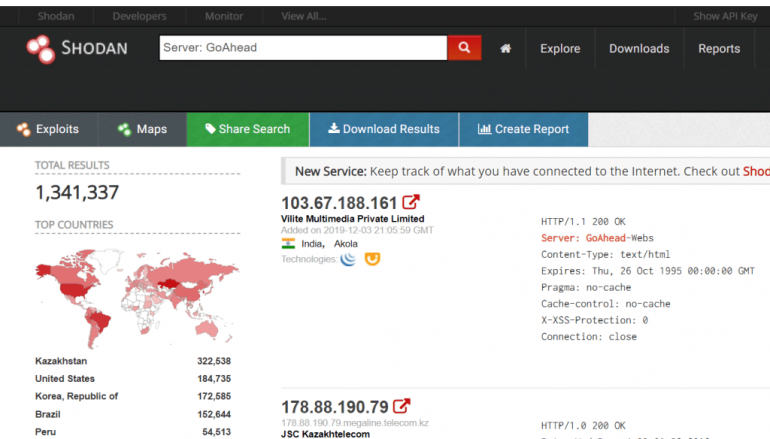
GoAhead is the world’s most popular, tiny embedded web server. It is developed by EmbedThis that defines it as compact, secure and simple to use. GoAhead is deployed in hundreds of millions of devices and is ideal for the smallest of embedded devices. Searching for GoAhead installs exposed online with Shodan search engine, at the time of writing there are over 1.3 million installs.

The first vulnerability, tracked as CVE-2019-5096, is related to how multi-part/form-data requests are processed. The flaw could be exploited by an unauthenticated attacker to trigger a use-after-free condition and execute arbitrary code on the server by sending specially crafted HTTP requests.
“An exploitable code execution vulnerability exists in the processing of multi-part/form-data requests within the base GoAhead web server application in versions v5.0.1, v.4.1.1 and v3.6.5. A specially crafted HTTP request can lead to a use-after-free condition during the processing of this request that can be used to corrupt heap structures that could lead to full code execution.” reads the security advisory published by Talos. “The request can be unauthenticated in the form of GET or POST requests, and does not require the requested resource to exist on the server.”
The security flaw has been assigned a CVSS score of 9.8.
The second vulnerability in the GoAhead web server found by Talos, tracked as CVE-2019-5097, can be exploited by an unauthenticated attacker to cause a denial-of-service (DoS) condition by sending specially crafted HTTP requests.
“A denial-of-service vulnerability exists in the processing of multi-part/form-data requests in the base GoAhead web server application in versions v5.0.1, v.4.1.1 and v3.6.5. A specially crafted HTTP request can lead to an infinite loop in the process.” continues the post. “The request can be unauthenticated in the form of GET or POST requests and does not require the requested resource to exist on the server.”
According to Talos, GoAhead versions 5.0.1, 4.1.1 and 3.6.5 are affected by the two vulnerabilities. Talos reported the flaws to EmbedThis in August, and the vendor addressed them on November 21.
In December 2017, experts from Elttam discovered a flaw in GoAhead tiny web server, tracked as CVE-2017-17562, that affects hundreds of thousands IoT devices. The flaw could be exploited to remotely execute malicious code on affected devices.
This post Talos Experts Found a Critical RCE in GoAhead Web Server originally appeared on Security Affairs.