Symantec Shared Details of North Korean Lazarus’s FastCash Trojan Used to Hack Banks
North Korea-linked Lazarus Group has been using FastCash Trojan to compromise AIX servers to empty tens of millions of dollars from ATMs.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
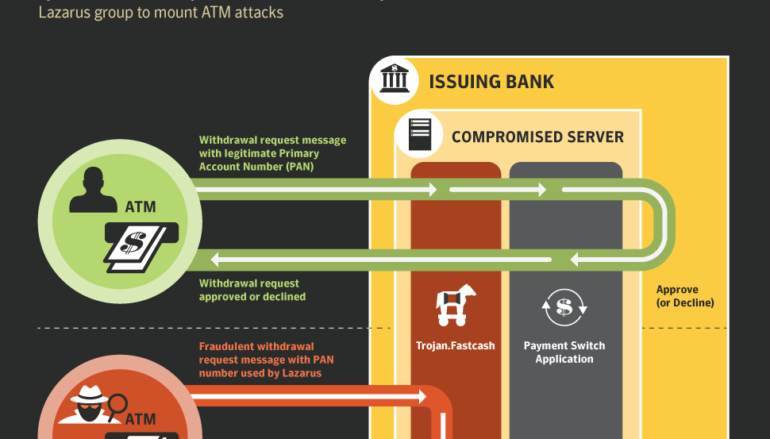
Following the above alert, Symantec uncovered the malware used in the FastCash scheme that was designed to intercept and approve fraudulent ATM cash withdrawal requests and send fake approval responses.
“Following US-CERT’s report, Symantec’s research uncovered the key component used in the group’s recent wave of financial attacks. The operation, known as “FASTCash“, has enabled Lazarus to fraudulently empty ATMs of cash. To make the fraudulent withdrawals, Lazarus first breaches targeted banks’ networks and compromises the switch application servers handling ATM transactions.” reads the analysis published by Symantec.
“Once these servers are compromised, previously unknown malware (Trojan.Fastcash) is deployed. This malware in turn intercepts fraudulent Lazarus cash withdrawal requests and sends fake approval responses, allowing the attackers to steal cash from ATMs.”
The malicious code was specifically designed to be injected into a legitimate process on application servers running the IBM’s AIX operating system. Symantec discovered that all the switch application servers targeted by the Lazarus APT Group were running unsupported versions of the AIX OS.
The hackers inject a malicious Advanced Interactive eXecutive (AIX) executable, tracked as Trojan.Fastcash, into a network handling ATM transactions. The malware is able to forgefraudulent ISO 8583 messages, where the ISO 8583 is the standard for financial transaction messaging.
Trojan.Fastcash has two primary functions:
- It monitors incoming messages and intercepts attacker-generated fraudulent transaction requests to prevent them from reaching the switch application that processes transactions.
- It contains logic that generates one of three fraudulent responses to fraudulent transaction requests.
Trojan.Fastcash will read all incoming network traffic, scanning for incoming ISO 8583 request messages, and when a Primary Account Number (PAN) used by the attackers is detected the malware will attempt to modify these messages.
The messages are modified depending on each victim organization, the malicious code will generate a fake response message approving fraudulent withdrawal requests. In this way, the hackers get the attempts to withdraw money via an ATM approved.
Symantec has discovered multiple versions of the FastCash Trojan that implement a different response logic tailored for a specific transaction processing network.
Further details, including IoCs, are reported in the analysis published by Symantec.
This post Symantec Shared Details of North Korean Lazarus’s FastCash Trojan Used to Hack Banks originally appeared on Security Affairs.






