SWEED Targets Precision Engineering Companies in Italy
Introduction
Today I’d like to share a quick analysis of an interesting attack targeting precision engineering companies based in Italy. Precision engineering is a very important business market in Europe, it includes developing mechanical equipment for: automotive, railways, heavy industries and military grade technology . The attacker pretended to be a customer and sent to the victim a well crafted email containing a Microsoft XLS file including real spear-parts codes, quantities and shipping addresses. A very similar attack schema to MartyMCFly campaign.
Technical Analysis
Hash 863934c1fa4378799ed0c3e353603ba0bee3a357a5c63d845fe0d7f4ebc1a64c
Threat Microsoft Excel Document
Brief Description Exploiter, Dropper and Executor targeting precision engineering companies
Ssdeep 384:janC18qmTUKhKVxbo6JpM2gwmeJxQrHwFeDtug/uND40C2D:janCOqm4tVxE6rM2g0fO2exuxC0FD
On 2019-10-26 a well-crafted email coming from
steel@vardhman.com
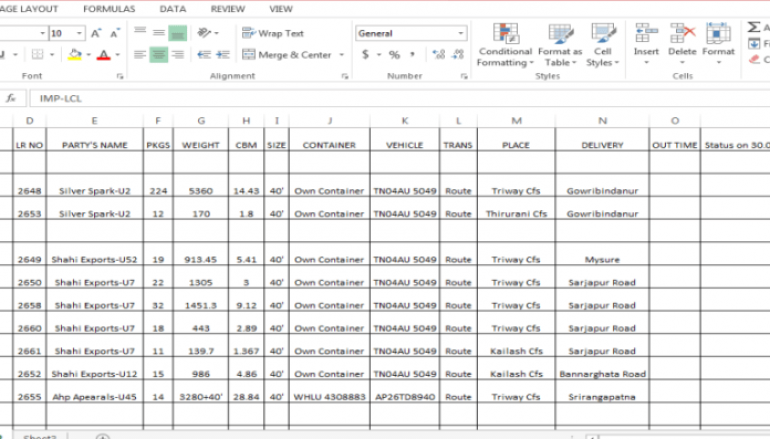
asking for an economic proposal reached specific email boxes belonging to purchasing department of a well-known precision engineering company. Basically the attacker asks to the victims to quote the entire list of spear-parts included in an attached Excel document. The source address looks like genuine since belonging to a big company working in the textile field which frequently uses precision equipment machines in its production chain.
Once the victim opens up the document it would actually see a “looking real” Microsoft Excel spreadsheet. Surprisingly the spreadsheet doesn’t hold Macro code, so no weird message would appear and no weird requests for enabling macros or compatibility-mode would appear on the victim screen. Everything looks like real except for the third object included into the Excel file.
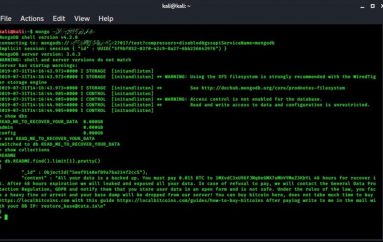
If you are familiar with CVE-2017-11882, you might notice it immediately, but if you aren’t you might take a look to HERE (for the exploit generation) to HERE (for an example) and HERE (for CVE original disclosure). In a nutshell CVE-2017-11882 is a 17-year old memory corruption issue in Microsoft Office (including Office 360). When exploited successfully, it can let attackers execute remote code on a vulnerable machine—even without user interaction—after a malicious document is opened. The flaw resides within Equation Editor (EQNEDT32.EXE), a component in Microsoft Office that inserts or edits Object Linking and Embedding (OLE) objects in documents.
Once the victim opens the document apparently nothing happens but silently Object3 runs EquationEditor and exploits a memory corruption vulnerability executing code on the running host.
This post SWEED Targets Precision Engineering Companies in Italy originally appeared on Security Affairs.