SamSam Ransomware Attacks Extorted Nearly $6 Million
Ransomware has become a multimillion-dollar black market business for cybercriminals, and SamSam being a great example.
New research revealed that the SamSam ransomware had extorted nearly $6 million from its victims since December 2015, when the cyber gang behind the ransomware started distributing the malware in the wild.
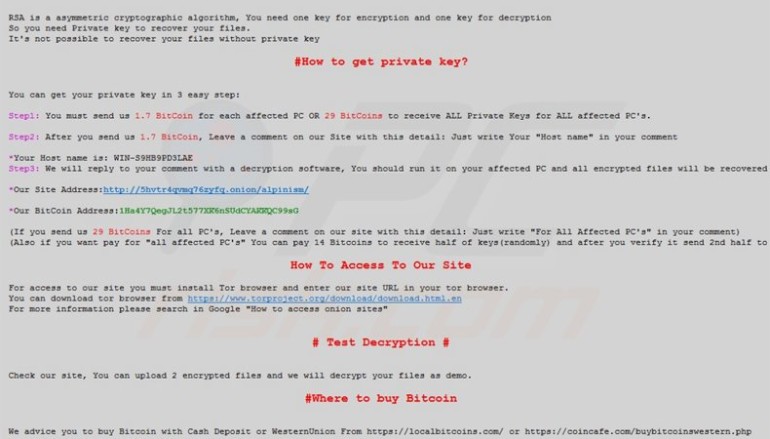
Researchers at Sophos have tracked Bitcoin addresses owned by the attackers mentioned on ransom notes of each SamSam version and found the attackers have received more than $5.9 million from just 233 victims, and their profits are still on the rise, netting around $300,000 per month.
“In total, we have now identified 157 unique addresses which have received ransom payments as well as 89 addresses which have been used on ransom notes and sample files but, to date, have not received payments,” the new report by Sophos reads.
What makes SamSam stand out from other forms of ransomware is that SamSam is not distributed in an unplanned way via spam email campaigns; instead, attackers choose potential targets and infect systems manually.
Attackers first compromise the RDP on a targeted system—either by conducting brute force attack or using stolen credentials purchased from the dark web—and then attempt to strategically deploy SamSam ransomware throughout the network by exploiting vulnerabilities in other systems.
Unlike other well-known ransomware like WannaCry and NotPetya, SamSam does not include any worm-like or virus capabilities to spread by itself. Instead, the ransomware relies on the human attacker to spread it.
Source | thehackernews